This repository is dedicated to the research and implementation of REST Authentication using FastAPI.
FastAPI is a modern, fast (high-performance), web framework for building APIs with Python 3.6+ based on standard Python type hints. It’s gaining popularity due to its ease of use, speed, and scalability. In this repository, we focus on exploring and implementing REST Authentication using FastAPI.
Understanding the different methods of API authentication is a core competence for any would-be developer, data professional, or anyone else who wants to connect to external tools, data sources, or other resources.
API authentication is the process of verifying the identity of a user or other actor - in order to confirm that they have the necessary permissions for whatever they’re trying to do via an API.
Authentication allows API owners to do three things:
- Verify the identity of a client or user.
- Enable authorized clients and users can access the API.
- Prevent unauthorized access.
This is very tightly linked to another idea - authorization. Following on from authentication, this is how vendors govern which elements of their API clients and users can access.
Authorization is used for:
- Granting access and exposure to particular resources or data for different users.
- Governing what actions different users and clients can take with our API.
- Otherwise enforce defined access control policies.
From the perspective of someone accessing an API, we’re not too worried about how vendors implement authorization after authentication. But, it’s worth being aware that they might use our authentication data in order to determine what resources and actions we can access.
Now that we know what authentication is, let's see what are the most used authentication methods in REST APIs.
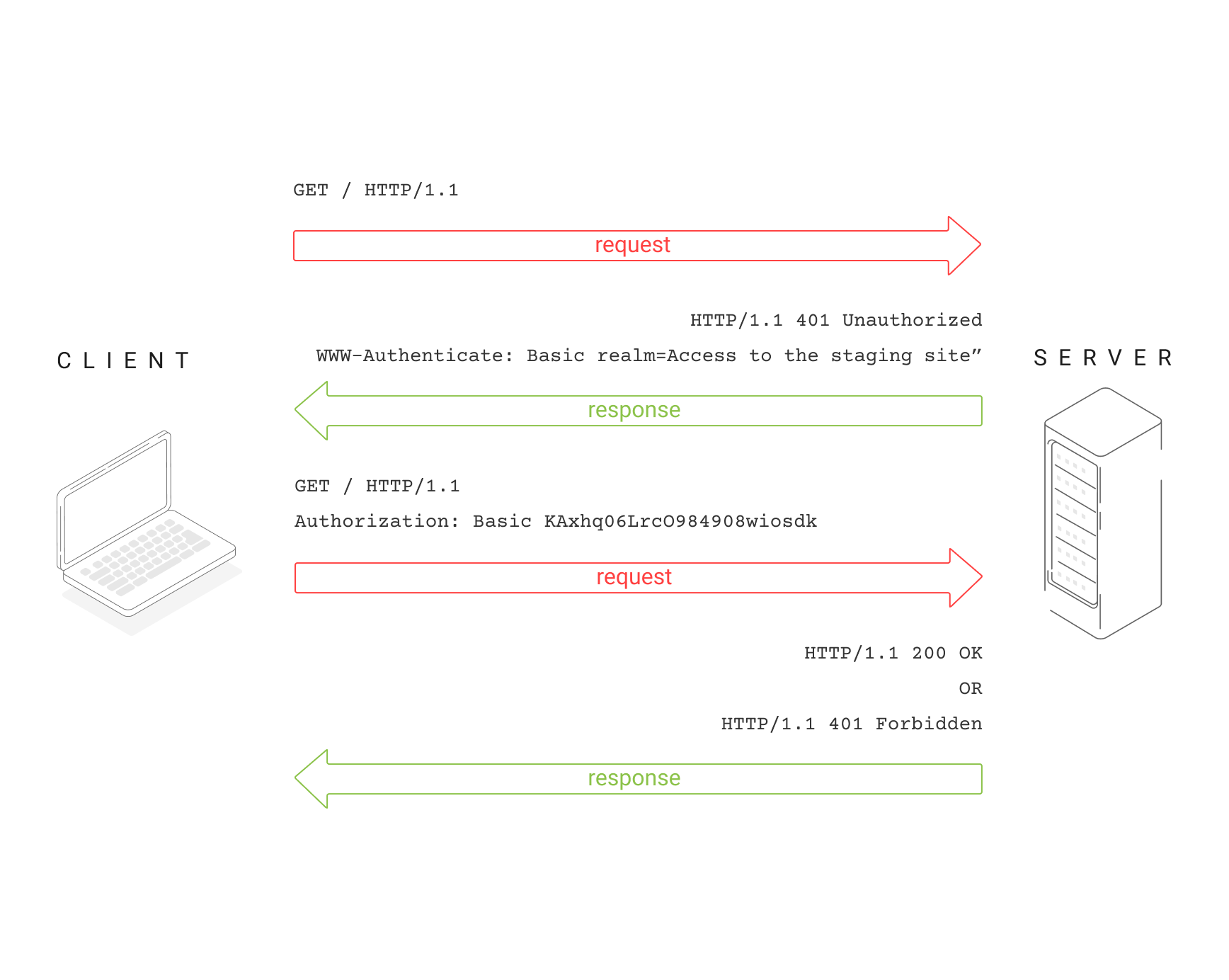
Basic authentication is the simplest form of authentication, and involves sending a username and password with each request. This is generally done using the HTTP authorization header, and the credentials are encoded using Base64.
This method does not require cookies, session IDs, login pages, and other such specialty solutions, and because it uses the HTTP header itself, there’s no need to handshakes or other complex response systems.
The username and password are encoded with Base64, which is an encoding technique that converts the username and password into a set of 64 characters to ensure safe transmission.
Basic authentication is a great solution for applications that require secure authentication and need to authenticate users quickly and easily. It is also a good choice for applications that require a user to be logged in before they can access certain resources.
Basic authentication sends the credentials in
plaintext, it is not recommended for use in theproductionenvironment.
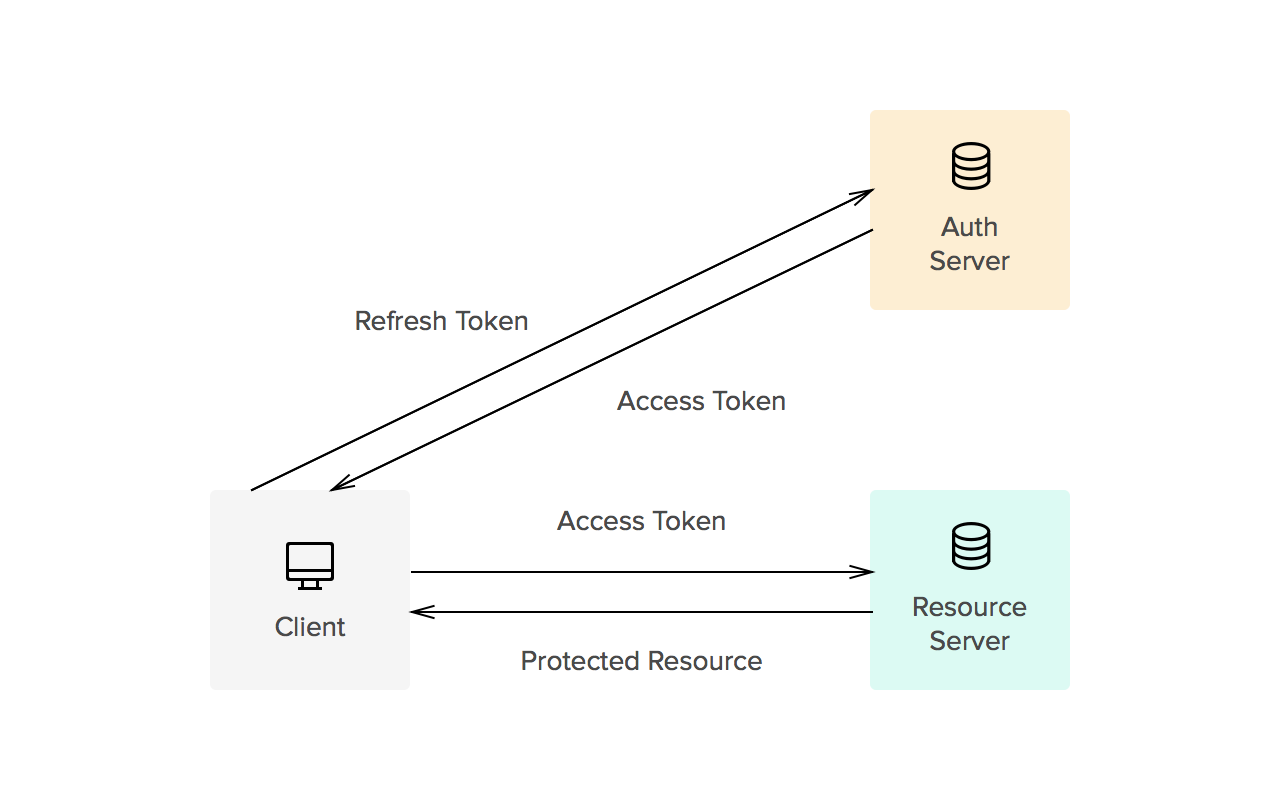
Bearer authentication (also called token authentication) is an HTTP authentication scheme that involves security tokens called bearer tokens.
“Bearer authentication” can be understood as “give access to the bearer of this token.”
The bearer token allowing access to a certain resource or URL and most likely is a cryptic string, usually generated by the server in response to a login request. The client must send this token in the Authorization header when making requests to protected resources
Similarly to Basic authentication, Bearer authentication should only be used over HTTPS (SSL).
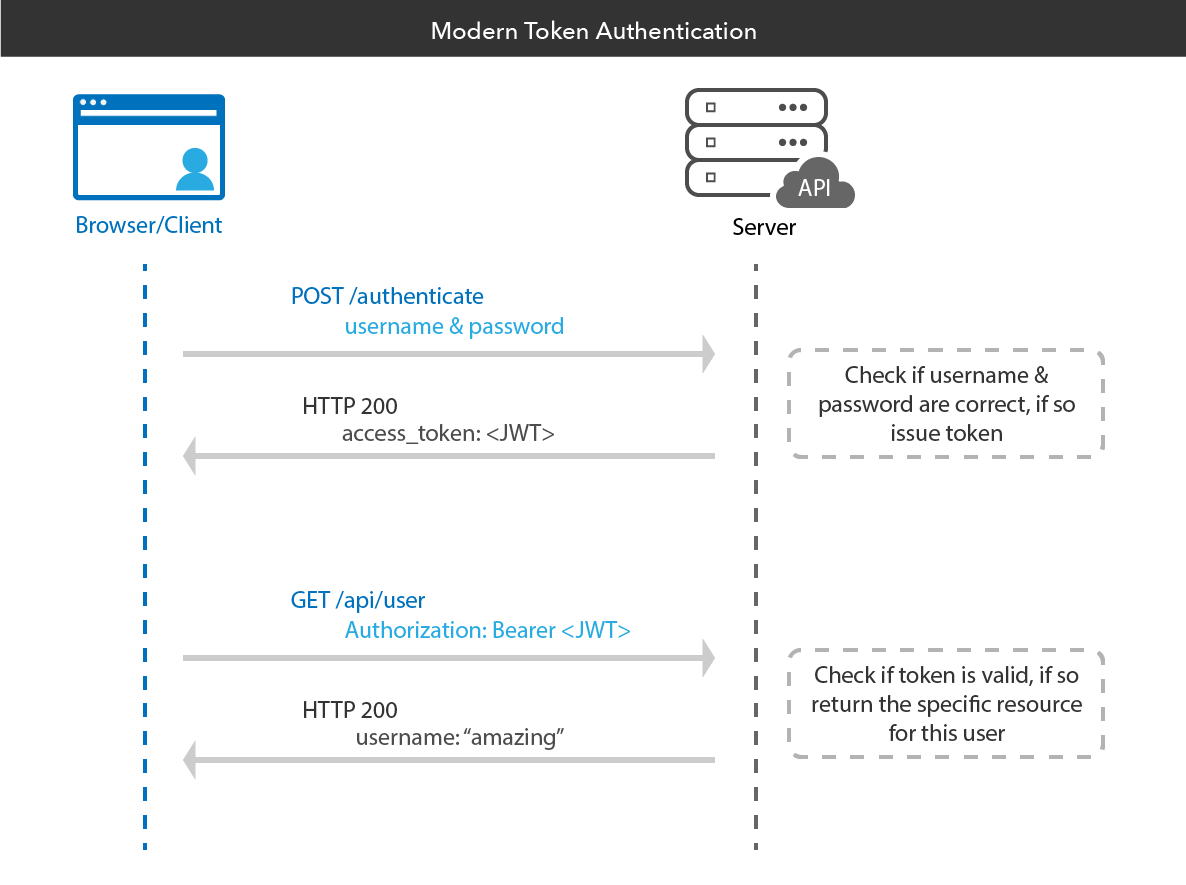
JSON Web Token (JWT) authentication is an API authentication method that uses tokens to authenticate API consumers. This API authentication method uses JSON data structures to store authentication information for API users, such as usernames and expiration dates.
JWT is an open standard that defines a compact and self-contained way for securely transmitting information between parties as a JSON object. This information can be verified and trusted because it is digitally signed. JWTs can be signed using a secret (with the HMAC algorithm) or a public/private key pair using RSA or ECDSA.
Although JWTs can be encrypted to also provide secrecy between parties, we will focus on signed tokens. Signed tokens can verify the integrity of the claims contained within it, while encrypted tokens hide those claims from other parties. When tokens are signed using public/private key pairs, the signature also certifies that only the party holding the private key is the one that signed it.
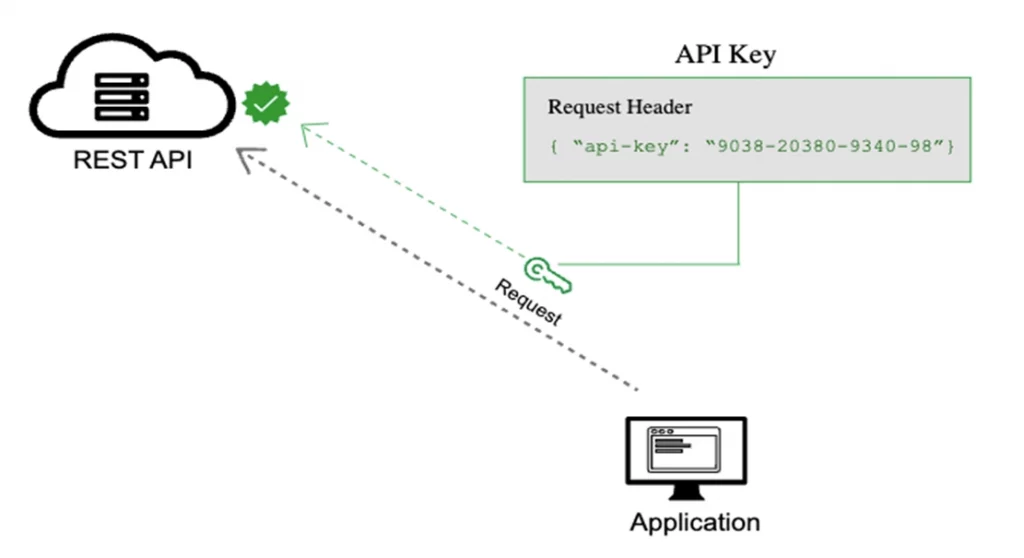
API Keys were created as somewhat of a fix to the early authentication issues of HTTP Basic Authentication and other such systems. In this method, a unique generated value is assigned to each first time user, signifying that the user is known. When the user attempts to re-enter the system, their unique key (sometimes generated from their hardware combination and IP data, and other times randomly generated by the server which knows them) is used to prove that they’re the same user as before.
API keys are widely used in the industry and became some sort of standard, however, this method should not be considered a good security measure.
API key authentication is relatively simple to implement and can be a good choice for small projects or for internal use. However, it does not provide the same level of security as other methods, such as OAuth, and is not recommended for use in public-facing applications.
Feel free to contribute to this project by providing suggestions, enhancing the code, or adding more resources. Your contributions are always welcome!
This project is for research purposes only. Please use the code responsibly and ensure to follow all security best practices when implementing authentication in a real-world application.