Comments (19)
Could be related to this http://forum.cheatengine.org/viewtopic.php?t=606385
This is the line that refers to the minimum address: https://github.com/erfg12/memory.dll/blob/master/Memory/Class1.cs#L1503
The debug console will tell you most of the information. Like for example, where the main module base is at (where it starts the scan). If you could post that information please.
Join our Discord chat after too.
from memory.dll.
Thanks for quick answer.
Here's what showed up in console when I pressed a button:
[DEBUG] memory scan starting... (base:0x0000000140000000 max:00000001f571b000 time:5:24:31 PM)
I still don't know what to do with this information to make it work.
from memory.dll.
It shows that your scan is starting at 0x140000000 (regardless of your start address provided). Your screenshot shows you're looking for 0x2F4CAA9C which is below the base module address, which is the issue Dark Byte and I were talking about on the forum.
You could download the Memory.dll source code and change the line at https://github.com/erfg12/memory.dll/blob/master/Memory/Class1.cs#L1503 with
Int64 proc_min_address_l = 0;
and see if it manages to read from that address.
Also, don't read to the max "0x7FFFFFFFFFFFFFFD" that will cause an overflow. Just scan starting from 0x20000000 and the length of 0x20000000.
from memory.dll.
Yup, looks incorrect. I don't see the line I mentioned modified.
from memory.dll.
Thanks! It works now. In the past I modified a string on the wrong line.
from memory.dll.
Seriously, the AoB scan works now?
from memory.dll.
Yes, when I did it the correct way and modified it on line 1503, it started working.
from memory.dll.
wow, thanks. I'll have to fix that.
from memory.dll.
Is the AoB in the main module or is it a part of a different module? If it's a different module wouldn't that cause it to be before the base address?
from memory.dll.
Dark Byte was describing it like it was a "copy" from another module to "temporary" memory. So it's basically unmapped memory. I think this only happens in 64bit games. I haven't seen this happen in 32bit ones anyways.
from memory.dll.
After I press a button for the first time, it finds the correct address:

But after I press same button second time, I get this error:

Code is just as before:
private void Button_Click(object sender, EventArgs e)
{
long foundAddr = m.AoBScan("0x20000000", 0x10000000, "AF 04 00 00 B0 04 00 00 05 00 00 00 00 00 00 00 00 00 00 00").Result;
MessageBox.Show("I found the address! Here it is: " + "0x" + longToHex(foundAddr));
}
from memory.dll.
If you open memory.dll source code, go to the project settings, select Debug on the left, check the radio button for "Start external program:" and navigate to your trainer executable. Then press the Start (Debug) button it should start memory.dll in a debug state and point you to the exact line that is causing the issue(s). Could you screenshot those for me please?
from memory.dll.
Is this happening when debugging and quickly closing during an AoB scan? It's possible this is happening if there are multiple tasks from the scan still open and running while trying to do something else.
from memory.dll.
If you open memory.dll source code, go to the project settings, select Debug on the left, check the radio button for "Start external program:" and navigate to your trainer executable. Then press the Start (Debug) button it should start memory.dll in a debug state and point you to the exact line that is causing the issue(s). Could you screenshot those for me please?
So I opened Memory.dll project in second instance of VS, went to the project settings of memory.dll, selected Debug on the left, checked radio button for start external program, navigated to my trainer executable, then pressed start button in debug mode. It started my trainer, I pressed a button, it found correct address, then I pressed a button second time and I got the same error:

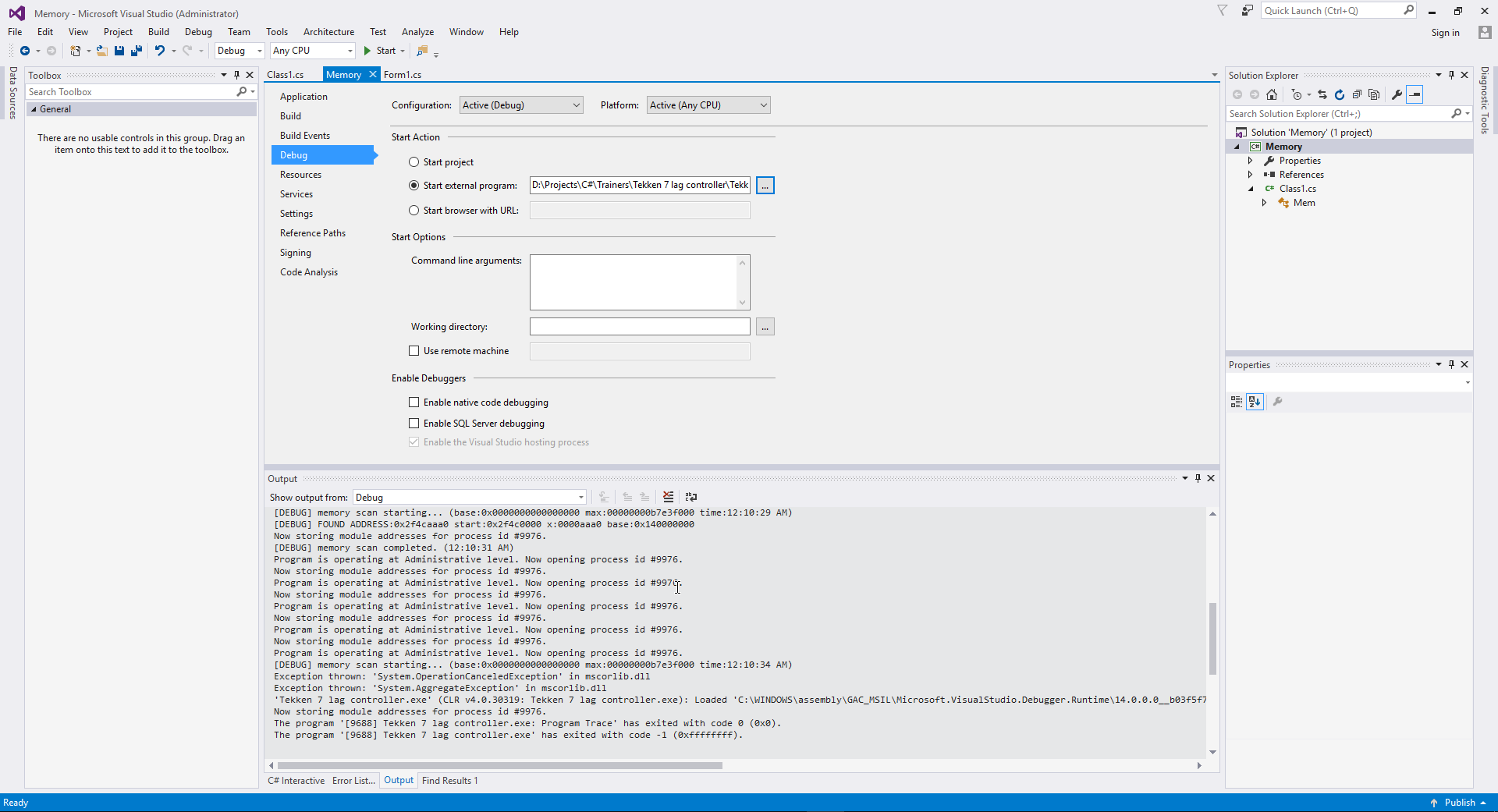
Console:
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
[DEBUG] memory scan starting... (base:0x0000000000000000 max:00000000b7e3f000 time:12:10:29 AM)
[DEBUG] FOUND ADDRESS:0x2f4caaa0 start:0x2f4c0000 x:0000aaa0 base:0x140000000
Now storing module addresses for process id #9976.
[DEBUG] memory scan completed. (12:10:31 AM)
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
[DEBUG] memory scan starting... (base:0x0000000000000000 max:00000000b7e3f000 time:12:10:34 AM)
Exception thrown: 'System.OperationCanceledException' in mscorlib.dll
Exception thrown: 'System.AggregateException' in mscorlib.dll
'Tekken 7 lag controller.exe' (CLR v4.0.30319: Tekken 7 lag controller.exe): Loaded 'C:\WINDOWS\assembly\GAC_MSIL\Microsoft.VisualStudio.Debugger.Runtime\14.0.0.0__b03f5f7f11d50a3a\Microsoft.VisualStudio.Debugger.Runtime.dll'. Skipped loading symbols. Module is optimized and the debugger option 'Just My Code' is enabled.
Now storing module addresses for process id #9976.
from memory.dll.
I think that second scan you're trying to do is happening at the same time the 1st scan is trying to complete and causing issues. You should try to use AoB scans sparingly. Use the await operator so the second scan waits for the first one to complete.
The next push I will be doing to the repo will have this base address fix, an AggregateException catch, and a potentially faster scan. I'm currently looking over the code to see if I can maybe shrink a few lines of code as well. Maybe clean it up a bit.
from memory.dll.
This time I used await operator and waited a minute between buttons presses:
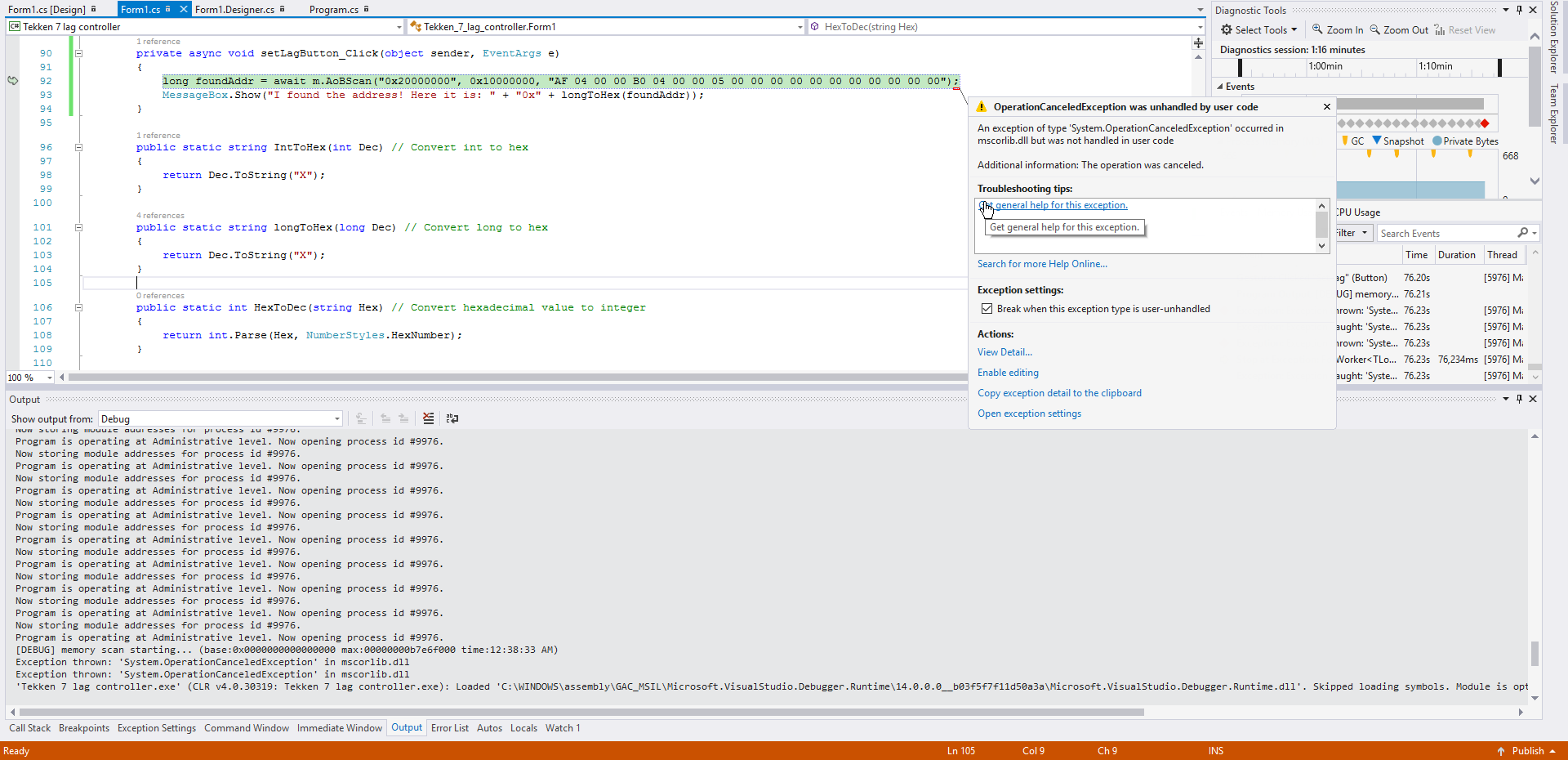
Output:
'Tekken 7 lag controller.exe' (CLR v4.0.30319: DefaultDomain): Loaded 'C:\WINDOWS\Microsoft.Net\assembly\GAC_64\mscorlib\v4.0_4.0.0.0__b77a5c561934e089\mscorlib.dll'. Skipped loading symbols. Module is optimized and the debugger option 'Just My Code' is enabled.
'Tekken 7 lag controller.exe' (CLR v4.0.30319: DefaultDomain): Loaded 'D:\Projects\C#\Trainers\Tekken 7 lag controller\Tekken 7 lag controller\bin\Debug\Tekken 7 lag controller.exe'. Symbols loaded.
'Tekken 7 lag controller.exe' (CLR v4.0.30319: Tekken 7 lag controller.exe): Loaded 'C:\WINDOWS\Microsoft.Net\assembly\GAC_MSIL\System.Windows.Forms\v4.0_4.0.0.0__b77a5c561934e089\System.Windows.Forms.dll'. Skipped loading symbols. Module is optimized and the debugger option 'Just My Code' is enabled.
'Tekken 7 lag controller.exe' (CLR v4.0.30319: Tekken 7 lag controller.exe): Loaded 'C:\WINDOWS\Microsoft.Net\assembly\GAC_MSIL\System\v4.0_4.0.0.0__b77a5c561934e089\System.dll'. Skipped loading symbols. Module is optimized and the debugger option 'Just My Code' is enabled.
'Tekken 7 lag controller.exe' (CLR v4.0.30319: Tekken 7 lag controller.exe): Loaded 'C:\WINDOWS\Microsoft.Net\assembly\GAC_MSIL\System.Drawing\v4.0_4.0.0.0__b03f5f7f11d50a3a\System.Drawing.dll'. Skipped loading symbols. Module is optimized and the debugger option 'Just My Code' is enabled.
'Tekken 7 lag controller.exe' (CLR v4.0.30319: Tekken 7 lag controller.exe): Loaded 'D:\Projects\C#\Trainers\Tekken 7 lag controller\Tekken 7 lag controller\bin\Debug\Memory.dll'. Symbols loaded.
'Tekken 7 lag controller.exe' (CLR v4.0.30319: Tekken 7 lag controller.exe): Loaded 'C:\WINDOWS\Microsoft.Net\assembly\GAC_MSIL\System.Core\v4.0_4.0.0.0__b77a5c561934e089\System.Core.dll'. Skipped loading symbols. Module is optimized and the debugger option 'Just My Code' is enabled.
'Tekken 7 lag controller.exe' (CLR v4.0.30319: Tekken 7 lag controller.exe): Loaded 'C:\WINDOWS\Microsoft.Net\assembly\GAC_MSIL\System.Configuration\v4.0_4.0.0.0__b03f5f7f11d50a3a\System.Configuration.dll'. Skipped loading symbols. Module is optimized and the debugger option 'Just My Code' is enabled.
'Tekken 7 lag controller.exe' (CLR v4.0.30319: Tekken 7 lag controller.exe): Loaded 'C:\WINDOWS\Microsoft.Net\assembly\GAC_MSIL\System.Xml\v4.0_4.0.0.0__b77a5c561934e089\System.Xml.dll'. Skipped loading symbols. Module is optimized and the debugger option 'Just My Code' is enabled.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
[DEBUG] memory scan starting... (base:0x0000000000000000 max:00000000b7e6f000 time:12:37:18 AM)
[DEBUG] FOUND ADDRESS:0x2f4caaa0 start:0x2f4c0000 x:0000aaa0 base:0x140000000
Now storing module addresses for process id #9976.
[DEBUG] memory scan completed. (12:37:20 AM)
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
The thread 0x2cdc has exited with code 0 (0x0).
The thread 0x32a8 has exited with code 0 (0x0).
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
The thread 0x2070 has exited with code 0 (0x0).
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
Now storing module addresses for process id #9976.
Program is operating at Administrative level. Now opening process id #9976.
[DEBUG] memory scan starting... (base:0x0000000000000000 max:00000000b7e6f000 time:12:38:33 AM)
Exception thrown: 'System.OperationCanceledException' in mscorlib.dll
Exception thrown: 'System.OperationCanceledException' in mscorlib.dll
'Tekken 7 lag controller.exe' (CLR v4.0.30319: Tekken 7 lag controller.exe): Loaded 'C:\WINDOWS\assembly\GAC_MSIL\Microsoft.VisualStudio.Debugger.Runtime\14.0.0.0__b03f5f7f11d50a3a\Microsoft.VisualStudio.Debugger.Runtime.dll'. Skipped loading symbols. Module is optimized and the debugger option 'Just My Code' is enabled.
from memory.dll.
Try using Task.IsCompleted to see if it is really done.
https://msdn.microsoft.com/en-us/library/system.threading.tasks.task.iscompleted(v=vs.110).aspx
from memory.dll.
I tried to see if task is done using different methods:
Task<Int64> aobScanTask = m.AoBScan("0x20000000", 0x10000000, "AF 04 00 00 B0 04 00 00 05 00 00 00 00 00 00 00 00 00 00 00");
//await aobScanTask;
//aobScanTask.Wait();
//while (!aobScanTask.IsCompleted) { }
//long foundAddr = await aobScanTask;
long foundAdd = aobScanTask.Result;
MessageBox.Show("I found the address! Here it is: " + "0x" + longToHex(foundAddr));
They all throw either OperationCanceledException or AggregateException.
while (!aobScanTask.IsCompleted) { } doesn't throw any exceptions, but then either aobScanTask.Result throws AggregateException:

Or await aobScanTask throws OperationCanceledException:

What I am doing wrong here?
PS I am using last version of memory.dll you posted here few hours ago.
I understand that I should scan only once when process is opened, but what if I want to scan like 15 different AoBs? I also want to use AoB and not pointers because it will survive patches.
from memory.dll.
Can you compile & test the current version that was pushed to the repo?
from memory.dll.
Related Issues (20)
- WriteMemory with the option bytes crashes the game
- Discord Link Has Expired HOT 1
- Will writeMemory function cause Crash? HOT 1
- OpenProcess Always Returned NULL
- Have you translated the following C + + code?VirtualAlloc
- Add GetModuleToPointer HOT 2
- Fix GetCode now work in 32bit&64bit HOT 1
- Using custom AoB scan regions causes no results. HOT 1
- I am astonished HOT 1
- Can we hook functions with this library? HOT 1
- UNIT64 error HOT 1
- Is Cheat Engine and Cheat Table Support added ? HOT 7
- I have a reading error HOT 2
- Not a bug but I have a question HOT 1
- WriteMemory function doesn't work in specifical condition HOT 2
- I am having some issues! HOT 5
- How can i change opcode values inline, or load a full auto assembler script from cheat engine HOT 1
- issue HOT 1
- Estouro no AoBScan memory.dll C# / Overflow in AoBScan memory.dll C#
- Can't use memory read/write functions on addresses within module that has name containing "main" HOT 3
Recommend Projects
-
 React
React
A declarative, efficient, and flexible JavaScript library for building user interfaces.
-
Vue.js
🖖 Vue.js is a progressive, incrementally-adoptable JavaScript framework for building UI on the web.
-
 Typescript
Typescript
TypeScript is a superset of JavaScript that compiles to clean JavaScript output.
-
TensorFlow
An Open Source Machine Learning Framework for Everyone
-
Django
The Web framework for perfectionists with deadlines.
-
Laravel
A PHP framework for web artisans
-
D3
Bring data to life with SVG, Canvas and HTML. 📊📈🎉
-
Recommend Topics
-
javascript
JavaScript (JS) is a lightweight interpreted programming language with first-class functions.
-
web
Some thing interesting about web. New door for the world.
-
server
A server is a program made to process requests and deliver data to clients.
-
Machine learning
Machine learning is a way of modeling and interpreting data that allows a piece of software to respond intelligently.
-
Visualization
Some thing interesting about visualization, use data art
-
Game
Some thing interesting about game, make everyone happy.
Recommend Org
-
Facebook
We are working to build community through open source technology. NB: members must have two-factor auth.
-
Microsoft
Open source projects and samples from Microsoft.
-
Google
Google ❤️ Open Source for everyone.
-
Alibaba
Alibaba Open Source for everyone
-
D3
Data-Driven Documents codes.
-
Tencent
China tencent open source team.



from memory.dll.