Django registration and authentication with GraphQL.
Abstract all the basic logic of handling user accounts out of your app, so you don't need to think about it and can get up and running faster.
No lock-in. When you are ready to implement your own code or this package is not up to your expectations , it's easy to extend or switch to your implementation.
Documentation is available at read the docs.
- Awesome docs 🎉
- Fully compatible with Relay
- Works with default or custom user model
- JWT authentication (with Django GraphQL JWT)
- User query with filters (with Django Filter and Graphene Django)
- User registration with email verification
- Add secondary email, with email verification too
- Resend activation email
- Retrieve/Update user
- Archive user
- Permanently delete user or make it inactive
- Turn archived user active again on login
- Track user status (archived, verified, secondary email)
- Password change
- Password reset through email
- Revoke user refresh tokens on account archive/delete/password change/reset
- All mutations return
successanderrors - Default email templates (you will customize though)
- Customizable, no lock-in
import graphene
from graphql_auth.schema import UserQuery, MeQuery
from graphql_auth import mutations
class AuthMutation(graphene.ObjectType):
register = mutations.Register.Field()
verify_account = mutations.VerifyAccount.Field()
resend_activation_email = mutations.ResendActivationEmail.Field()
send_password_reset_email = mutations.SendPasswordResetEmail.Field()
password_reset = mutations.PasswordReset.Field()
password_set = mutations.PasswordSet.Field() # For passwordless registration
password_change = mutations.PasswordChange.Field()
update_account = mutations.UpdateAccount.Field()
archive_account = mutations.ArchiveAccount.Field()
delete_account = mutations.DeleteAccount.Field()
send_secondary_email_activation = mutations.SendSecondaryEmailActivation.Field()
verify_secondary_email = mutations.VerifySecondaryEmail.Field()
swap_emails = mutations.SwapEmails.Field()
remove_secondary_email = mutations.RemoveSecondaryEmail.Field()
# django-graphql-jwt inheritances
token_auth = mutations.ObtainJSONWebToken.Field()
verify_token = mutations.VerifyToken.Field()
refresh_token = mutations.RefreshToken.Field()
revoke_token = mutations.RevokeToken.Field()
class Query(UserQuery, MeQuery, graphene.ObjectType):
pass
class Mutation(AuthMutation, graphene.ObjectType):
pass
schema = graphene.Schema(query=Query, mutation=Mutation)Import mutations from the relay module:
from graphql_auth import relay
class AuthMutation(graphene.ObjectType):
register = relay.Register.Field()
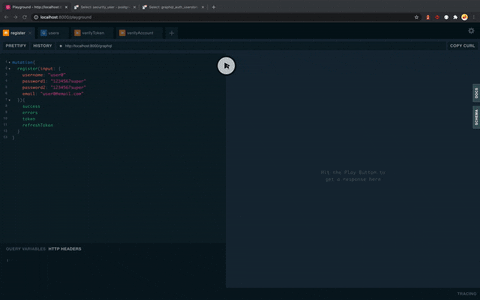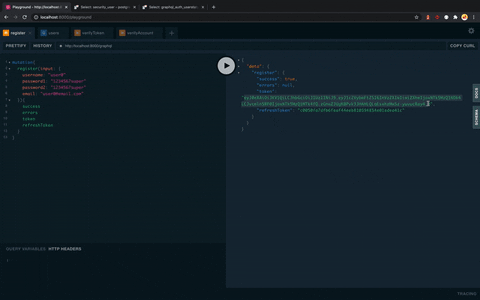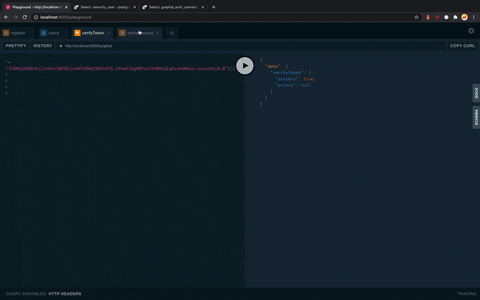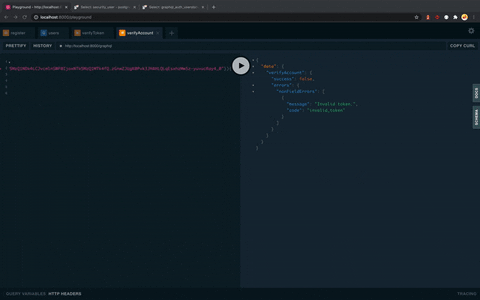
# ...Handling user accounts becomes super easy.
mutation {
register(
email: "[email protected]",
username: "new_user",
password1: "123456super",
password2: "123456super",
) {
success,
errors,
token,
refreshToken
}
}Check the status of the new user:
u = UserModel.objects.last()
u.status.verified
# FalseDuring the registration, an email with a verification link was sent.
mutation {
verifyAccount(
token:"<TOKEN ON EMAIL LINK>",
) {
success,
errors
}
}Now user is verified.
u.status.verified
# TrueCheck the installation guide or jump to the quickstart. Or if you prefer, browse the api.
See CONTRIBUTING.md