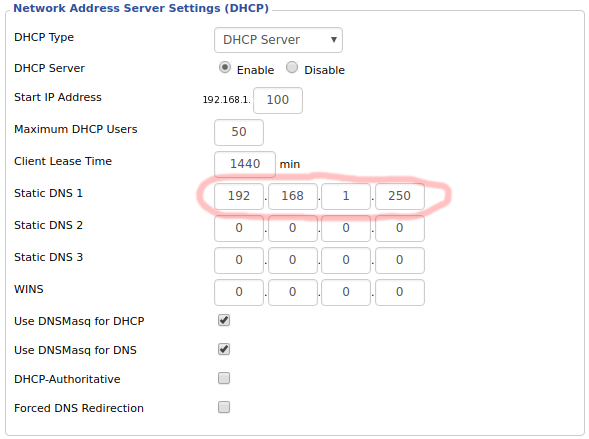
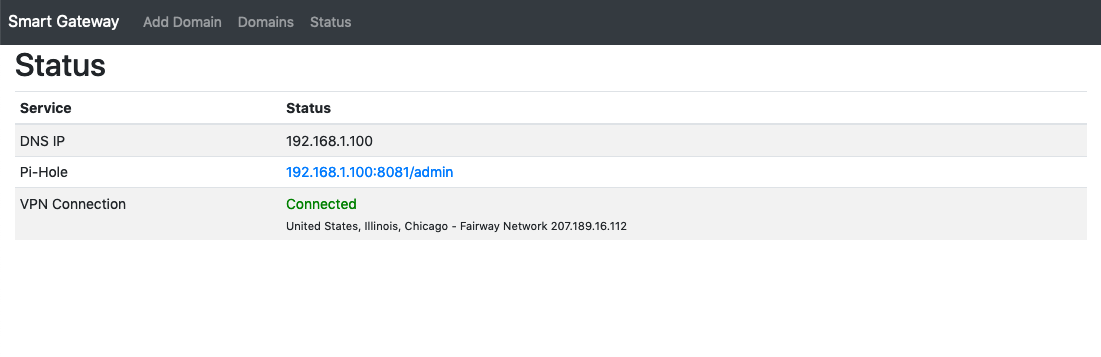
hello please help me i am facing vpn auth error . i also give the accurate username and password of nord vpn but same error.

sniproxyvpn | Mon Nov 9 17:30:31 2020 WARNING: --ping should normally be used with --ping-restart or --ping-exit
sniproxyvpn | Mon Nov 9 17:30:31 2020 TCP/UDP: Preserving recently used remote address: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:30:31 2020 Socket Buffers: R=[212992->212992] S=[212992->212992]
sniproxyvpn | Mon Nov 9 17:30:31 2020 UDP link local: (not bound)
sniproxyvpn | Mon Nov 9 17:30:31 2020 UDP link remote: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:30:31 2020 TLS: Initial packet from [AF_INET]92.119.17.3:1194, sid=3098b842 52d3123a
sniproxyvpn | Mon Nov 9 17:30:31 2020 VERIFY OK: depth=1, C=PA, O=NordVPN, CN=NordVPN CA5
sniproxyvpn | Mon Nov 9 17:30:31 2020 VERIFY KU OK
sniproxyvpn | Mon Nov 9 17:30:31 2020 Validating certificate extended key usage
sniproxyvpn | Mon Nov 9 17:30:31 2020 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
sniproxyvpn | Mon Nov 9 17:30:31 2020 VERIFY EKU OK
sniproxyvpn | Mon Nov 9 17:30:31 2020 VERIFY OK: depth=0, CN=us8028.nordvpn.com
sniproxyvpn | Mon Nov 9 17:30:33 2020 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
sniproxyvpn | Mon Nov 9 17:30:33 2020 [us8028.nordvpn.com] Peer Connection Initiated with [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:30:34 2020 SENT CONTROL [us8028.nordvpn.com]: 'PUSH_REQUEST' (status=1)
sniproxyvpn | Mon Nov 9 17:30:34 2020 AUTH: Received control message: AUTH_FAILED
sniproxyvpn | Mon Nov 9 17:30:34 2020 SIGUSR1[soft,auth-failure] received, process restarting
sniproxyvpn | Mon Nov 9 17:30:34 2020 Restart pause, 10 second(s)
sniproxyvpn | Mon Nov 9 17:30:44 2020 WARNING: --ping should normally be used with --ping-restart or --ping-exit
sniproxyvpn | Mon Nov 9 17:30:44 2020 TCP/UDP: Preserving recently used remote address: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:30:44 2020 Socket Buffers: R=[212992->212992] S=[212992->212992]
sniproxyvpn | Mon Nov 9 17:30:44 2020 UDP link local: (not bound)
sniproxyvpn | Mon Nov 9 17:30:44 2020 UDP link remote: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:30:44 2020 TLS: Initial packet from [AF_INET]92.119.17.3:1194, sid=00963317 e2f389a4
sniproxyvpn | Mon Nov 9 17:30:44 2020 VERIFY OK: depth=1, C=PA, O=NordVPN, CN=NordVPN CA5
sniproxyvpn | Mon Nov 9 17:30:44 2020 VERIFY KU OK
sniproxyvpn | Mon Nov 9 17:30:44 2020 Validating certificate extended key usage
sniproxyvpn | Mon Nov 9 17:30:44 2020 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
sniproxyvpn | Mon Nov 9 17:30:44 2020 VERIFY EKU OK
sniproxyvpn | Mon Nov 9 17:30:44 2020 VERIFY OK: depth=0, CN=us8028.nordvpn.com
sniproxyvpn | Mon Nov 9 17:30:46 2020 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
sniproxyvpn | Mon Nov 9 17:30:46 2020 [us8028.nordvpn.com] Peer Connection Initiated with [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:30:48 2020 SENT CONTROL [us8028.nordvpn.com]: 'PUSH_REQUEST' (status=1)
sniproxyvpn | Mon Nov 9 17:30:48 2020 AUTH: Received control message: AUTH_FAILED
sniproxyvpn | Mon Nov 9 17:30:48 2020 SIGUSR1[soft,auth-failure] received, process restarting
sniproxyvpn | Mon Nov 9 17:30:48 2020 Restart pause, 10 second(s)
sniproxyvpn | Mon Nov 9 17:30:58 2020 WARNING: --ping should normally be used with --ping-restart or --ping-exit
sniproxyvpn | Mon Nov 9 17:30:58 2020 TCP/UDP: Preserving recently used remote address: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:30:58 2020 Socket Buffers: R=[212992->212992] S=[212992->212992]
sniproxyvpn | Mon Nov 9 17:30:58 2020 UDP link local: (not bound)
sniproxyvpn | Mon Nov 9 17:30:58 2020 UDP link remote: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:30:58 2020 TLS: Initial packet from [AF_INET]92.119.17.3:1194, sid=d03f9126 ae2beeac
sniproxyvpn | Mon Nov 9 17:30:58 2020 VERIFY OK: depth=1, C=PA, O=NordVPN, CN=NordVPN CA5
sniproxyvpn | Mon Nov 9 17:30:58 2020 VERIFY KU OK
sniproxyvpn | Mon Nov 9 17:30:58 2020 Validating certificate extended key usage
sniproxyvpn | Mon Nov 9 17:30:58 2020 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
sniproxyvpn | Mon Nov 9 17:30:58 2020 VERIFY EKU OK
sniproxyvpn | Mon Nov 9 17:30:58 2020 VERIFY OK: depth=0, CN=us8028.nordvpn.com
sniproxyvpn | Mon Nov 9 17:31:00 2020 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
sniproxyvpn | Mon Nov 9 17:31:00 2020 [us8028.nordvpn.com] Peer Connection Initiated with [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:31:01 2020 SENT CONTROL [us8028.nordvpn.com]: 'PUSH_REQUEST' (status=1)
sniproxyvpn | Mon Nov 9 17:31:01 2020 AUTH: Received control message: AUTH_FAILED
sniproxyvpn | Mon Nov 9 17:31:01 2020 SIGUSR1[soft,auth-failure] received, process restarting
sniproxyvpn | Mon Nov 9 17:31:01 2020 Restart pause, 10 second(s)
sniproxyvpn | Mon Nov 9 17:31:11 2020 WARNING: --ping should normally be used with --ping-restart or --ping-exit
sniproxyvpn | Mon Nov 9 17:31:11 2020 TCP/UDP: Preserving recently used remote address: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:31:11 2020 Socket Buffers: R=[212992->212992] S=[212992->212992]
sniproxyvpn | Mon Nov 9 17:31:11 2020 UDP link local: (not bound)
sniproxyvpn | Mon Nov 9 17:31:11 2020 UDP link remote: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:31:11 2020 TLS: Initial packet from [AF_INET]92.119.17.3:1194, sid=59902c7a 01d1944d
sniproxyvpn | Mon Nov 9 17:31:11 2020 VERIFY OK: depth=1, C=PA, O=NordVPN, CN=NordVPN CA5
sniproxyvpn | Mon Nov 9 17:31:11 2020 VERIFY KU OK
sniproxyvpn | Mon Nov 9 17:31:11 2020 Validating certificate extended key usage
sniproxyvpn | Mon Nov 9 17:31:11 2020 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
sniproxyvpn | Mon Nov 9 17:31:11 2020 VERIFY EKU OK
sniproxyvpn | Mon Nov 9 17:31:11 2020 VERIFY OK: depth=0, CN=us8028.nordvpn.com
sniproxyvpn | Mon Nov 9 17:31:13 2020 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
sniproxyvpn | Mon Nov 9 17:31:13 2020 [us8028.nordvpn.com] Peer Connection Initiated with [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:31:15 2020 SENT CONTROL [us8028.nordvpn.com]: 'PUSH_REQUEST' (status=1)
sniproxyvpn | Mon Nov 9 17:31:15 2020 AUTH: Received control message: AUTH_FAILED
sniproxyvpn | Mon Nov 9 17:31:15 2020 SIGUSR1[soft,auth-failure] received, process restarting
sniproxyvpn | Mon Nov 9 17:31:15 2020 Restart pause, 10 second(s)
sniproxyvpn | Mon Nov 9 17:31:25 2020 WARNING: --ping should normally be used with --ping-restart or --ping-exit
sniproxyvpn | Mon Nov 9 17:31:25 2020 TCP/UDP: Preserving recently used remote address: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:31:25 2020 Socket Buffers: R=[212992->212992] S=[212992->212992]
sniproxyvpn | Mon Nov 9 17:31:25 2020 UDP link local: (not bound)
sniproxyvpn | Mon Nov 9 17:31:25 2020 UDP link remote: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:31:25 2020 TLS: Initial packet from [AF_INET]92.119.17.3:1194, sid=bd79d468 0e93f1a5
sniproxyvpn | Mon Nov 9 17:31:25 2020 VERIFY OK: depth=1, C=PA, O=NordVPN, CN=NordVPN CA5
sniproxyvpn | Mon Nov 9 17:31:25 2020 VERIFY KU OK
sniproxyvpn | Mon Nov 9 17:31:25 2020 Validating certificate extended key usage
sniproxyvpn | Mon Nov 9 17:31:25 2020 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
sniproxyvpn | Mon Nov 9 17:31:25 2020 VERIFY EKU OK
sniproxyvpn | Mon Nov 9 17:31:25 2020 VERIFY OK: depth=0, CN=us8028.nordvpn.com
sniproxyvpn | Mon Nov 9 17:31:27 2020 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
sniproxyvpn | Mon Nov 9 17:31:27 2020 [us8028.nordvpn.com] Peer Connection Initiated with [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:31:28 2020 SENT CONTROL [us8028.nordvpn.com]: 'PUSH_REQUEST' (status=1)
sniproxyvpn | Mon Nov 9 17:31:28 2020 AUTH: Received control message: AUTH_FAILED
sniproxyvpn | Mon Nov 9 17:31:28 2020 SIGUSR1[soft,auth-failure] received, process restarting
sniproxyvpn | Mon Nov 9 17:31:28 2020 Restart pause, 10 second(s)
sniproxyvpn | Mon Nov 9 17:31:38 2020 WARNING: --ping should normally be used with --ping-restart or --ping-exit
sniproxyvpn | Mon Nov 9 17:31:38 2020 TCP/UDP: Preserving recently used remote address: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:31:38 2020 Socket Buffers: R=[212992->212992] S=[212992->212992]
sniproxyvpn | Mon Nov 9 17:31:38 2020 UDP link local: (not bound)
sniproxyvpn | Mon Nov 9 17:31:38 2020 UDP link remote: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:31:38 2020 TLS: Initial packet from [AF_INET]92.119.17.3:1194, sid=329df2c6 d6676ec1
sniproxyvpn | Mon Nov 9 17:31:38 2020 VERIFY OK: depth=1, C=PA, O=NordVPN, CN=NordVPN CA5
sniproxyvpn | Mon Nov 9 17:31:38 2020 VERIFY KU OK
sniproxyvpn | Mon Nov 9 17:31:38 2020 Validating certificate extended key usage
sniproxyvpn | Mon Nov 9 17:31:38 2020 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
sniproxyvpn | Mon Nov 9 17:31:38 2020 VERIFY EKU OK
sniproxyvpn | Mon Nov 9 17:31:38 2020 VERIFY OK: depth=0, CN=us8028.nordvpn.com
sniproxyvpn | Mon Nov 9 17:31:40 2020 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
sniproxyvpn | Mon Nov 9 17:31:40 2020 [us8028.nordvpn.com] Peer Connection Initiated with [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:31:41 2020 SENT CONTROL [us8028.nordvpn.com]: 'PUSH_REQUEST' (status=1)
sniproxyvpn | Mon Nov 9 17:31:41 2020 AUTH: Received control message: AUTH_FAILED
sniproxyvpn | Mon Nov 9 17:31:41 2020 SIGUSR1[soft,auth-failure] received, process restarting
sniproxyvpn | Mon Nov 9 17:31:41 2020 Restart pause, 10 second(s)
sniproxyvpn | Mon Nov 9 17:31:51 2020 WARNING: --ping should normally be used with --ping-restart or --ping-exit
sniproxyvpn | Mon Nov 9 17:31:51 2020 TCP/UDP: Preserving recently used remote address: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:31:51 2020 Socket Buffers: R=[212992->212992] S=[212992->212992]
sniproxyvpn | Mon Nov 9 17:31:51 2020 UDP link local: (not bound)
sniproxyvpn | Mon Nov 9 17:31:51 2020 UDP link remote: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:31:51 2020 TLS: Initial packet from [AF_INET]92.119.17.3:1194, sid=d9248b89 11b59a05
sniproxyvpn | Mon Nov 9 17:31:52 2020 VERIFY OK: depth=1, C=PA, O=NordVPN, CN=NordVPN CA5
sniproxyvpn | Mon Nov 9 17:31:52 2020 VERIFY KU OK
sniproxyvpn | Mon Nov 9 17:31:52 2020 Validating certificate extended key usage
sniproxyvpn | Mon Nov 9 17:31:52 2020 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
sniproxyvpn | Mon Nov 9 17:31:52 2020 VERIFY EKU OK
sniproxyvpn | Mon Nov 9 17:31:52 2020 VERIFY OK: depth=0, CN=us8028.nordvpn.com
sniproxyvpn | Mon Nov 9 17:31:54 2020 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
sniproxyvpn | Mon Nov 9 17:31:54 2020 [us8028.nordvpn.com] Peer Connection Initiated with [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:31:55 2020 SENT CONTROL [us8028.nordvpn.com]: 'PUSH_REQUEST' (status=1)
sniproxyvpn | Mon Nov 9 17:31:55 2020 AUTH: Received control message: AUTH_FAILED
sniproxyvpn | Mon Nov 9 17:31:55 2020 SIGUSR1[soft,auth-failure] received, process restarting
sniproxyvpn | Mon Nov 9 17:31:55 2020 Restart pause, 10 second(s)
sniproxyvpn | Mon Nov 9 17:32:05 2020 WARNING: --ping should normally be used with --ping-restart or --ping-exit
sniproxyvpn | Mon Nov 9 17:32:05 2020 TCP/UDP: Preserving recently used remote address: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:32:05 2020 Socket Buffers: R=[212992->212992] S=[212992->212992]
sniproxyvpn | Mon Nov 9 17:32:05 2020 UDP link local: (not bound)
sniproxyvpn | Mon Nov 9 17:32:05 2020 UDP link remote: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:32:05 2020 TLS: Initial packet from [AF_INET]92.119.17.3:1194, sid=0cd805e8 c452a2d5
sniproxyvpn | Mon Nov 9 17:32:05 2020 VERIFY OK: depth=1, C=PA, O=NordVPN, CN=NordVPN CA5
sniproxyvpn | Mon Nov 9 17:32:05 2020 VERIFY KU OK
sniproxyvpn | Mon Nov 9 17:32:05 2020 Validating certificate extended key usage
sniproxyvpn | Mon Nov 9 17:32:05 2020 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
sniproxyvpn | Mon Nov 9 17:32:05 2020 VERIFY EKU OK
sniproxyvpn | Mon Nov 9 17:32:05 2020 VERIFY OK: depth=0, CN=us8028.nordvpn.com
sniproxyvpn | Mon Nov 9 17:32:07 2020 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
sniproxyvpn | Mon Nov 9 17:32:07 2020 [us8028.nordvpn.com] Peer Connection Initiated with [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:32:08 2020 SENT CONTROL [us8028.nordvpn.com]: 'PUSH_REQUEST' (status=1)
sniproxyvpn | Mon Nov 9 17:32:08 2020 AUTH: Received control message: AUTH_FAILED
sniproxyvpn | Mon Nov 9 17:32:08 2020 SIGUSR1[soft,auth-failure] received, process restarting
sniproxyvpn | Mon Nov 9 17:32:08 2020 Restart pause, 10 second(s)
sniproxyvpn | Mon Nov 9 17:32:18 2020 WARNING: --ping should normally be used with --ping-restart or --ping-exit
sniproxyvpn | Mon Nov 9 17:32:18 2020 TCP/UDP: Preserving recently used remote address: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:32:18 2020 Socket Buffers: R=[212992->212992] S=[212992->212992]
sniproxyvpn | Mon Nov 9 17:32:18 2020 UDP link local: (not bound)
sniproxyvpn | Mon Nov 9 17:32:18 2020 UDP link remote: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:32:18 2020 TLS: Initial packet from [AF_INET]92.119.17.3:1194, sid=8613145d 75db7c16
sniproxyvpn | Mon Nov 9 17:32:18 2020 VERIFY OK: depth=1, C=PA, O=NordVPN, CN=NordVPN CA5
sniproxyvpn | Mon Nov 9 17:32:18 2020 VERIFY KU OK
sniproxyvpn | Mon Nov 9 17:32:18 2020 Validating certificate extended key usage
sniproxyvpn | Mon Nov 9 17:32:18 2020 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
sniproxyvpn | Mon Nov 9 17:32:18 2020 VERIFY EKU OK
sniproxyvpn | Mon Nov 9 17:32:18 2020 VERIFY OK: depth=0, CN=us8028.nordvpn.com
sniproxyvpn | Mon Nov 9 17:32:20 2020 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
sniproxyvpn | Mon Nov 9 17:32:20 2020 [us8028.nordvpn.com] Peer Connection Initiated with [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:32:21 2020 SENT CONTROL [us8028.nordvpn.com]: 'PUSH_REQUEST' (status=1)
sniproxyvpn | Mon Nov 9 17:32:21 2020 AUTH: Received control message: AUTH_FAILED
sniproxyvpn | Mon Nov 9 17:32:21 2020 SIGUSR1[soft,auth-failure] received, process restarting
sniproxyvpn | Mon Nov 9 17:32:21 2020 Restart pause, 10 second(s)
sniproxyvpn | Mon Nov 9 17:32:31 2020 WARNING: --ping should normally be used with --ping-restart or --ping-exit
sniproxyvpn | Mon Nov 9 17:32:31 2020 TCP/UDP: Preserving recently used remote address: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:32:31 2020 Socket Buffers: R=[212992->212992] S=[212992->212992]
sniproxyvpn | Mon Nov 9 17:32:31 2020 UDP link local: (not bound)
sniproxyvpn | Mon Nov 9 17:32:31 2020 UDP link remote: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:32:32 2020 TLS: Initial packet from [AF_INET]92.119.17.3:1194, sid=95675d9d 88d6523c
sniproxyvpn | Mon Nov 9 17:32:32 2020 VERIFY OK: depth=1, C=PA, O=NordVPN, CN=NordVPN CA5
sniproxyvpn | Mon Nov 9 17:32:32 2020 VERIFY KU OK
sniproxyvpn | Mon Nov 9 17:32:32 2020 Validating certificate extended key usage
sniproxyvpn | Mon Nov 9 17:32:32 2020 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
sniproxyvpn | Mon Nov 9 17:32:32 2020 VERIFY EKU OK
sniproxyvpn | Mon Nov 9 17:32:32 2020 VERIFY OK: depth=0, CN=us8028.nordvpn.com
sniproxyvpn | Mon Nov 9 17:32:34 2020 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
sniproxyvpn | Mon Nov 9 17:32:34 2020 [us8028.nordvpn.com] Peer Connection Initiated with [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:32:35 2020 SENT CONTROL [us8028.nordvpn.com]: 'PUSH_REQUEST' (status=1)
sniproxyvpn | Mon Nov 9 17:32:35 2020 AUTH: Received control message: AUTH_FAILED
sniproxyvpn | Mon Nov 9 17:32:35 2020 SIGUSR1[soft,auth-failure] received, process restarting
sniproxyvpn | Mon Nov 9 17:32:35 2020 Restart pause, 10 second(s)
sniproxyvpn | Mon Nov 9 17:32:45 2020 WARNING: --ping should normally be used with --ping-restart or --ping-exit
sniproxyvpn | Mon Nov 9 17:32:45 2020 TCP/UDP: Preserving recently used remote address: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:32:45 2020 Socket Buffers: R=[212992->212992] S=[212992->212992]
sniproxyvpn | Mon Nov 9 17:32:45 2020 UDP link local: (not bound)
sniproxyvpn | Mon Nov 9 17:32:45 2020 UDP link remote: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:32:45 2020 TLS: Initial packet from [AF_INET]92.119.17.3:1194, sid=32289e25 93dcb7e2
sniproxyvpn | Mon Nov 9 17:32:45 2020 VERIFY OK: depth=1, C=PA, O=NordVPN, CN=NordVPN CA5
sniproxyvpn | Mon Nov 9 17:32:45 2020 VERIFY KU OK
sniproxyvpn | Mon Nov 9 17:32:45 2020 Validating certificate extended key usage
sniproxyvpn | Mon Nov 9 17:32:45 2020 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
sniproxyvpn | Mon Nov 9 17:32:45 2020 VERIFY EKU OK
sniproxyvpn | Mon Nov 9 17:32:45 2020 VERIFY OK: depth=0, CN=us8028.nordvpn.com
sniproxyvpn | Mon Nov 9 17:32:47 2020 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
sniproxyvpn | Mon Nov 9 17:32:47 2020 [us8028.nordvpn.com] Peer Connection Initiated with [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:32:48 2020 SENT CONTROL [us8028.nordvpn.com]: 'PUSH_REQUEST' (status=1)
sniproxyvpn | Mon Nov 9 17:32:49 2020 AUTH: Received control message: AUTH_FAILED
sniproxyvpn | Mon Nov 9 17:32:49 2020 SIGUSR1[soft,auth-failure] received, process restarting
sniproxyvpn | Mon Nov 9 17:32:49 2020 Restart pause, 10 second(s)
sniproxyvpn | Mon Nov 9 17:32:59 2020 WARNING: --ping should normally be used with --ping-restart or --ping-exit
sniproxyvpn | Mon Nov 9 17:32:59 2020 TCP/UDP: Preserving recently used remote address: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:32:59 2020 Socket Buffers: R=[212992->212992] S=[212992->212992]
sniproxyvpn | Mon Nov 9 17:32:59 2020 UDP link local: (not bound)
sniproxyvpn | Mon Nov 9 17:32:59 2020 UDP link remote: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:32:59 2020 TLS: Initial packet from [AF_INET]92.119.17.3:1194, sid=70e68587 01a9c52d
sniproxyvpn | Mon Nov 9 17:32:59 2020 VERIFY OK: depth=1, C=PA, O=NordVPN, CN=NordVPN CA5
sniproxyvpn | Mon Nov 9 17:32:59 2020 VERIFY KU OK
sniproxyvpn | Mon Nov 9 17:32:59 2020 Validating certificate extended key usage
sniproxyvpn | Mon Nov 9 17:32:59 2020 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
sniproxyvpn | Mon Nov 9 17:32:59 2020 VERIFY EKU OK
sniproxyvpn | Mon Nov 9 17:32:59 2020 VERIFY OK: depth=0, CN=us8028.nordvpn.com
sniproxyvpn | Mon Nov 9 17:33:01 2020 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
sniproxyvpn | Mon Nov 9 17:33:01 2020 [us8028.nordvpn.com] Peer Connection Initiated with [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:33:02 2020 SENT CONTROL [us8028.nordvpn.com]: 'PUSH_REQUEST' (status=1)
sniproxyvpn | Mon Nov 9 17:33:02 2020 AUTH: Received control message: AUTH_FAILED
sniproxyvpn | Mon Nov 9 17:33:02 2020 SIGUSR1[soft,auth-failure] received, process restarting
sniproxyvpn | Mon Nov 9 17:33:02 2020 Restart pause, 10 second(s)
sniproxyvpn | Mon Nov 9 17:33:12 2020 WARNING: --ping should normally be used with --ping-restart or --ping-exit
sniproxyvpn | Mon Nov 9 17:33:12 2020 TCP/UDP: Preserving recently used remote address: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:33:12 2020 Socket Buffers: R=[212992->212992] S=[212992->212992]
sniproxyvpn | Mon Nov 9 17:33:12 2020 UDP link local: (not bound)
sniproxyvpn | Mon Nov 9 17:33:12 2020 UDP link remote: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:33:12 2020 TLS: Initial packet from [AF_INET]92.119.17.3:1194, sid=d2983803 0c809e55
sniproxyvpn | Mon Nov 9 17:33:12 2020 VERIFY OK: depth=1, C=PA, O=NordVPN, CN=NordVPN CA5
sniproxyvpn | Mon Nov 9 17:33:12 2020 VERIFY KU OK
sniproxyvpn | Mon Nov 9 17:33:12 2020 Validating certificate extended key usage
sniproxyvpn | Mon Nov 9 17:33:12 2020 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
sniproxyvpn | Mon Nov 9 17:33:12 2020 VERIFY EKU OK
sniproxyvpn | Mon Nov 9 17:33:12 2020 VERIFY OK: depth=0, CN=us8028.nordvpn.com
sniproxyvpn | Mon Nov 9 17:33:14 2020 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
sniproxyvpn | Mon Nov 9 17:33:14 2020 [us8028.nordvpn.com] Peer Connection Initiated with [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:33:15 2020 SENT CONTROL [us8028.nordvpn.com]: 'PUSH_REQUEST' (status=1)
sniproxyvpn | Mon Nov 9 17:33:15 2020 AUTH: Received control message: AUTH_FAILED
sniproxyvpn | Mon Nov 9 17:33:15 2020 SIGUSR1[soft,auth-failure] received, process restarting
sniproxyvpn | Mon Nov 9 17:33:15 2020 Restart pause, 10 second(s)
sniproxyvpn | Mon Nov 9 17:33:25 2020 WARNING: --ping should normally be used with --ping-restart or --ping-exit
sniproxyvpn | Mon Nov 9 17:33:25 2020 TCP/UDP: Preserving recently used remote address: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:33:25 2020 Socket Buffers: R=[212992->212992] S=[212992->212992]
sniproxyvpn | Mon Nov 9 17:33:25 2020 UDP link local: (not bound)
sniproxyvpn | Mon Nov 9 17:33:25 2020 UDP link remote: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:33:25 2020 TLS: Initial packet from [AF_INET]92.119.17.3:1194, sid=17c5c6f6 e0b1e756
sniproxyvpn | Mon Nov 9 17:33:26 2020 VERIFY OK: depth=1, C=PA, O=NordVPN, CN=NordVPN CA5
sniproxyvpn | Mon Nov 9 17:33:26 2020 VERIFY KU OK
sniproxyvpn | Mon Nov 9 17:33:26 2020 Validating certificate extended key usage
sniproxyvpn | Mon Nov 9 17:33:26 2020 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
sniproxyvpn | Mon Nov 9 17:33:26 2020 VERIFY EKU OK
sniproxyvpn | Mon Nov 9 17:33:26 2020 VERIFY OK: depth=0, CN=us8028.nordvpn.com
sniproxyvpn | Mon Nov 9 17:33:28 2020 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
sniproxyvpn | Mon Nov 9 17:33:28 2020 [us8028.nordvpn.com] Peer Connection Initiated with [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:33:29 2020 SENT CONTROL [us8028.nordvpn.com]: 'PUSH_REQUEST' (status=1)
sniproxyvpn | Mon Nov 9 17:33:29 2020 AUTH: Received control message: AUTH_FAILED
sniproxyvpn | Mon Nov 9 17:33:29 2020 SIGUSR1[soft,auth-failure] received, process restarting
sniproxyvpn | Mon Nov 9 17:33:29 2020 Restart pause, 10 second(s)
sniproxyvpn | Mon Nov 9 17:33:39 2020 WARNING: --ping should normally be used with --ping-restart or --ping-exit
sniproxyvpn | Mon Nov 9 17:33:39 2020 TCP/UDP: Preserving recently used remote address: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:33:39 2020 Socket Buffers: R=[212992->212992] S=[212992->212992]
sniproxyvpn | Mon Nov 9 17:33:39 2020 UDP link local: (not bound)
sniproxyvpn | Mon Nov 9 17:33:39 2020 UDP link remote: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:33:39 2020 TLS: Initial packet from [AF_INET]92.119.17.3:1194, sid=d0831d67 dbc26cf2
sniproxyvpn | Mon Nov 9 17:33:39 2020 VERIFY OK: depth=1, C=PA, O=NordVPN, CN=NordVPN CA5
sniproxyvpn | Mon Nov 9 17:33:39 2020 VERIFY KU OK
sniproxyvpn | Mon Nov 9 17:33:39 2020 Validating certificate extended key usage
sniproxyvpn | Mon Nov 9 17:33:39 2020 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
sniproxyvpn | Mon Nov 9 17:33:39 2020 VERIFY EKU OK
sniproxyvpn | Mon Nov 9 17:33:39 2020 VERIFY OK: depth=0, CN=us8028.nordvpn.com
sniproxyvpn | Mon Nov 9 17:33:41 2020 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
sniproxyvpn | Mon Nov 9 17:33:41 2020 [us8028.nordvpn.com] Peer Connection Initiated with [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:33:42 2020 SENT CONTROL [us8028.nordvpn.com]: 'PUSH_REQUEST' (status=1)
sniproxyvpn | Mon Nov 9 17:33:42 2020 AUTH: Received control message: AUTH_FAILED
sniproxyvpn | Mon Nov 9 17:33:42 2020 SIGUSR1[soft,auth-failure] received, process restarting
sniproxyvpn | Mon Nov 9 17:33:42 2020 Restart pause, 10 second(s)
sniproxyvpn | Mon Nov 9 17:33:52 2020 WARNING: --ping should normally be used with --ping-restart or --ping-exit
sniproxyvpn | Mon Nov 9 17:33:52 2020 TCP/UDP: Preserving recently used remote address: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:33:52 2020 Socket Buffers: R=[212992->212992] S=[212992->212992]
sniproxyvpn | Mon Nov 9 17:33:52 2020 UDP link local: (not bound)
sniproxyvpn | Mon Nov 9 17:33:52 2020 UDP link remote: [AF_INET]92.119.17.3:1194
sniproxyvpn | Mon Nov 9 17:33:52 2020 TLS: Initial packet from [AF_INET]92.119.17.3:1194, sid=5abc9a74 ca67a17f
sniproxyvpn | Mon Nov 9 17:33:52 2020 VERIFY OK: depth=1, C=PA, O=NordVPN, CN=NordVPN CA5
sniproxyvpn | Mon Nov 9 17:33:52 2020 VERIFY KU OK
sniproxyvpn | Mon Nov 9 17:33:52 2020 Validating certificate extended key usage
sniproxyvpn | Mon Nov 9 17:33:52 2020 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
sniproxyvpn | Mon Nov 9 17:33:52 2020 VERIFY EKU OK
sniproxyvpn | Mon Nov 9 17:33:52 2020 VERIFY OK: depth=0, CN=us8028.nordvpn.com