Comments (23)
I succeeded attestation and assertion using the example in https://webauthn.io (there are quite a few libraries out there).
In addition, I used Microsoft' sample for implementing WebAuthn with resident key.
from simplewebauthn.
This is the raw attestation (JSON) returned from startAttestation:
{
"attResp": {
"id": "QdiHnAdxCTeVpw2Up2QYdbTG1fQFLwfdELRHvyyZg10",
"rawId": "QdiHnAdxCTeVpw2Up2QYdbTG1fQFLwfdELRHvyyZg10",
"response": {
"attestationObject": "o2NmbXRkbm9uZWdhdHRTdG10oGhhdXRoRGF0YVkBZ9Ukck8V92UT5YFZtBoVSQZWyFTM-rDMTOAW1DLfg1hnRQAAAAAAAAAAAAAAAAAAAAAAAAAAACBB2IecB3EJN5WnDZSnZBh1tMbV9AUvB90QtEe_LJmDXaQBAwM5AQAgWQEAycssl7oWfq6Kl9I_CUlJAMDvgR_ikvp6ugJxuQCTlmJ399AzoenJMrN_GcudcIdVviopUwTIipVZfsXrHRShZXh9hoSwt6Hxc8hYy2fHsOOhYeQ1k7pheZD_U_obAkuZa31I_0EqkkTAEgKJ0MIw0NQKQcL9SvqB0cvowj1j_mAfgEc519SDSqtfUkeX8if36Y10jJPok-ieczFKAQn5V_0VhSAoCUXM9gsNArOo2K8BxU8N5gwFWnJIYIkEHQBxO2IC4w5W14wftU1Ysh0kzNWFSAR4obKmUVZMSr04pHu-3bd_aHadTd9zCUtrmFB3bHkCgOYidpYNpy0xLiJDWSFDAQAB",
"clientDataJSON": "eyJ0eXBlIjoid2ViYXV0aG4uY3JlYXRlIiwiY2hhbGxlbmdlIjoiLThHZXZjMzVlOVlremxvY05DbjhxRWdMN1ZLZDZSeDlac3NsTkw4SWE2QSIsIm9yaWdpbiI6Imh0dHBzOi8vZGV2Lm5ldHBhc3Nwb3J0LmlvIiwiY3Jvc3NPcmlnaW4iOmZhbHNlfQ"
},
"type": "public-key"
}
}
from simplewebauthn.
Good news, I was able to successfully fix the original error mentioned at the beginning of this issue!
error:0D0680A8:asn1 encoding routines:asn1_check_tlen:wrong tag
It turns out RSA support wasn't nearly as baked as I thought. Suspiciously short public keys I was getting back from Attestation were due to the library trying to convert RSA keys to PKCS format as though they were ECC keys.
This doesn't solve any TPM-related issues as it turns out I'd been getting None type attestations with RSA public keys instead of the TPM attestations I was hoping for.
from simplewebauthn.
@yaron14 I confirmed that I received the same "Certificate contained incomplete subjectAltName data" error with that TPM attestation you posted above.
I'm happy to report that I was able to solve the issue 🎉
Here's output from the fixed verifyAttestationResponse() for that TPM attestation:
{
"verified": true,
"userVerified": true,
"authenticatorInfo": {
"fmt": "tpm",
"counter": 0,
"base64PublicKey": "pAEDAzkBACBZAQC0ciFRFbWRy-FM8K7FKCWx1xQ9lkpjErkYnun5Fbu6h8OeXpPdngMam85Kf56JRuwKPtwz-cToz-wjjQ7Bpg--EaBE4_WEoQc6lfEoShDSAa2gvf1rKhOoe4quaRu3lxpqGCp5qRSbKET3SWYSphrfo6AD_qQ2X8safYhnRb7WatyTP42qKCwzWX0J4JovMG4d_zteT1q3wljbp2XGxcF9qPTHhqSjj2h20DeP4dDS-TZzLsytSYCswpBE-WvEElcIslIhmFdmnbRY5UMECR9tkyp3NfwHBGqP_uZVwilxRC3rVTuGWSNm9pdqrgADnLftVeKSNGU22tnMxyNb-4MVIUMBAAE",
"base64CredentialID": "LVwzXx0fStkvsos_jdl9DTd6O3-6be8Ua4tcdXc5XeM"
}
}I'll release a new version in a day or two with this fix.
from simplewebauthn.
@yaron14 I confirmed that I received the same "Certificate contained incomplete subjectAltName data" error with that TPM attestation you posted above.
FYI, I am currently chasing down an issue that sounds suspiciously like this one. There are apparently two SAN configurations in the wild, one that is 100% per spec, and another that is slightly off. Thread: passwordless-lib/fido2-net-lib#187
from simplewebauthn.
@MasterKale Sure! I'll test and make you notice about it.
And after testing it I'll add the TPM assertion response here.
from simplewebauthn.
Attestation:
{ "id": "ryoAn12QaYeC5t21-E4U2kV92VbFWOBMfdXFa7KMkpY", "rawId": "ryoAn12QaYeC5t21-E4U2kV92VbFWOBMfdXFa7KMkpY", "response": { "attestationObject": "o2NmbXRjdHBtZ2F0dFN0bXSmY2FsZzn__mNzaWdZAQA3gSb0KX3ANQz4XdqVh1NUGn2vgjw2cHdmsySEfDPaBH1mPglMyRkl9bV5Bo4eeU4j1rympeJxBBXBj4xw6NbBEzEIRQnoJv5sLvbxpYTl0alB6qYiid3csTP8NG3OpbP2bbPSTxA47lq3meKH0TlKajINCbGYg-RMdHeU2AoFV7OKlGhlWVnLbzAtF8cwfLtDQk1XQul_LF7HrB-bz7YqtG2QlemwuO5PoDqzmNBexGgZlXh4KpLlHinOcg9jybJ7sStAOy_cUbUzK-RM_C8vSzEDeyHtDKvjLesMLZ3uruNCAHW2iK5JuCGKehto1MC3r_FtnE33aJMinJIGw-FeY3ZlcmMyLjBjeDVjglkFxDCCBcAwggOooAMCAQICEGoHJ5pU80VnnGzPa5PrxlkwDQYJKoZIhvcNAQELBQAwQTE_MD0GA1UEAxM2RVVTLVNUTS1LRVlJRC0xQURCOTk0QUI1OEJFNTdBMENDOUI5MDBFNzg1MUUxQTQzQzA4NjYwMB4XDTIwMDgyNzE1MTIzMFoXDTI1MDMyMTIwMjkxNVowADCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAKkVhLA9cKyViKaVr6wwKqzty1AKR0VJGa3BB3QF7IfK81mfqv-x31Y0V0zPioxYgPHHfF4j4XPm5mVlQI9PluM828elk86kwPV-OFlhIX7nM1Hy9NQtgnfyV-7Kxmb3pKe2TI937XrtuJj0pKUav3g0RtPUZDywpWBVDCI4AopqLVyys8bse_bZdDI-l8IDqpzptL1kfmH2WG6rtCIyVimGQS3UtgkNpl-8FeDXOc3ciAYdY9MUHfE6QmFpwXn_qo_4x0VR1wiBKyK0ZACTAm96io_iskeyig3OGR_SEd2OeThYQtoJoAfZvBzSs3eTVTAsZ8unKnGjkss7eCF48Q8CAwEAAaOCAfMwggHvMA4GA1UdDwEB_wQEAwIHgDAMBgNVHRMBAf8EAjAAMG0GA1UdIAEB_wRjMGEwXwYJKwYBBAGCNxUfMFIwUAYIKwYBBQUHAgIwRB5CAFQAQwBQAEEAIAAgAFQAcgB1AHMAdABlAGQAIAAgAFAAbABhAHQAZgBvAHIAbQAgACAASQBkAGUAbgB0AGkAdAB5MBAGA1UdJQQJMAcGBWeBBQgDMFkGA1UdEQEB_wRPME2kSzBJMRYwFAYFZ4EFAgEMC2lkOjUzNTQ0RDIwMRcwFQYFZ4EFAgIMDFNUMzNIVFB4QUhBNjEWMBQGBWeBBQIDDAtpZDowMDQ3MDAwNDAfBgNVHSMEGDAWgBS4X9VnypLEDs8M2B9tPwNVbzimUTAdBgNVHQ4EFgQUSk_obuVTgSLFuag0uCvjqcyeFPIwgbIGCCsGAQUFBwEBBIGlMIGiMIGfBggrBgEFBQcwAoaBkmh0dHA6Ly9hemNzcHJvZGV1c2Fpa3B1Ymxpc2guYmxvYi5jb3JlLndpbmRvd3MubmV0L2V1cy1zdG0ta2V5aWQtMWFkYjk5NGFiNThiZTU3YTBjYzliOTAwZTc4NTFlMWE0M2MwODY2MC9hYmQ2MTVmMi0xNThhLTQ1OGUtYTE1NS03YzRjOGNiMTNjNjUuY2VyMA0GCSqGSIb3DQEBCwUAA4ICAQDYZJbtNQICOEg3N3UULml0qfQyuitzuVZJ59nvhhwHH6SsWLXhoZVgKaV3zOd00nJPVnX8uilmX2o9qkNi1ODO7WQ-wN2_jVtNsVDu1mgox6T6NeWzel-EbJdkg2kiwUaO639Yu_Xc8FUKNtUp-9fuF2p31uoYo-Nw-H58rbYOdsiOQ-SPYI4zbdjssntKyI6MAT_j1KAKv0Gbh5SvKM4aEmZA0v0dHXuxoH6kFVHLeNdwLe0cG__K9rCw5CKOD0zFMnKRx6LfNzaZ0OedM9skVjHPqR3qEfwGFXQzrfVGFzrri2vaE9bo2Q-cREY6ITX6kUJpkSc6Iz96hxpSxyIxN1faSeblMETRJD4pV0PtJGZb4GOeng0lQ8l4IkBlBgx-I27Ks_tTsf2owNkVOWTViWZLYLon0l_LhNKuuGJkjB0whvccBB4DiQPTckuCeFoB8IH5wAR__A_y33_zBR0fYWnVlEXWwtMO-vGRYQLPuK6j30MWBjPEvtujsS1gwJUhXnd3GENHaXtrQHnyZgLzRCHSeJy6SjI64Jm86VMMalvLJEbGrvjfs-vKnBKAoK_9JcK-tmx4pIJIm1gtOx-J59bfpLjgueBqpvVl3dz1r9dCXrRlsCCeqtXOFPK5lgJz3sxXyDxAT-Np52S1pfrui1i2VvnHB-YEM83nubdz01kG7zCCBuswggTToAMCAQICEzMAAAI5-btqHUlkR38AAAAAAjkwDQYJKoZIhvcNAQELBQAwgYwxCzAJBgNVBAYTAlVTMRMwEQYDVQQIEwpXYXNoaW5ndG9uMRAwDgYDVQQHEwdSZWRtb25kMR4wHAYDVQQKExVNaWNyb3NvZnQgQ29ycG9yYXRpb24xNjA0BgNVBAMTLU1pY3Jvc29mdCBUUE0gUm9vdCBDZXJ0aWZpY2F0ZSBBdXRob3JpdHkgMjAxNDAeFw0xOTAzMjEyMDI5MTVaFw0yNTAzMjEyMDI5MTVaMEExPzA9BgNVBAMTNkVVUy1TVE0tS0VZSUQtMUFEQjk5NEFCNThCRTU3QTBDQzlCOTAwRTc4NTFFMUE0M0MwODY2MDCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBANviI_mGj6lxn4v5fOlFLVlWXpb03ZoSzZAaDLUDvwm-v_dVUug5TL4qKIh4OafL-UxV0jGWO0ii8_bTGoF_kGKr7FrHoH-BMiebKXV9HpbF-g584GCWesqUuuayad3EfbvTxLRuAIYfnSXorscQhNzANCRu9_zdPTJ6Q5bWyHv0mz2nHrpN0Ds9hJrRJSJdAESwWbdAxaNTU6-Pnv2PHgLTT_cJzsXGcVzp6Hq1a6S_C9m2-iSwzVIiHX7oFS8eXqLs06gCd7lVms_M1wggpdo5mjB2kDenYN8YEmUXqt1I1RIdTINdgQcdGIFAVWCPo2s0HtXmz1Jzd0pQTxsPOcMNFvm7THf2Tqyc_ui7UqUKDpvwDe_7b4k0fUfsFGr0CuFgRHN7oKtbjEOmBUJhRqoc9ewshoUhmd9FjvTRHvvNm5Qy4KDMT62uRIuGJ5H-YJ_yYzBsXY28q9T1orJ06NSV8tYDi8mjUudjBWRQ5QpqoGxQzTeYqIcCOFtsAmk9H5V0TUZ2Kp1i1Mcb-TGmUe57yORuOs9PT0mK9U8lkyMC73mmJ75a53S316jBrlWIpMdNt2Lw-Vu_R1v-zAuJGWVLb99PfU2WQg0qob0-cJK6yFnVHTqYU3WmMshyA0ZfXBOk28dVNSINxheFvUZL-h5Jwv4e-WKJVoTfoPv9k6QlAgMBAAGjggGOMIIBijAOBgNVHQ8BAf8EBAMCAoQwGwYDVR0lBBQwEgYJKwYBBAGCNxUkBgVngQUIAzAWBgNVHSAEDzANMAsGCSsGAQQBgjcVHzASBgNVHRMBAf8ECDAGAQH_AgEAMB0GA1UdDgQWBBS4X9VnypLEDs8M2B9tPwNVbzimUTAfBgNVHSMEGDAWgBR6jArOL0hiF-KU0a5VwVLscXSkVjBwBgNVHR8EaTBnMGWgY6Bhhl9odHRwOi8vd3d3Lm1pY3Jvc29mdC5jb20vcGtpb3BzL2NybC9NaWNyb3NvZnQlMjBUUE0lMjBSb290JTIwQ2VydGlmaWNhdGUlMjBBdXRob3JpdHklMjAyMDE0LmNybDB9BggrBgEFBQcBAQRxMG8wbQYIKwYBBQUHMAKGYWh0dHA6Ly93d3cubWljcm9zb2Z0LmNvbS9wa2lvcHMvY2VydHMvTWljcm9zb2Z0JTIwVFBNJTIwUm9vdCUyMENlcnRpZmljYXRlJTIwQXV0aG9yaXR5JTIwMjAxNC5jcnQwDQYJKoZIhvcNAQELBQADggIBAEGq_ihs92tT3nfAgFCU2dtGjmqTqRA3Jx_1cPGoz6FFhirdj7i1webPivoyoUu3pL8KSMtCY3HBlrk6N4QOJDnrWM49t6lEklm5_9sYvmpe587vuEBTr8Gb-0KZfp0FK3EKenpE0THK8F90hanivMgMrVfR6UiQiFeG18XJ5rJeXxPcEH_fY4rVnpDCdVMeaBcrAykVA8WMZj6uvUoyflmJC4TC2ZD6AiKQjZy2DE3hKHbXgsM2wqMqUuX-PI_jS9pq28B6PFf6hY_7YsOhOM6E8roS9DAqSpSpNSx9EcdoH0eqV0MGcHmMtjtdV_PzwCzF3kGZ9t1ViuQTysnsaZMTSPBf2i79-6kbkt5JcTeMP8IICoMl8W4K41WFlpotosCh7v4jO2kiA_3Mit20U42EpqzgHgfl1_nLueOat4RwoZPWAh7-2yh899Rib4B1yNg1JgzLhO27ld9_1bsAlpcy57roKbUaUYG7BNEhdjRtHpOWH5ZTX1ye852CHDk2Wa7JPFNKZ2Vuv6asPtqyp2MHF-Fb2moxn_u06qGXCG6yaPNydpnoAEaIJuE8Byt4Sdp5Or1vylygqO00zNsT4lGbPQOsx_Yy4RFd4cX9nnrNBrnm_OADMfRKqTt5AbBkaJ9udqHM7BdBndRbTp3lRtRrYCojtXqJfCeWZZdW7JjjZ3B1YkFyZWFZATYAAQALAAYEcgAgnf_L82w4OuaZ-5ho3G3LidcVOIS-KAOSLBJBWL-tIq4AEAAQCAAAAAAAAQDUVkSaDn-QQuaCrvj9iQSzvg48Op2e4q6jY2vThk6t7utXJkGSfjENx1953c6TbGeWUK-zGPF2BSgq7WM2o2qEF8tZd9oPl45O0Aehd-4LyI1Cgc66z00IwL1c0U8YhI7Q6xVX82KbBa0l63daJ7Vj3Xj6Fc3CtgqnJ2uCte0-n68v2WyC9C8GrUm6twpzCR25lC8VQ37D6RlrY2_PoWwEbbq04Rrr-U1H9xUl73IokfOI_qhhLNOKxOtVqo_XDRN3z1O_joimf97nAKD4BUVKdIRYd70hlGxzBFNIQdHbD8FhiOrZf0DafzyQzSnroyw6YvLbBClJDHHbSO1JuV7jaGNlcnRJbmZvWKH_VENHgBcAIgALI_9Gp39SuKvSJvllxwHyGHhtaaF8TtuCHdfJEBqgCJQAFFla1jPDybSWBhwQg142fqMmFo4gAAAAAARYwl0DEFBNdFFCZAE1hhRhFj_igAAiAAsRZzu4nZeKlmHnyCfKx7Ds9fXHuS9XC00tOEr6SlecFwAiAAvlxdA1U70G8FTYLPSlJ4nXP381tFCKlMXlqjFsSUQTc2hhdXRoRGF0YVkBZ9Ukck8V92UT5YFZtBoVSQZWyFTM-rDMTOAW1DLfg1hnRQAAAAAImHBYytxLgbbhMN5Q3L6WACCvKgCfXZBph4Lm3bX4ThTaRX3ZVsVY4Ex91cVrsoySlqQBAwM5AQAgWQEA1FZEmg5_kELmgq74_YkEs74OPDqdnuKuo2Nr04ZOre7rVyZBkn4xDcdfed3Ok2xnllCvsxjxdgUoKu1jNqNqhBfLWXfaD5eOTtAHoXfuC8iNQoHOus9NCMC9XNFPGISO0OsVV_NimwWtJet3Wie1Y914-hXNwrYKpydrgrXtPp-vL9lsgvQvBq1JurcKcwkduZQvFUN-w-kZa2Nvz6FsBG26tOEa6_lNR_cVJe9yKJHziP6oYSzTisTrVaqP1w0Td89Tv46Ipn_e5wCg-AVFSnSEWHe9IZRscwRTSEHR2w_BYYjq2X9A2n88kM0p66MsOmLy2wQpSQxx20jtSble4yFDAQAB", "clientDataJSON": "eyJ0eXBlIjoid2ViYXV0aG4uY3JlYXRlIiwiY2hhbGxlbmdlIjoiN3Q4ZFBBSGFNQzhrZ282RGhaWktTeVI0QllOS1ZSTm93MVZIVzhfaWRNYyIsIm9yaWdpbiI6Imh0dHBzOi8vZGV2Lm5ldHBhc3Nwb3J0LmlvIiwiY3Jvc3NPcmlnaW4iOmZhbHNlfQ" }, "type": "public-key" }
Assertion:
{ "id": "ryoAn12QaYeC5t21-E4U2kV92VbFWOBMfdXFa7KMkpY", "rawId": "ryoAn12QaYeC5t21-E4U2kV92VbFWOBMfdXFa7KMkpY", "response": { "authenticatorData": "1SRyTxX3ZRPlgVm0GhVJBlbIVMz6sMxM4BbUMt-DWGcFAAAAAQ", "clientDataJSON": "eyJ0eXBlIjoid2ViYXV0aG4uZ2V0IiwiY2hhbGxlbmdlIjoibDVmb3JLampkV2FxR1lmX042bnhlZXdJY04tbkFJNUM5bDJvU0ZiWlZDVG0yaUNQUUEtblhvbFh4QmxVOE1OQ2RrMlJyejRHRU01N09WUFFLNVVxb1EiLCJvcmlnaW4iOiJodHRwczovL2Rldi5uZXRwYXNzcG9ydC5pbyIsImNyb3NzT3JpZ2luIjpmYWxzZX0", "signature": "B5qOGZZK4BBlY9vifFnZIl-XPQOVeIlIrEsiYaJQYsuw8lUeCNZ05opj41ZAVsiyBRMrbJiBRMVyL3PPw4lJXcPotU7hNKj5YlDoFAEx8GMStfDy5bhOQf8HT_Cei-sy-Vo6xPQ-SnSDZxyIQ91Zwv3BK923iG0RI4o2nnYvp5WV3iQF4I_Ll5xoib0DzTK-2swPwoXZHIA8uFUyAf-d43sjYislJa9cIbCI5pcjTwFU5fjX4o7DXscHzDZCcRXGoSZcKLEN8CBY1EjkJs7rD5UWbgqtXux1erT5U4F9UJ5BK8bNhSt018nExU3rXdoinFMvOccUVAvBkp3KLQ424g", "userHandle": "MEdpcVNPK0c4WE5zb3l1ZVBjRzB2VGRTMitiNzlKWUNlSlJtRGZqSVlHbz0" }, "type": "public-key" }
from simplewebauthn.
@yaron14 You rock, thank you! 👏
from simplewebauthn.
Aha, I was wondering when this would come up. I've been aware of this for some time now. If I remember correctly I got as far as discovering that the public key the TPM authenticator returns during attestation is surprisingly short - maybe 16 characters? This strange "public key" causes issues with signature verification at the end of an assertion verification, which is the error you're seeing.
I've had a branch with a unit test on it that recreates this exact same error you're experiencing. I've gone ahead and drafted a WIP PR #50 to eventually contain the fix for this issue.
from simplewebauthn.
Thanks!
Waiting for your next update to install it as a package dependency.
from simplewebauthn.
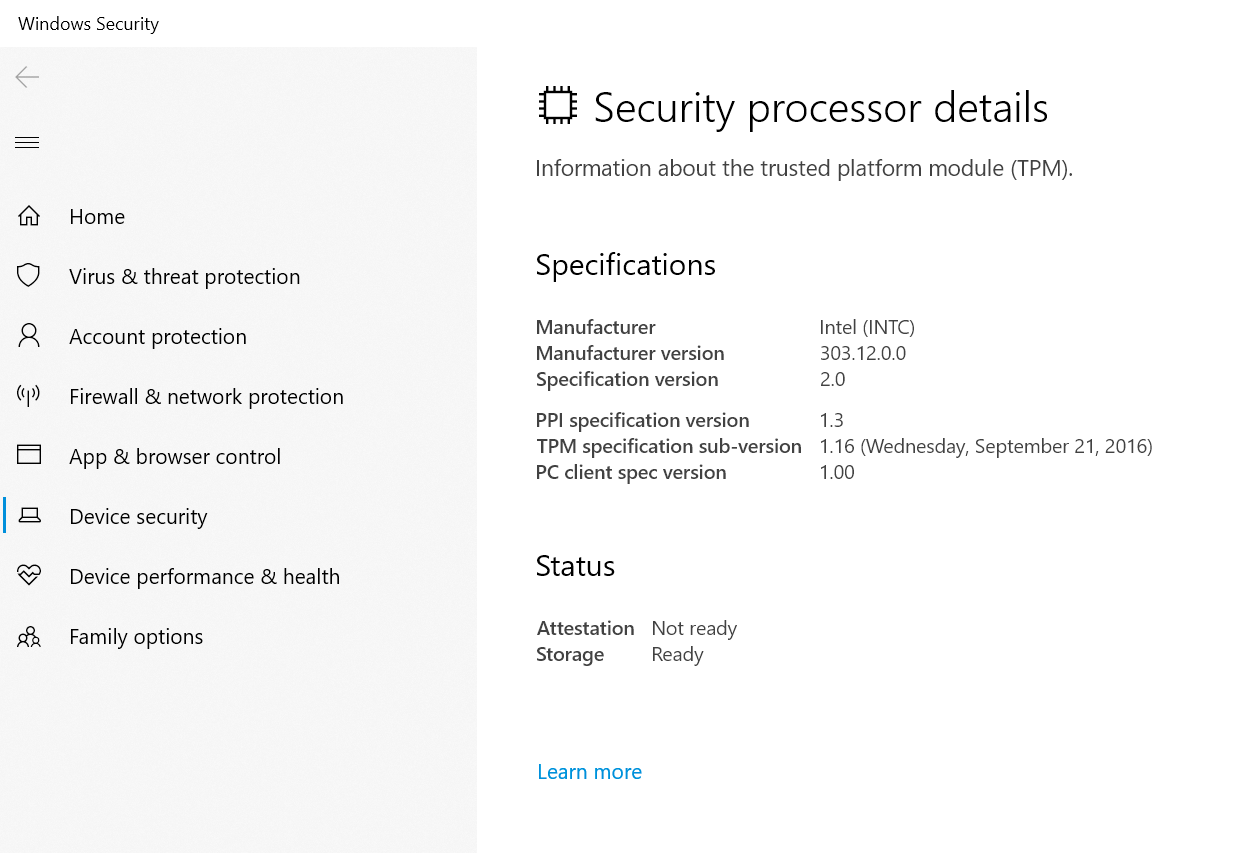
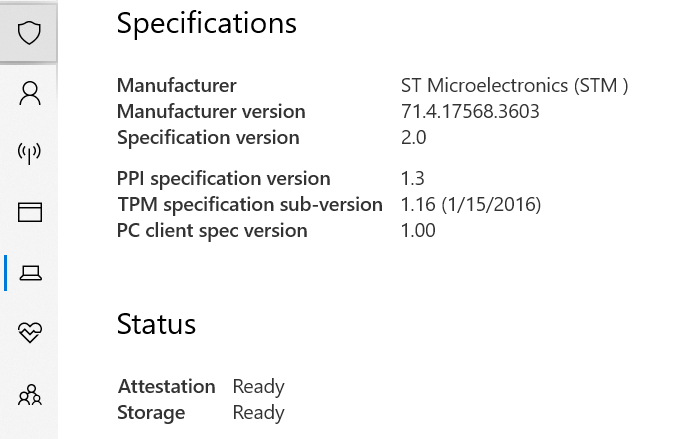
@yaron14 Can you do a Start Menu search for "TPM", click "Security Processor", and then provide a screenshot here of your "Security processor details" screen? It'll look like this:
I'm wondering what your "Attestation" status is. If it's "not ready" like mine then it might mean there's something at the OS/BIOS level that needs to be adjusted to get it to a "Ready" state. This might be a symptom of a mis-configured system preventing valid public keys from being returned in a TPM attestation, which causes assertions to fail.
from simplewebauthn.
I've already tried and tested WebAuthn with some demos and libraries and my TPM authenticattor worked fine.
I believe it relates to what you've said earlier that the public key that been generated is really short and for some reason it failed the signature verification phase.
from simplewebauthn.
I assumed SimpleWebAuthn would handle TPM fine because it passes the FIDO Conformance test which include TPM assertions, but for some reason in the real world something isn't working as expected.
Is there another library in which your same setup handles TPM assertions just fine? I'd be curious to compare notes.
Can you show me how you're calling generateAttestationOptions()? That'll help me recreate your conditions.
For that matter would you be able to provide attestation options from a WebAuthn demo that does work? I wonder if there's an optimal set of Attestation options specifically for TPM that will generate a proper public key, and perhaps by attempting to simplify things I've chosen initialized values that can be tweaked to handle more use cases.
from simplewebauthn.
I put in some time yesterday trying to get my Windows 10 PC to fix that "Attestation: Not ready" issue. Even after (finally) upgrading to 2004, enabling Secure Boot, and resetting TPM, though, I still can't get it to show "Ready".
I discovered afterwards that in this state I've actually been getting "packed" attestations! It's still true that the public key the authenticator returns is malformed (it also means I haven't actually been able to test SimpleWebAuthn's TPM support in real-world conditions! 😬)
I know I've asked for a lot of data from you, but I have another request: can you provide a raw attestation using those above options? I'd love to dig into it to see if it is indeed a TPM attestation, or a Packed attestation like I've been getting.
from simplewebauthn.
@yaron14 That's a "none" type attestation:
{
"id": "QdiHnAdxCTeVpw2Up2QYdbTG1fQFLwfdELRHvyyZg10",
"rawId": "QdiHnAdxCTeVpw2Up2QYdbTG1fQFLwfdELRHvyyZg10",
"response": {
"clientDataJSON": {
"type": "webauthn.create",
"challenge": "-8Gevc35e9YkzlocNCn8qEgL7VKd6Rx9ZsslNL8Ia6A",
"origin": "https://dev.netpassport.io",
"crossOrigin": false
},
"attestationObject": {
"fmt": "none",
"attStmt": {},
"authData": {
"rpIdHash": {
"type": "Buffer",
"data": [213,36,114,79,21,247,101,19,229,129,89,180,26,21,73,6,86,200,84,204,250,176,204,76,224,22,212,50,223,131,88,103]
},
"flagsBuf": {
"type": "Buffer",
"data": [
69
]
},
"flags": {
"up": true,
"uv": true,
"at": true,
"ed": false,
"flagsInt": 69
},
"counter": 0,
"counterBuf": {
"type": "Buffer",
"data": [0,0,0,0]
},
"aaguid": {
"type": "Buffer",
"data": [0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0]
},
"credentialID": "QdiHnAdxCTeVpw2Up2QYdbTG1fQFLwfdELRHvyyZg10",
"credentialPublicKey": "pAEDAzkBACBZAQDJyyyXuhZ-roqX0j8JSUkAwO-BH-KS-nq6AnG5AJOWYnf30DOh6ckys38Zy51wh1W-KilTBMiKlVl-xesdFKFleH2GhLC3ofFzyFjLZ8ew46Fh5DWTumF5kP9T-hsCS5lrfUj_QSqSRMASAonQwjDQ1ApBwv1K-oHRy-jCPWP-YB-ARznX1INKq19SR5fyJ_fpjXSMk-iT6J5zMUoBCflX_RWFICgJRcz2Cw0Cs6jYrwHFTw3mDAVackhgiQQdAHE7YgLjDlbXjB-1TViyHSTM1YVIBHihsqZRVkxKvTike77dt39odp1N33MJS2uYUHdseQKA5iJ2lg2nLTEuIkNZIUMBAAE"
}
}
},
"type": "public-key"
}attestationType: 'none' in your call to generateAttestationOptions() will only get back from the authenticator the most basic of attestations - your browser will never attempt an TPM attestation.
Can you try again with attestationType: 'direct'?
from simplewebauthn.
I'm getting the following error:
Error: Certificate contained incomplete subjectAltName data (TPM)
It's from verifyTPM.js file
from simplewebauthn.
Aha, an actual TPM attestation appears. Can you share that here?
from simplewebauthn.
{ "id": "LVwzXx0fStkvsos_jdl9DTd6O3-6be8Ua4tcdXc5XeM", "rawId": "LVwzXx0fStkvsos_jdl9DTd6O3-6be8Ua4tcdXc5XeM", "response": { "attestationObject": "o2NmbXRjdHBtZ2F0dFN0bXSmY2FsZzn__mNzaWdZAQAVTQGgcWtxs9VV4i1gQTcdXfoyZwupUnZjebIIzuq77nBe_EyxS4Fh8Go2vCdVnpHLXHsVct1ISZ8fmSB31YrnuaHpvxjTN-k0t3ynOwJY9SZd4uxX9KQUOMpjhWsQczpNL72J7wd4VckeU6oHvq-z9x6Oqfk1KbmzRu-ZdrUikYkM1uCXqk9h0P1MpeaoxFoLiS-2Vz1MZENB2-N-tC_ljwoUsAOBiE3MRfp2e_LCe4oRWCvhJn7qiVglQOnQWTtoky_FOKqJtPqt59v74C3rin8reNmNwXD1l0XljOYQaujLOMGut63CwtlpAgBN8IPHNWnukzv0X5VY0KjBT6DbY3ZlcmMyLjBjeDVjglkFxDCCBcAwggOooAMCAQICEGoHJ5pU80VnnGzPa5PrxlkwDQYJKoZIhvcNAQELBQAwQTE_MD0GA1UEAxM2RVVTLVNUTS1LRVlJRC0xQURCOTk0QUI1OEJFNTdBMENDOUI5MDBFNzg1MUUxQTQzQzA4NjYwMB4XDTIwMDgyNzE1MTIzMFoXDTI1MDMyMTIwMjkxNVowADCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAKkVhLA9cKyViKaVr6wwKqzty1AKR0VJGa3BB3QF7IfK81mfqv-x31Y0V0zPioxYgPHHfF4j4XPm5mVlQI9PluM828elk86kwPV-OFlhIX7nM1Hy9NQtgnfyV-7Kxmb3pKe2TI937XrtuJj0pKUav3g0RtPUZDywpWBVDCI4AopqLVyys8bse_bZdDI-l8IDqpzptL1kfmH2WG6rtCIyVimGQS3UtgkNpl-8FeDXOc3ciAYdY9MUHfE6QmFpwXn_qo_4x0VR1wiBKyK0ZACTAm96io_iskeyig3OGR_SEd2OeThYQtoJoAfZvBzSs3eTVTAsZ8unKnGjkss7eCF48Q8CAwEAAaOCAfMwggHvMA4GA1UdDwEB_wQEAwIHgDAMBgNVHRMBAf8EAjAAMG0GA1UdIAEB_wRjMGEwXwYJKwYBBAGCNxUfMFIwUAYIKwYBBQUHAgIwRB5CAFQAQwBQAEEAIAAgAFQAcgB1AHMAdABlAGQAIAAgAFAAbABhAHQAZgBvAHIAbQAgACAASQBkAGUAbgB0AGkAdAB5MBAGA1UdJQQJMAcGBWeBBQgDMFkGA1UdEQEB_wRPME2kSzBJMRYwFAYFZ4EFAgEMC2lkOjUzNTQ0RDIwMRcwFQYFZ4EFAgIMDFNUMzNIVFB4QUhBNjEWMBQGBWeBBQIDDAtpZDowMDQ3MDAwNDAfBgNVHSMEGDAWgBS4X9VnypLEDs8M2B9tPwNVbzimUTAdBgNVHQ4EFgQUSk_obuVTgSLFuag0uCvjqcyeFPIwgbIGCCsGAQUFBwEBBIGlMIGiMIGfBggrBgEFBQcwAoaBkmh0dHA6Ly9hemNzcHJvZGV1c2Fpa3B1Ymxpc2guYmxvYi5jb3JlLndpbmRvd3MubmV0L2V1cy1zdG0ta2V5aWQtMWFkYjk5NGFiNThiZTU3YTBjYzliOTAwZTc4NTFlMWE0M2MwODY2MC9hYmQ2MTVmMi0xNThhLTQ1OGUtYTE1NS03YzRjOGNiMTNjNjUuY2VyMA0GCSqGSIb3DQEBCwUAA4ICAQDYZJbtNQICOEg3N3UULml0qfQyuitzuVZJ59nvhhwHH6SsWLXhoZVgKaV3zOd00nJPVnX8uilmX2o9qkNi1ODO7WQ-wN2_jVtNsVDu1mgox6T6NeWzel-EbJdkg2kiwUaO639Yu_Xc8FUKNtUp-9fuF2p31uoYo-Nw-H58rbYOdsiOQ-SPYI4zbdjssntKyI6MAT_j1KAKv0Gbh5SvKM4aEmZA0v0dHXuxoH6kFVHLeNdwLe0cG__K9rCw5CKOD0zFMnKRx6LfNzaZ0OedM9skVjHPqR3qEfwGFXQzrfVGFzrri2vaE9bo2Q-cREY6ITX6kUJpkSc6Iz96hxpSxyIxN1faSeblMETRJD4pV0PtJGZb4GOeng0lQ8l4IkBlBgx-I27Ks_tTsf2owNkVOWTViWZLYLon0l_LhNKuuGJkjB0whvccBB4DiQPTckuCeFoB8IH5wAR__A_y33_zBR0fYWnVlEXWwtMO-vGRYQLPuK6j30MWBjPEvtujsS1gwJUhXnd3GENHaXtrQHnyZgLzRCHSeJy6SjI64Jm86VMMalvLJEbGrvjfs-vKnBKAoK_9JcK-tmx4pIJIm1gtOx-J59bfpLjgueBqpvVl3dz1r9dCXrRlsCCeqtXOFPK5lgJz3sxXyDxAT-Np52S1pfrui1i2VvnHB-YEM83nubdz01kG7zCCBuswggTToAMCAQICEzMAAAI5-btqHUlkR38AAAAAAjkwDQYJKoZIhvcNAQELBQAwgYwxCzAJBgNVBAYTAlVTMRMwEQYDVQQIEwpXYXNoaW5ndG9uMRAwDgYDVQQHEwdSZWRtb25kMR4wHAYDVQQKExVNaWNyb3NvZnQgQ29ycG9yYXRpb24xNjA0BgNVBAMTLU1pY3Jvc29mdCBUUE0gUm9vdCBDZXJ0aWZpY2F0ZSBBdXRob3JpdHkgMjAxNDAeFw0xOTAzMjEyMDI5MTVaFw0yNTAzMjEyMDI5MTVaMEExPzA9BgNVBAMTNkVVUy1TVE0tS0VZSUQtMUFEQjk5NEFCNThCRTU3QTBDQzlCOTAwRTc4NTFFMUE0M0MwODY2MDCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBANviI_mGj6lxn4v5fOlFLVlWXpb03ZoSzZAaDLUDvwm-v_dVUug5TL4qKIh4OafL-UxV0jGWO0ii8_bTGoF_kGKr7FrHoH-BMiebKXV9HpbF-g584GCWesqUuuayad3EfbvTxLRuAIYfnSXorscQhNzANCRu9_zdPTJ6Q5bWyHv0mz2nHrpN0Ds9hJrRJSJdAESwWbdAxaNTU6-Pnv2PHgLTT_cJzsXGcVzp6Hq1a6S_C9m2-iSwzVIiHX7oFS8eXqLs06gCd7lVms_M1wggpdo5mjB2kDenYN8YEmUXqt1I1RIdTINdgQcdGIFAVWCPo2s0HtXmz1Jzd0pQTxsPOcMNFvm7THf2Tqyc_ui7UqUKDpvwDe_7b4k0fUfsFGr0CuFgRHN7oKtbjEOmBUJhRqoc9ewshoUhmd9FjvTRHvvNm5Qy4KDMT62uRIuGJ5H-YJ_yYzBsXY28q9T1orJ06NSV8tYDi8mjUudjBWRQ5QpqoGxQzTeYqIcCOFtsAmk9H5V0TUZ2Kp1i1Mcb-TGmUe57yORuOs9PT0mK9U8lkyMC73mmJ75a53S316jBrlWIpMdNt2Lw-Vu_R1v-zAuJGWVLb99PfU2WQg0qob0-cJK6yFnVHTqYU3WmMshyA0ZfXBOk28dVNSINxheFvUZL-h5Jwv4e-WKJVoTfoPv9k6QlAgMBAAGjggGOMIIBijAOBgNVHQ8BAf8EBAMCAoQwGwYDVR0lBBQwEgYJKwYBBAGCNxUkBgVngQUIAzAWBgNVHSAEDzANMAsGCSsGAQQBgjcVHzASBgNVHRMBAf8ECDAGAQH_AgEAMB0GA1UdDgQWBBS4X9VnypLEDs8M2B9tPwNVbzimUTAfBgNVHSMEGDAWgBR6jArOL0hiF-KU0a5VwVLscXSkVjBwBgNVHR8EaTBnMGWgY6Bhhl9odHRwOi8vd3d3Lm1pY3Jvc29mdC5jb20vcGtpb3BzL2NybC9NaWNyb3NvZnQlMjBUUE0lMjBSb290JTIwQ2VydGlmaWNhdGUlMjBBdXRob3JpdHklMjAyMDE0LmNybDB9BggrBgEFBQcBAQRxMG8wbQYIKwYBBQUHMAKGYWh0dHA6Ly93d3cubWljcm9zb2Z0LmNvbS9wa2lvcHMvY2VydHMvTWljcm9zb2Z0JTIwVFBNJTIwUm9vdCUyMENlcnRpZmljYXRlJTIwQXV0aG9yaXR5JTIwMjAxNC5jcnQwDQYJKoZIhvcNAQELBQADggIBAEGq_ihs92tT3nfAgFCU2dtGjmqTqRA3Jx_1cPGoz6FFhirdj7i1webPivoyoUu3pL8KSMtCY3HBlrk6N4QOJDnrWM49t6lEklm5_9sYvmpe587vuEBTr8Gb-0KZfp0FK3EKenpE0THK8F90hanivMgMrVfR6UiQiFeG18XJ5rJeXxPcEH_fY4rVnpDCdVMeaBcrAykVA8WMZj6uvUoyflmJC4TC2ZD6AiKQjZy2DE3hKHbXgsM2wqMqUuX-PI_jS9pq28B6PFf6hY_7YsOhOM6E8roS9DAqSpSpNSx9EcdoH0eqV0MGcHmMtjtdV_PzwCzF3kGZ9t1ViuQTysnsaZMTSPBf2i79-6kbkt5JcTeMP8IICoMl8W4K41WFlpotosCh7v4jO2kiA_3Mit20U42EpqzgHgfl1_nLueOat4RwoZPWAh7-2yh899Rib4B1yNg1JgzLhO27ld9_1bsAlpcy57roKbUaUYG7BNEhdjRtHpOWH5ZTX1ye852CHDk2Wa7JPFNKZ2Vuv6asPtqyp2MHF-Fb2moxn_u06qGXCG6yaPNydpnoAEaIJuE8Byt4Sdp5Or1vylygqO00zNsT4lGbPQOsx_Yy4RFd4cX9nnrNBrnm_OADMfRKqTt5AbBkaJ9udqHM7BdBndRbTp3lRtRrYCojtXqJfCeWZZdW7JjjZ3B1YkFyZWFZATYAAQALAAYEcgAgnf_L82w4OuaZ-5ho3G3LidcVOIS-KAOSLBJBWL-tIq4AEAAQCAAAAAAAAQC0ciFRFbWRy-FM8K7FKCWx1xQ9lkpjErkYnun5Fbu6h8OeXpPdngMam85Kf56JRuwKPtwz-cToz-wjjQ7Bpg--EaBE4_WEoQc6lfEoShDSAa2gvf1rKhOoe4quaRu3lxpqGCp5qRSbKET3SWYSphrfo6AD_qQ2X8safYhnRb7WatyTP42qKCwzWX0J4JovMG4d_zteT1q3wljbp2XGxcF9qPTHhqSjj2h20DeP4dDS-TZzLsytSYCswpBE-WvEElcIslIhmFdmnbRY5UMECR9tkyp3NfwHBGqP_uZVwilxRC3rVTuGWSNm9pdqrgADnLftVeKSNGU22tnMxyNb-4MVaGNlcnRJbmZvWKH_VENHgBcAIgALI_9Gp39SuKvSJvllxwHyGHhtaaF8TtuCHdfJEBqgCJQAFHAs7LsTg6ywAmOxET_5IxypMjRjAAAAAAKIAWoDEFBLdFFCfQE1hhRhFj_igAAiAAsbzG7XFehetxw_1Xqqsm9xjRGD8dbXDYq2q0yK2hdJagAiAAvbuEFNLlj6-ytEKRA8KlzE-x4DlyoBuskc-iQXv4NZ52hhdXRoRGF0YVkBZ9Ukck8V92UT5YFZtBoVSQZWyFTM-rDMTOAW1DLfg1hnRQAAAAAImHBYytxLgbbhMN5Q3L6WACAtXDNfHR9K2S-yiz-N2X0NN3o7f7pt7xRri1x1dzld46QBAwM5AQAgWQEAtHIhURW1kcvhTPCuxSglsdcUPZZKYxK5GJ7p-RW7uofDnl6T3Z4DGpvOSn-eiUbsCj7cM_nE6M_sI40OwaYPvhGgROP1hKEHOpXxKEoQ0gGtoL39ayoTqHuKrmkbt5caahgqeakUmyhE90lmEqYa36OgA_6kNl_LGn2IZ0W-1mrckz-NqigsM1l9CeCaLzBuHf87Xk9at8JY26dlxsXBfaj0x4ako49odtA3j-HQ0vk2cy7MrUmArMKQRPlrxBJXCLJSIZhXZp20WOVDBAkfbZMqdzX8BwRqj_7mVcIpcUQt61U7hlkjZvaXaq4AA5y37VXikjRlNtrZzMcjW_uDFSFDAQAB", "clientDataJSON": "eyJ0eXBlIjoid2ViYXV0aG4uY3JlYXRlIiwiY2hhbGxlbmdlIjoiVmZtWlhLRHhxZG9YRk1IWE8zU0UyUTJiOHU1S2k2NE9MX1hJQ0VMY0dLZyIsIm9yaWdpbiI6Imh0dHBzOi8vZGV2Lm5ldHBhc3Nwb3J0LmlvIiwiY3Jvc3NPcmlnaW4iOmZhbHNlfQ" }, "type": "public-key" }
from simplewebauthn.
YAY!
Thank you! I'm waiting for the new release :)
from simplewebauthn.
@yaron14 This issue should be fixed as of the newly-published v0.9.0. RSA support in general should be greatly improved, even if fmt is "none" as in an earlier example above.
And while I have your attention, I've been unable to procure a device capable of producing actual TPM attestations. I'm hoping you can test out both attestations and assertions with the new version of the library and report back on how it goes.
Also, I'd like to request a TPM assertion response from you as well. I need one to round out my unit testing so I can feel more confident about being able to support these types of devices for both scenarios.
from simplewebauthn.
@MasterKale, its working superbly! Thanks.
You should have had to inform me about the change of serviceName property though as I received an error in startAttestation and had no idea what to do until I looked at the changes you've made to the new version :)
This is the TPM assertion you've asked for:
{ "id": "7NtSkjQY3AsVB2SWw0jZhYerjOAJo4tqOYXM-dNw7FE", "rawId": "7NtSkjQY3AsVB2SWw0jZhYerjOAJo4tqOYXM-dNw7FE", "response": { "authenticatorData": "1SRyTxX3ZRPlgVm0GhVJBlbIVMz6sMxM4BbUMt-DWGcFAAAAAg", "clientDataJSON": "eyJ0eXBlIjoid2ViYXV0aG4uZ2V0IiwiY2hhbGxlbmdlIjoiMS1tUVp5U2x5MDdmRlhwY19OMGYxYUZEa19uUnJXWUIwV1FYX3dZOTBMYkJXeFU4QmRTaUNyZnFXRXRUSWY3Ym51VFVPN1M3WTlsQm5fS21ldlJuWGciLCJvcmlnaW4iOiJodHRwczovL2Rldi5uZXRwYXNzcG9ydC5pbyIsImNyb3NzT3JpZ2luIjpmYWxzZX0", "signature": "qKfneac-UwlxCnxd_D23VHO8RAKbaBG0s1dTIi2FrLyOunyr7mzpJgQT-iKjaTl5Vh8lJrBtM7J88zj2r8KuDXHqPTDsuNKqP_-RezJq6Jbr8ctlx-u8hl3CVhv1hkrSQjb1Oisk54esJ7BYJowojLT6Q1e5002JBC0Urt0ic7IDZ65YDle2Xuu30FXSvQrbfWe51G0LDgnAZKpCE8Fga7Arp8Kh82EXoZ5CpK9YqDHe_WYeCYXLF39-Vi03_eVAyO89aoVaI0gUKeifFcHnf3L1p88PjjUK0JbItyhvqXz1CjG5Adfg6hMZSOID11AWm3mcU_bCM-f9f0nre9e2hQ", "userHandle": "cXM4VjR6VDUxeHRWSWZzaGxzeVJRS3o1enBscExqWTJpRGlmWjk1MEdGdz0" }, "type": "public-key" }
from simplewebauthn.
You should have had to inform me about the change of serviceName property though as I received an error in startAttestation and had no idea what to do until I looked at the changes you've made to the new version :)
Yikes, sorry about that! I'll make a point of highlighting things like that when addressing future issues 🙇
This is the TPM assertion you've asked for:
Argh, the id in the assertion is different than the id in the attestation from a few days ago. I suppose I should have asked for a pair of attestation+assertion as the assertion is no good if I don't have the public key from the preceding attestation. Can I bother you for another set? 😅
from simplewebauthn.
Closing this out as the issue has been confirmed resolved 🚀
from simplewebauthn.
Related Issues (20)
- Cannot find module 'cbor-x/index-no-eval' or its corresponding type declarations. HOT 9
- ignore `node:crypto` import with webpack in `@simplewebauthn/server` HOT 8
- Update minimum Node support to v20+ HOT 3
- library reports lack of support to webauthn in mobile chrome but webauthn seems to work if using reference site HOT 8
- Using Android devices without non-Google Password managers fail to authenticate HOT 11
- Change signature of `decodeClientDataJSON` to accept `Base64URLString` as paramater HOT 2
- Improve ergonomics of `excludeCredentials` and `allowCredentials` HOT 3
- Remove footgun related to random user IDs HOT 16
- Update `getWebCrypto()` for Node 20 HOT 2
- cross-platform authenticator usage on android 14 HOT 1
- Default `userDisplayName` to empty string when not specified HOT 1
- Handle undefined `PublicKeyCredential` in `browserSupportsWebAuthnAutofill` helper HOT 1
- Discrepancy between example code and docs HOT 4
- get public key as string
- Make rpID required when generating authentication options HOT 1
- Clean up some docstrings in @simplewebauthn/server
- Rename `AuthenticatorDevice` type and usage
- Parsing the attestation data explicitly HOT 3
- Changed userHandle behavior v10 breaks definitely with existing registrations HOT 2
- RequireUserVerification Is Not Documented HOT 2
Recommend Projects
-
 React
React
A declarative, efficient, and flexible JavaScript library for building user interfaces.
-
Vue.js
🖖 Vue.js is a progressive, incrementally-adoptable JavaScript framework for building UI on the web.
-
 Typescript
Typescript
TypeScript is a superset of JavaScript that compiles to clean JavaScript output.
-
TensorFlow
An Open Source Machine Learning Framework for Everyone
-
Django
The Web framework for perfectionists with deadlines.
-
Laravel
A PHP framework for web artisans
-
D3
Bring data to life with SVG, Canvas and HTML. 📊📈🎉
-
Recommend Topics
-
javascript
JavaScript (JS) is a lightweight interpreted programming language with first-class functions.
-
web
Some thing interesting about web. New door for the world.
-
server
A server is a program made to process requests and deliver data to clients.
-
Machine learning
Machine learning is a way of modeling and interpreting data that allows a piece of software to respond intelligently.
-
Visualization
Some thing interesting about visualization, use data art
-
Game
Some thing interesting about game, make everyone happy.
Recommend Org
-
Facebook
We are working to build community through open source technology. NB: members must have two-factor auth.
-
Microsoft
Open source projects and samples from Microsoft.
-
Google
Google ❤️ Open Source for everyone.
-
Alibaba
Alibaba Open Source for everyone
-
D3
Data-Driven Documents codes.
-
Tencent
China tencent open source team.


from simplewebauthn.