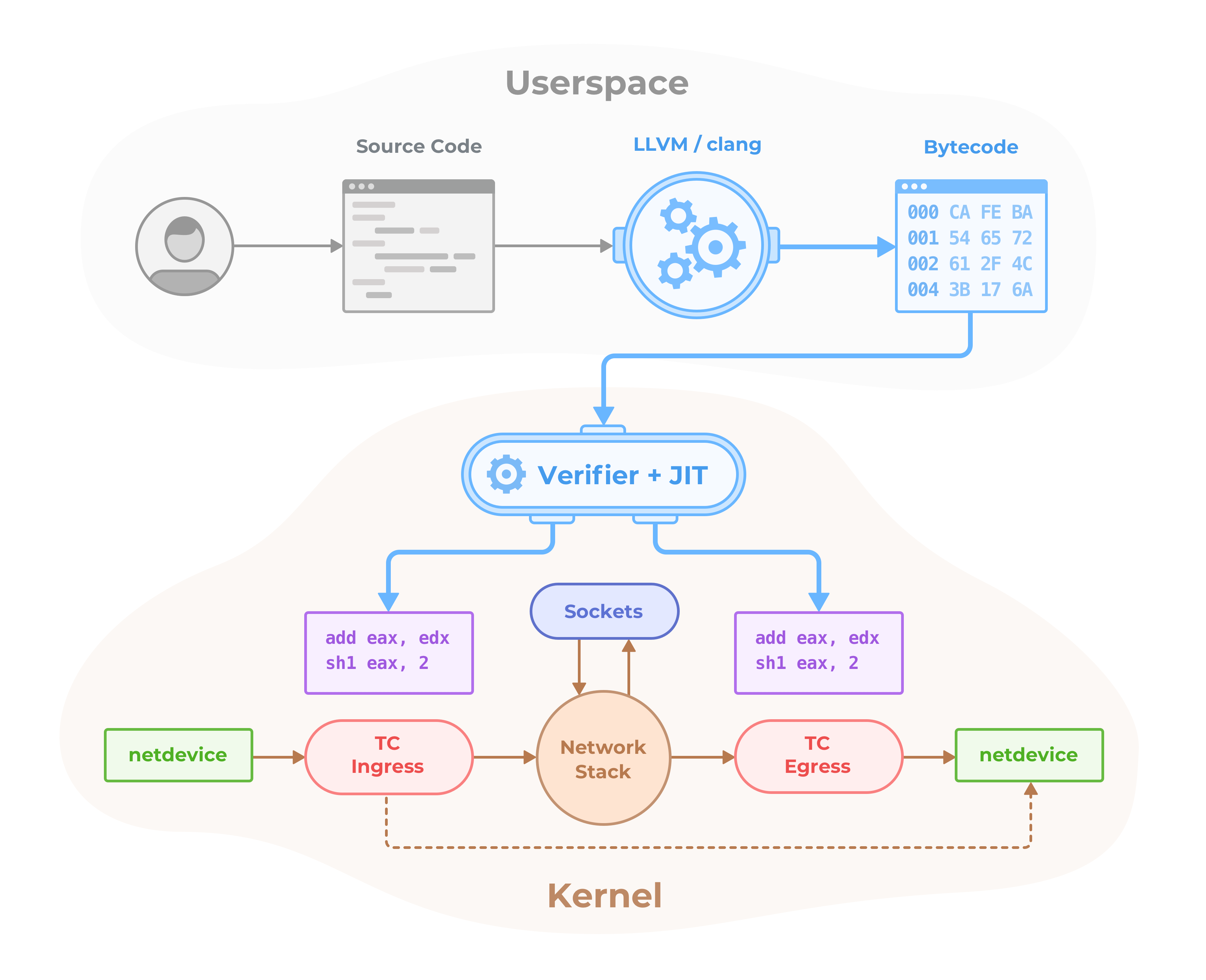
===== Test: operator-metadata-preparation-bundle-image =====
Failed to parse and prepare operator metadata:
java.lang.Exception: No valid OCP versions found for `com.redhat.openshift.versions` label: v4.5,v4.6,v4.7 organization: certified-operators
Output of the `extract-operator-bundle.yml` ansible role:
2021-06-25 12:57:33,685 p=23 u=default n=ansible | Using /etc/ansible/ansible.cfg as config file
2021-06-25 12:57:33,897 p=23 u=default n=ansible | PLAY [Extract and parse the operator bundle image for testing usage] ***********
2021-06-25 12:57:33,910 p=23 u=default n=ansible | TASK [Extract the operator bundle image into files needed to run the tests] ****
2021-06-25 12:57:33,952 p=23 u=default n=ansible | TASK [extract_operator_bundle : Ensure that the operator bundle directory is empty] ***
2021-06-25 12:57:34,451 p=23 u=default n=ansible | ok: [localhost] => {"ansible_facts": {"discovered_interpreter_python": "/usr/bin/python3"}, "changed": false, "path": "/tmp/operator-bundle", "state": "absent"}
2021-06-25 12:57:34,453 p=23 u=default n=ansible | TASK [extract_operator_bundle : Ensure that the operator testing directory exists and is empty] ***
2021-06-25 12:57:34,733 p=23 u=default n=ansible | ok: [localhost] => (item=absent) => {"ansible_loop_var": "item", "changed": false, "item": "absent", "path": "/home/jenkins/agent/test-operator", "state": "absent"}
2021-06-25 12:57:34,899 p=23 u=default n=ansible | changed: [localhost] => (item=directory) => {"ansible_loop_var": "item", "changed": true, "gid": 1001680000, "group": "1001680000", "item": "directory", "mode": "02777", "owner": "default", "path": "/home/jenkins/agent/test-operator", "size": 6, "state": "directory", "uid": 1001680000}
2021-06-25 12:57:34,901 p=23 u=default n=ansible | TASK [extract_operator_bundle : Copy the bundle image layers into a local directory using skopeo] ***
2021-06-25 12:57:37,142 p=23 u=default n=ansible | changed: [localhost] => {"changed": true, "cmd": "skopeo copy docker://registry-proxy.engineering.redhat.com/rh-osbs/iib:85288 oci:/tmp/operator-bundle:latest", "delta": "0:00:01.855013", "end": "2021-06-25 12:57:37.120945", "rc": 0, "start": "2021-06-25 12:57:35.265932", "stderr": "", "stderr_lines": [], "stdout": "Getting image source signatures\nCopying blob sha256:04096fcfd395ec19238b78033c1f187ad2dea9ad043de46af5d2fbbb5c2408ac\nCopying blob sha256:cf462a34353a199b63e5a317a3dddbdbee5d6b2915798806e86469e8549b4907\nCopying blob sha256:8383384b6e405a28ad70017140ef4e99a3a33e713b39b2291442714cda849831\nCopying blob sha256:a9fe1fbb05f00be2b6dfb5116457839ea3bdd38e6a5facd43555c0f921f93e9a\nCopying config sha256:6d1571eaff425c3fa6eda782e014347669690b1176733065d562509c44103ca9\nWriting manifest to image destination\nStoring signatures", "stdout_lines": ["Getting image source signatures", "Copying blob sha256:04096fcfd395ec19238b78033c1f187ad2dea9ad043de46af5d2fbbb5c2408ac", "Copying blob sha256:cf462a34353a199b63e5a317a3dddbdbee5d6b2915798806e86469e8549b4907", "Copying blob sha256:8383384b6e405a28ad70017140ef4e99a3a33e713b39b2291442714cda849831", "Copying blob sha256:a9fe1fbb05f00be2b6dfb5116457839ea3bdd38e6a5facd43555c0f921f93e9a", "Copying config sha256:6d1571eaff425c3fa6eda782e014347669690b1176733065d562509c44103ca9", "Writing manifest to image destination", "Storing signatures"]}
2021-06-25 12:57:37,144 p=23 u=default n=ansible | TASK [extract_operator_bundle : Inspect the copied image directory] ************
2021-06-25 12:57:37,478 p=23 u=default n=ansible | changed: [localhost] => {"changed": true, "cmd": "skopeo inspect --raw oci:///tmp/operator-bundle", "delta": "0:00:00.037190", "end": "2021-06-25 12:57:37.458496", "rc": 0, "start": "2021-06-25 12:57:37.421306", "stderr": "", "stderr_lines": [], "stdout": "{\"schemaVersion\":2,\"config\":{\"mediaType\":\"application/vnd.oci.image.config.v1+json\",\"digest\":\"sha256:6d1571eaff425c3fa6eda782e014347669690b1176733065d562509c44103ca9\",\"size\":4370},\"layers\":[{\"mediaType\":\"application/vnd.oci.image.layer.v1.tar+gzip\",\"digest\":\"sha256:04096fcfd395ec19238b78033c1f187ad2dea9ad043de46af5d2fbbb5c2408ac\",\"size\":7674},{\"mediaType\":\"application/vnd.oci.image.layer.v1.tar+gzip\",\"digest\":\"sha256:cf462a34353a199b63e5a317a3dddbdbee5d6b2915798806e86469e8549b4907\",\"size\":366},{\"mediaType\":\"application/vnd.oci.image.layer.v1.tar+gzip\",\"digest\":\"sha256:8383384b6e405a28ad70017140ef4e99a3a33e713b39b2291442714cda849831\",\"size\":433},{\"mediaType\":\"application/vnd.oci.image.layer.v1.tar+gzip\",\"digest\":\"sha256:a9fe1fbb05f00be2b6dfb5116457839ea3bdd38e6a5facd43555c0f921f93e9a\",\"size\":7039}]}", "stdout_lines": ["{\"schemaVersion\":2,\"config\":{\"mediaType\":\"application/vnd.oci.image.config.v1+json\",\"digest\":\"sha256:6d1571eaff425c3fa6eda782e014347669690b1176733065d562509c44103ca9\",\"size\":4370},\"layers\":[{\"mediaType\":\"application/vnd.oci.image.layer.v1.tar+gzip\",\"digest\":\"sha256:04096fcfd395ec19238b78033c1f187ad2dea9ad043de46af5d2fbbb5c2408ac\",\"size\":7674},{\"mediaType\":\"application/vnd.oci.image.layer.v1.tar+gzip\",\"digest\":\"sha256:cf462a34353a199b63e5a317a3dddbdbee5d6b2915798806e86469e8549b4907\",\"size\":366},{\"mediaType\":\"application/vnd.oci.image.layer.v1.tar+gzip\",\"digest\":\"sha256:8383384b6e405a28ad70017140ef4e99a3a33e713b39b2291442714cda849831\",\"size\":433},{\"mediaType\":\"application/vnd.oci.image.layer.v1.tar+gzip\",\"digest\":\"sha256:a9fe1fbb05f00be2b6dfb5116457839ea3bdd38e6a5facd43555c0f921f93e9a\",\"size\":7039}]}"]}
2021-06-25 12:57:37,481 p=23 u=default n=ansible | TASK [extract_operator_bundle : Parse the image manifest json retrieved by skopeo] ***
2021-06-25 12:57:37,608 p=23 u=default n=ansible | ok: [localhost] => {"ansible_facts": {"image_manifest": {"config": {"digest": "sha256:6d1571eaff425c3fa6eda782e014347669690b1176733065d562509c44103ca9", "mediaType": "application/vnd.oci.image.config.v1+json", "size": 4370}, "layers": [{"digest": "sha256:04096fcfd395ec19238b78033c1f187ad2dea9ad043de46af5d2fbbb5c2408ac", "mediaType": "application/vnd.oci.image.layer.v1.tar+gzip", "size": 7674}, {"digest": "sha256:cf462a34353a199b63e5a317a3dddbdbee5d6b2915798806e86469e8549b4907", "mediaType": "application/vnd.oci.image.layer.v1.tar+gzip", "size": 366}, {"digest": "sha256:8383384b6e405a28ad70017140ef4e99a3a33e713b39b2291442714cda849831", "mediaType": "application/vnd.oci.image.layer.v1.tar+gzip", "size": 433}, {"digest": "sha256:a9fe1fbb05f00be2b6dfb5116457839ea3bdd38e6a5facd43555c0f921f93e9a", "mediaType": "application/vnd.oci.image.layer.v1.tar+gzip", "size": 7039}], "schemaVersion": 2}}, "changed": false}
2021-06-25 12:57:37,610 p=23 u=default n=ansible | TASK [extract_operator_bundle : debug] *****************************************
2021-06-25 12:57:37,736 p=23 u=default n=ansible | ok: [localhost] => {
"image_manifest": {
"config": {
"digest": "sha256:6d1571eaff425c3fa6eda782e014347669690b1176733065d562509c44103ca9",
"mediaType": "application/vnd.oci.image.config.v1+json",
"size": 4370
},
"layers": [
{
"digest": "sha256:04096fcfd395ec19238b78033c1f187ad2dea9ad043de46af5d2fbbb5c2408ac",
"mediaType": "application/vnd.oci.image.layer.v1.tar+gzip",
"size": 7674
},
{
"digest": "sha256:cf462a34353a199b63e5a317a3dddbdbee5d6b2915798806e86469e8549b4907",
"mediaType": "application/vnd.oci.image.layer.v1.tar+gzip",
"size": 366
},
{
"digest": "sha256:8383384b6e405a28ad70017140ef4e99a3a33e713b39b2291442714cda849831",
"mediaType": "application/vnd.oci.image.layer.v1.tar+gzip",
"size": 433
},
{
"digest": "sha256:a9fe1fbb05f00be2b6dfb5116457839ea3bdd38e6a5facd43555c0f921f93e9a",
"mediaType": "application/vnd.oci.image.layer.v1.tar+gzip",
"size": 7039
}
],
"schemaVersion": 2
}
}
2021-06-25 12:57:37,739 p=23 u=default n=ansible | TASK [extract_operator_bundle : Unpack the image layers using the umoci tool] ***
2021-06-25 12:57:38,049 p=23 u=default n=ansible | changed: [localhost] => {"changed": true, "cmd": "/usr/local/bin/umoci unpack --rootless --image /tmp/operator-bundle:latest /tmp/operator-bundle/data", "delta": "0:00:00.017238", "end": "2021-06-25 12:57:38.030055", "rc": 0, "start": "2021-06-25 12:57:38.012817", "stderr": "", "stderr_lines": [], "stdout": "", "stdout_lines": []}
2021-06-25 12:57:38,052 p=23 u=default n=ansible | TASK [extract_operator_bundle : Copy the rootfs of the unpacked data into the operator work directory] ***
2021-06-25 12:57:38,355 p=23 u=default n=ansible | changed: [localhost] => {"changed": true, "cmd": "cp -r /tmp/operator-bundle/data/rootfs/* /home/jenkins/agent/test-operator", "delta": "0:00:00.004747", "end": "2021-06-25 12:57:38.335496", "rc": 0, "start": "2021-06-25 12:57:38.330749", "stderr": "", "stderr_lines": [], "stdout": "", "stdout_lines": []}
2021-06-25 12:57:38,357 p=23 u=default n=ansible | TASK [Parse the operator bundle image, manifest and metadata] ******************
2021-06-25 12:57:38,391 p=23 u=default n=ansible | TASK [parse_operator_bundle : Inspect the bundle image with skopeo] ************
2021-06-25 12:57:38,732 p=23 u=default n=ansible | changed: [localhost] => {"changed": true, "cmd": "skopeo inspect oci:/tmp/operator-bundle:latest", "delta": "0:00:00.039334", "end": "2021-06-25 12:57:38.710159", "rc": 0, "start": "2021-06-25 12:57:38.670825", "stderr": "", "stderr_lines": [], "stdout": "{\n \"Digest\": \"sha256:b281990102cb80fdc40f1f7c1bed3f8267671701dd94e4a4508e3ffa8b371928\",\n \"RepoTags\": [],\n \"Created\": \"2021-06-25T12:55:48.69285054Z\",\n \"DockerVersion\": \"\",\n \"Labels\": {\n \"com.redhat.delivery.backport\": \"true\",\n \"com.redhat.delivery.operator.bundle\": \"true\",\n \"com.redhat.iib.pinned\": \"true\",\n \"com.redhat.openshift.versions\": \"v4.5,v4.6,v4.7\",\n \"io.buildah.version\": \"1.16.7\",\n \"operators.operatorframework.io.bundle.channel.default.v1\": \"stable\",\n \"operators.operatorframework.io.bundle.channels.v1\": \"stable\",\n \"operators.operatorframework.io.bundle.manifests.v1\": \"manifests/\",\n \"operators.operatorframework.io.bundle.mediatype.v1\": \"registry+v1\",\n \"operators.operatorframework.io.bundle.metadata.v1\": \"metadata/\",\n \"operators.operatorframework.io.bundle.package.v1\": \"cilium\",\n \"operators.operatorframework.io.metrics.builder\": \"operator-sdk-v1.0.1\",\n \"operators.operatorframework.io.metrics.mediatype.v1\": \"metrics+v1\",\n \"operators.operatorframework.io.metrics.project_layout\": \"helm.sdk.operatorframework.io/v1\"\n },\n \"Architecture\": \"amd64\",\n \"Os\": \"linux\",\n \"Layers\": [\n \"sha256:04096fcfd395ec19238b78033c1f187ad2dea9ad043de46af5d2fbbb5c2408ac\",\n \"sha256:cf462a34353a199b63e5a317a3dddbdbee5d6b2915798806e86469e8549b4907\",\n \"sha256:8383384b6e405a28ad70017140ef4e99a3a33e713b39b2291442714cda849831\",\n \"sha256:a9fe1fbb05f00be2b6dfb5116457839ea3bdd38e6a5facd43555c0f921f93e9a\"\n ],\n \"Env\": [\n \"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin\"\n ]\n}", "stdout_lines": ["{", " \"Digest\": \"sha256:b281990102cb80fdc40f1f7c1bed3f8267671701dd94e4a4508e3ffa8b371928\",", " \"RepoTags\": [],", " \"Created\": \"2021-06-25T12:55:48.69285054Z\",", " \"DockerVersion\": \"\",", " \"Labels\": {", " \"com.redhat.delivery.backport\": \"true\",", " \"com.redhat.delivery.operator.bundle\": \"true\",", " \"com.redhat.iib.pinned\": \"true\",", " \"com.redhat.openshift.versions\": \"v4.5,v4.6,v4.7\",", " \"io.buildah.version\": \"1.16.7\",", " \"operators.operatorframework.io.bundle.channel.default.v1\": \"stable\",", " \"operators.operatorframework.io.bundle.channels.v1\": \"stable\",", " \"operators.operatorframework.io.bundle.manifests.v1\": \"manifests/\",", " \"operators.operatorframework.io.bundle.mediatype.v1\": \"registry+v1\",", " \"operators.operatorframework.io.bundle.metadata.v1\": \"metadata/\",", " \"operators.operatorframework.io.bundle.package.v1\": \"cilium\",", " \"operators.operatorframework.io.metrics.builder\": \"operator-sdk-v1.0.1\",", " \"operators.operatorframework.io.metrics.mediatype.v1\": \"metrics+v1\",", " \"operators.operatorframework.io.metrics.project_layout\": \"helm.sdk.operatorframework.io/v1\"", " },", " \"Architecture\": \"amd64\",", " \"Os\": \"linux\",", " \"Layers\": [", " \"sha256:04096fcfd395ec19238b78033c1f187ad2dea9ad043de46af5d2fbbb5c2408ac\",", " \"sha256:cf462a34353a199b63e5a317a3dddbdbee5d6b2915798806e86469e8549b4907\",", " \"sha256:8383384b6e405a28ad70017140ef4e99a3a33e713b39b2291442714cda849831\",", " \"sha256:a9fe1fbb05f00be2b6dfb5116457839ea3bdd38e6a5facd43555c0f921f93e9a\"", " ],", " \"Env\": [", " \"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin\"", " ]", "}"]}
2021-06-25 12:57:38,735 p=23 u=default n=ansible | TASK [parse_operator_bundle : Save the skopeo inspect output to a log file] ****
2021-06-25 12:57:39,460 p=23 u=default n=ansible | changed: [localhost] => {"changed": true, "checksum": "310c712a169b0533c744c10f9da0c99e51cc2544", "dest": "/home/jenkins/agent/workspace/cvp-isv-operator-bundle-image-validation-test/bundle-skopeo-inspect.json", "gid": 0, "group": "root", "md5sum": "793c083ef28e9a4e5033bd5007f5c178", "mode": "0644", "owner": "default", "size": 1652, "src": "/home/jenkins/agent/.ansible/tmp/ansible-tmp-1624625858.8761046-231-40274241097795/source", "state": "file", "uid": 1001680000}
2021-06-25 12:57:39,463 p=23 u=default n=ansible | TASK [parse_operator_bundle : Include the skopeo inspect result vars] **********
2021-06-25 12:57:39,592 p=23 u=default n=ansible | ok: [localhost] => {"ansible_facts": {"skopeo_inspect_json": {"Architecture": "amd64", "Created": "2021-06-25T12:55:48.69285054Z", "Digest": "sha256:b281990102cb80fdc40f1f7c1bed3f8267671701dd94e4a4508e3ffa8b371928", "DockerVersion": "", "Env": ["PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin"], "Labels": {"com.redhat.delivery.backport": "true", "com.redhat.delivery.operator.bundle": "true", "com.redhat.iib.pinned": "true", "com.redhat.openshift.versions": "v4.5,v4.6,v4.7", "io.buildah.version": "1.16.7", "operators.operatorframework.io.bundle.channel.default.v1": "stable", "operators.operatorframework.io.bundle.channels.v1": "stable", "operators.operatorframework.io.bundle.manifests.v1": "manifests/", "operators.operatorframework.io.bundle.mediatype.v1": "registry+v1", "operators.operatorframework.io.bundle.metadata.v1": "metadata/", "operators.operatorframework.io.bundle.package.v1": "cilium", "operators.operatorframework.io.metrics.builder": "operator-sdk-v1.0.1", "operators.operatorframework.io.metrics.mediatype.v1": "metrics+v1", "operators.operatorframework.io.metrics.project_layout": "helm.sdk.operatorframework.io/v1"}, "Layers": ["sha256:04096fcfd395ec19238b78033c1f187ad2dea9ad043de46af5d2fbbb5c2408ac", "sha256:cf462a34353a199b63e5a317a3dddbdbee5d6b2915798806e86469e8549b4907", "sha256:8383384b6e405a28ad70017140ef4e99a3a33e713b39b2291442714cda849831", "sha256:a9fe1fbb05f00be2b6dfb5116457839ea3bdd38e6a5facd43555c0f921f93e9a"], "Os": "linux", "RepoTags": []}}, "changed": false}
2021-06-25 12:57:39,595 p=23 u=default n=ansible | TASK [parse_operator_bundle : Set the failed labels to an empty string and is_bundle_image to false] ***
2021-06-25 12:57:39,604 p=23 u=default n=ansible | ok: [localhost] => {"ansible_facts": {"failed_labels": "", "is_bundle_image": false}, "changed": false}
2021-06-25 12:57:39,606 p=23 u=default n=ansible | TASK [parse_operator_bundle : If the required label is not found among the image labels, add it to the failed_labels] ***
2021-06-25 12:57:39,737 p=23 u=default n=ansible | skipping: [localhost] => (item=operators.operatorframework.io.bundle.package.v1) => {"ansible_loop_var": "item", "changed": false, "item": "operators.operatorframework.io.bundle.package.v1", "skip_reason": "Conditional result was False"}
2021-06-25 12:57:39,740 p=23 u=default n=ansible | skipping: [localhost] => (item=operators.operatorframework.io.bundle.channels.v1) => {"ansible_loop_var": "item", "changed": false, "item": "operators.operatorframework.io.bundle.channels.v1", "skip_reason": "Conditional result was False"}
2021-06-25 12:57:39,743 p=23 u=default n=ansible | skipping: [localhost] => (item=com.redhat.openshift.versions) => {"ansible_loop_var": "item", "changed": false, "item": "com.redhat.openshift.versions", "skip_reason": "Conditional result was False"}
2021-06-25 12:57:39,745 p=23 u=default n=ansible | TASK [parse_operator_bundle : Fail if any of the required operator bundle image label(s) are not found] ***
2021-06-25 12:57:39,874 p=23 u=default n=ansible | skipping: [localhost] => {"changed": false, "skip_reason": "Conditional result was False"}
2021-06-25 12:57:39,876 p=23 u=default n=ansible | TASK [parse_operator_bundle : If the image contains all of the required labels for a bundle image, set the is_bundle_image to true] ***
2021-06-25 12:57:39,886 p=23 u=default n=ansible | ok: [localhost] => {"ansible_facts": {"is_bundle_image": true}, "changed": false}
2021-06-25 12:57:39,888 p=23 u=default n=ansible | TASK [parse_operator_bundle : Set the main operator bundle info as parsed from the bundle image labels] ***
2021-06-25 12:57:40,019 p=23 u=default n=ansible | ok: [localhost] => {"ansible_facts": {"channels": ["stable"], "default_channel": "", "is_backport": "", "ocp_versions": "v4.5,v4.6,v4.7", "package_name": "cilium"}, "changed": false}
2021-06-25 12:57:40,021 p=23 u=default n=ansible | TASK [parse_operator_bundle : Set the current channel to the first value from the operators.operatorframework.io.bundle.channels.v1 label] ***
2021-06-25 12:57:40,151 p=23 u=default n=ansible | ok: [localhost] => {"ansible_facts": {"current_channel": "stable"}, "changed": false}
2021-06-25 12:57:40,153 p=23 u=default n=ansible | TASK [parse_operator_bundle : Set is_backport according to the com.redhat.delivery.backport label, if it's missing, an empty is_backport means not set.] ***
2021-06-25 12:57:40,284 p=23 u=default n=ansible | ok: [localhost] => {"ansible_facts": {"is_backport": "true"}, "changed": false}
2021-06-25 12:57:40,287 p=23 u=default n=ansible | TASK [parse_operator_bundle : Set default_channel according to the operators.operatorframework.io.bundle.channel.default.v1 label if present.] ***
2021-06-25 12:57:40,420 p=23 u=default n=ansible | ok: [localhost] => {"ansible_facts": {"default_channel": "stable"}, "changed": false}
2021-06-25 12:57:40,423 p=23 u=default n=ansible | TASK [parse_operator_bundle : Determine paths with kind ClusterServiceVersion] ***
2021-06-25 12:57:40,880 p=23 u=default n=ansible | ok: [localhost] => {"changed": false, "examined": 8, "files": [{"atime": 1624625858.333047, "ctime": 1624625858.333047, "dev": 2065, "gid": 1001680000, "gr_name": "", "inode": 1154915079, "isblk": false, "ischr": false, "isdir": false, "isfifo": false, "isgid": false, "islnk": false, "isreg": true, "issock": false, "isuid": false, "mode": "0644", "mtime": 1624625858.333047, "nlink": 1, "path": "/home/jenkins/agent/test-operator/manifests/cilium-olm.csv.yaml", "pw_name": "default", "rgrp": true, "roth": true, "rusr": true, "size": 18736, "uid": 1001680000, "wgrp": false, "woth": false, "wusr": true, "xgrp": false, "xoth": false, "xusr": false}], "matched": 1, "msg": ""}
2021-06-25 12:57:40,883 p=23 u=default n=ansible | TASK [parse_operator_bundle : Set the first location found as the CSV path since the operator bundles only support having one CSV] ***
2021-06-25 12:57:41,019 p=23 u=default n=ansible | ok: [localhost] => {"ansible_facts": {"csv_path": "/home/jenkins/agent/test-operator/manifests/cilium-olm.csv.yaml"}, "changed": false}
2021-06-25 12:57:41,022 p=23 u=default n=ansible | TASK [parse_operator_bundle : Set variables for csv_path and current_csv_dir] ***
2021-06-25 12:57:41,156 p=23 u=default n=ansible | ok: [localhost] => {"ansible_facts": {"current_csv_dir": "/home/jenkins/agent/test-operator/manifests"}, "changed": false}
2021-06-25 12:57:41,159 p=23 u=default n=ansible | TASK [parse_operator_bundle : Determine the CRD paths in the operator metadata directory] ***
2021-06-25 12:57:41,471 p=23 u=default n=ansible | ok: [localhost] => {"changed": false, "examined": 2, "files": [{"atime": 1624625860.8581235, "ctime": 1624625858.3340468, "dev": 2065, "gid": 1001680000, "gr_name": "", "inode": 1154915080, "isblk": false, "ischr": false, "isdir": false, "isfifo": false, "isgid": false, "islnk": false, "isreg": true, "issock": false, "isuid": false, "mode": "0644", "mtime": 1624625858.3340468, "nlink": 1, "path": "/home/jenkins/agent/test-operator/manifests/ciliumconfigs.crd.yaml", "pw_name": "default", "rgrp": true, "roth": true, "rusr": true, "size": 1716, "uid": 1001680000, "wgrp": false, "woth": false, "wusr": true, "xgrp": false, "xoth": false, "xusr": false}], "matched": 1, "msg": ""}
2021-06-25 12:57:41,474 p=23 u=default n=ansible | TASK [parse_operator_bundle : Set crd_paths to collect crd_paths] **************
2021-06-25 12:57:41,484 p=23 u=default n=ansible | ok: [localhost] => {"ansible_facts": {"crd_paths": []}, "changed": false}
2021-06-25 12:57:41,486 p=23 u=default n=ansible | TASK [parse_operator_bundle : Get paths from crd_paths_result] *****************
2021-06-25 12:57:41,622 p=23 u=default n=ansible | ok: [localhost] => (item={'path': '/home/jenkins/agent/test-operator/manifests/ciliumconfigs.crd.yaml', 'mode': '0644', 'isdir': False, 'ischr': False, 'isblk': False, 'isreg': True, 'isfifo': False, 'islnk': False, 'issock': False, 'uid': 1001680000, 'gid': 1001680000, 'size': 1716, 'inode': 1154915080, 'dev': 2065, 'nlink': 1, 'atime': 1624625860.8581235, 'mtime': 1624625858.3340468, 'ctime': 1624625858.3340468, 'gr_name': '', 'pw_name': 'default', 'wusr': True, 'rusr': True, 'xusr': False, 'wgrp': False, 'rgrp': True, 'xgrp': False, 'woth': False, 'roth': True, 'xoth': False, 'isuid': False, 'isgid': False}) => {"ansible_facts": {"crd_paths": ["/home/jenkins/agent/test-operator/manifests/ciliumconfigs.crd.yaml"]}, "ansible_loop_var": "item", "changed": false, "item": {"atime": 1624625860.8581235, "ctime": 1624625858.3340468, "dev": 2065, "gid": 1001680000, "gr_name": "", "inode": 1154915080, "isblk": false, "ischr": false, "isdir": false, "isfifo": false, "isgid": false, "islnk": false, "isreg": true, "issock": false, "isuid": false, "mode": "0644", "mtime": 1624625858.3340468, "nlink": 1, "path": "/home/jenkins/agent/test-operator/manifests/ciliumconfigs.crd.yaml", "pw_name": "default", "rgrp": true, "roth": true, "rusr": true, "size": 1716, "uid": 1001680000, "wgrp": false, "woth": false, "wusr": true, "xgrp": false, "xoth": false, "xusr": false}}
2021-06-25 12:57:41,625 p=23 u=default n=ansible | TASK [parse_operator_bundle : Read csv.yaml file] ******************************
2021-06-25 12:57:41,936 p=23 u=default n=ansible | changed: [localhost] => {"changed": true, "cmd": "cat /home/jenkins/agent/test-operator/manifests/cilium-olm.csv.yaml", "delta": "0:00:00.003739", "end": "2021-06-25 12:57:41.912348", "rc": 0, "start": "2021-06-25 12:57:41.908609", "stderr": "", "stderr_lines": [], "stdout": "apiVersion: operators.coreos.com/v1alpha1\nkind: ClusterServiceVersion\nmetadata:\n annotations:\n alm-examples: '[{\"apiVersion\":\"cilium.io/v1alpha1\",\"kind\":\"CiliumConfig\",\"metadata\":{\"name\":\"cilium-openshift-default\",\"namespace\":\"placeholder\"},\"spec\":{\"nativeRoutingCIDR\":\"10.128.0.0/14\",\"endpointRoutes\":{\"enabled\":true},\"kubeProxyReplacement\":\"probe\",\"cni\":{\"binPath\":\"/var/lib/cni/bin\",\"confPath\":\"/var/run/multus/cni/net.d\"},\"ipam\":{\"operator\":{\"clusterPoolIPv4PodCIDR\":\"10.128.0.0/14\",\"clusterPoolIPv4MaskSize\":\"23\"},\"mode\":\"cluster-pool\"},\"prometheus\":{\"serviceMonitor\":{\"enabled\":false}},\"hubble\":{\"tls\":{\"enabled\":false}}}}]'\n alm-examples-metadata: '{\"cilium-openshift-default\":{\"description\":\"Default CiliumConfig CR for OpenShift\"}}'\n capabilities: Basic Install\n categories: Networking,Security\n repository: http://github.com/cilium/cilium\n support: [email protected]\n name: cilium.v1.10.1-xdcd9835\n namespace: placeholder\nspec:\n apiservicedefinitions: {}\n customresourcedefinitions:\n owned:\n - kind: CiliumConfig\n name: ciliumconfigs.cilium.io\n resources:\n - kind: DaemonSet\n name: cilium\n version: v1\n - kind: Deployment\n name: cilium-operator\n version: v1\n - kind: ConfigMap\n name: cilium-config\n version: v1\n statusDescriptors:\n - description: Helm release conditions\n displayName: Conditions\n path: conditions\n - description: Name of deployed Helm release\n displayName: Deployed release\n path: deployedRelease\n version: v1alpha1\n description: Cilium - eBPF-based Networking, Security, and Observability\n displayName: Cilium\n icon:\n - base64data: PHN2ZyB3aWR0aD0iMTE5IiBoZWlnaHQ9IjM1IiB2aWV3Qm94PSIwIDAgMTE5IDM1IiBmaWxsPSJub25lIiB4bWxucz0iaHR0cDovL3d3dy53My5vcmcvMjAwMC9zdmciPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTI5LjMzNjEgMTguODA3NUgyNC4yMzY4TDIxLjY1NzEgMjMuMzI2MkwyNC4yMzY4IDI3Ljc4MzhIMjkuMzM2MUwzMS45MTU3IDIzLjMyNjJMMjkuMzM2MSAxOC44MDc1WiIgZmlsbD0iIzgwNjFBOSIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTI5LjMzNjEgNi44MzkwNUgyNC4yMzY4TDIxLjY1NzEgMTEuMzU3N0wyNC4yMzY4IDE1LjgxNTNIMjkuMzM2MUwzMS45MTU3IDExLjM1NzdMMjkuMzM2MSA2LjgzOTA1WiIgZmlsbD0iI0YxNzMyMyIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTE5LjA3NzQgMS4xMzk4M0gxMy45NzgxTDExLjM5ODQgNS42NTg1MkwxMy45NzgxIDEwLjExNjFIMTkuMDc3NEwyMS42NTcxIDUuNjU4NTJMMTkuMDc3NCAxLjEzOTgzWiIgZmlsbD0iI0Y4QzUxNyIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTguODE4ODkgNi44MzkwNUgzLjcxOTU5TDEuMTM5ODkgMTEuMzU3N0wzLjcxOTU5IDE1LjgxNTNIOC44MTg4OUwxMS4zOTg1IDExLjM1NzdMOC44MTg4OSA2LjgzOTA1WiIgZmlsbD0iI0NBREQ3MiIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTE5LjA3NzQgMTIuNTM4M0gxMy45NzgxTDExLjM5ODQgMTcuMDU3TDEzLjk3ODEgMjEuNTE0NkgxOS4wNzc0TDIxLjY1NzEgMTcuMDU3TDE5LjA3NzQgMTIuNTM4M1oiIGZpbGw9IiNFODI2MjkiLz4KPHBhdGggZmlsbC1ydWxlPSJldmVub2RkIiBjbGlwLXJ1bGU9ImV2ZW5vZGQiIGQ9Ik04LjgxODg5IDE4LjgwNzVIMy43MTk1OUwxLjEzOTg5IDIzLjMyNjJMMy43MTk1OSAyNy43ODM4SDguODE4ODlMMTEuMzk4NSAyMy4zMjYyTDguODE4ODkgMTguODA3NVoiIGZpbGw9IiM5OEM5M0UiLz4KPHBhdGggZmlsbC1ydWxlPSJldmVub2RkIiBjbGlwLXJ1bGU9ImV2ZW5vZGQiIGQ9Ik0xOS4wNzc0IDI0LjUwNjdIMTMuOTc4MUwxMS4zOTg0IDI5LjAyNTRMMTMuOTc4MSAzMy40ODNIMTkuMDc3NEwyMS42NTcxIDI5LjAyNTRMMTkuMDc3NCAyNC41MDY3WiIgZmlsbD0iIzYyOEFDNiIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTE4LjgxODEgMjAuNzc4M0gxNC4yMzc3TDExLjkyMDUgMTYuODM5N0wxNC4yMzc3IDEyLjg0NzFIMTguODE4MUwyMS4xMzUyIDE2LjgzOTdMMTguODE4MSAyMC43NzgzWk0xOS42NDQxIDExLjM5ODRIMTMuMzkzM0wxMC4yNTg3IDE2LjgzMUwxMy4zOTMzIDIyLjIyN0gxOS42NDQxTDIyLjc5NyAxNi44MzFMMTkuNjQ0MSAxMS4zOTg0WiIgZmlsbD0iIzM2MzczNiIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTEzLjM5MzIgMjMuMzY2OUwxMC4yNTg3IDI4Ljc5OTVMMTMuMzkzMiAzNC4xOTU0SDE5LjY0NDFMMjIuNzk3IDI4Ljc5OTVMMTkuNjQ0MSAyMy4zNjY5SDEzLjM5MzJaTTExLjkyMDQgMjguODA4MkwxNC4yMzc2IDI0LjgxNTZIMTguODE4TDIxLjEzNTIgMjguODA4MkwxOC44MTggMzIuNzQ2OEgxNC4yMzc2TDExLjkyMDQgMjguODA4MloiIGZpbGw9IiMzNjM3MzYiLz4KPHBhdGggZmlsbC1ydWxlPSJldmVub2RkIiBjbGlwLXJ1bGU9ImV2ZW5vZGQiIGQ9Ik0xMy4zOTMyIDBMMTAuMjU4NyA1LjQzMjYzTDEzLjM5MzIgMTAuODI4NUgxOS42NDQxTDIyLjc5NyA1LjQzMjYzTDE5LjY0NDEgMEgxMy4zOTMyWk0xMS45MjA0IDUuNDQxMkwxNC4yMzc2IDEuNDQ4N0gxOC44MThMMjEuMTM1MiA1LjQ0MTJMMTguODE4IDkuMzc5ODVIMTQuMjM3NkwxMS45MjA0IDUuNDQxMloiIGZpbGw9IiMzNjM3MzYiLz4KPHBhdGggZmlsbC1ydWxlPSJldmVub2RkIiBjbGlwLXJ1bGU9ImV2ZW5vZGQiIGQ9Ik0yMy42NTE4IDE3LjY2NzZMMjAuNTE3MiAyMy4xMDAyTDIzLjY1MTggMjguNDk2MUgyOS45MDI2TDMzLjA1NTUgMjMuMTAwMkwyOS45MDI2IDE3LjY2NzZIMjMuNjUxOFpNMjIuMTc5MSAyMy4xMDg4TDI0LjQ5NjIgMTkuMTE2MkgyOS4wNzY2TDMxLjM5MzcgMjMuMTA4OEwyOS4wNzY2IDI3LjA0NzVIMjQuNDk2MkwyMi4xNzkxIDIzLjEwODhaIiBmaWxsPSIjMzYzNzM2Ii8+CjxwYXRoIGZpbGwtcnVsZT0iZXZlbm9kZCIgY2xpcC1ydWxlPSJldmVub2RkIiBkPSJNMjMuNjUxOCA1LjY5OTIyTDIwLjUxNzIgMTEuMTMxOUwyMy42NTE4IDE2LjUyNzhIMjkuOTAyNkwzMy4wNTU1IDExLjEzMTlMMjkuOTAyNiA1LjY5OTIySDIzLjY1MThaTTIyLjE3OTEgMTEuMTQwNUwyNC40OTYyIDcuMTQ3OTFIMjkuMDc2NkwzMS4zOTM3IDExLjE0MDVMMjkuMDc2NiAxNS4wNzkxSDI0LjQ5NjJMMjIuMTc5MSAxMS4xNDA1WiIgZmlsbD0iIzM2MzczNiIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTMuMTM0NTMgMTcuNjY3NkwwIDIzLjEwMDJMMy4xMzQ1MyAyOC40OTYxSDkuMzg1NDJMMTIuNTM4MyAyMy4xMDAyTDkuMzg1NDIgMTcuNjY3NkgzLjEzNDUzWk0xLjY2MTc5IDIzLjEwODhMMy45Nzg5MiAxOS4xMTYySDguNTU5MzNMMTAuODc2NSAyMy4xMDg4TDguNTU5MzMgMjcuMDQ3NUgzLjk3ODkyTDEuNjYxNzkgMjMuMTA4OFoiIGZpbGw9IiMzNjM3MzYiLz4KPHBhdGggZmlsbC1ydWxlPSJldmVub2RkIiBjbGlwLXJ1bGU9ImV2ZW5vZGQiIGQ9Ik0zLjEzNDUzIDUuNjk5MjJMMCAxMS4xMzE5TDMuMTM0NTMgMTYuNTI3OEg5LjM4NTQyTDEyLjUzODMgMTEuMTMxOUw5LjM4NTQyIDUuNjk5MjJIMy4xMzQ1M1pNMS42NjE3OSAxMS4xNDA1TDMuOTc4OTIgNy4xNDc5MUg4LjU1OTMzTDEwLjg3NjUgMTEuMTQwNUw4LjU1OTMzIDE1LjA3OTFIMy45Nzg5MkwxLjY2MTc5IDExLjE0MDVaIiBmaWxsPSIjMzYzNzM2Ii8+CjxwYXRoIGZpbGwtcnVsZT0iZXZlbm9kZCIgY2xpcC1ydWxlPSJldmVub2RkIiBkPSJNMTE4LjA0NSAyNi4yMjEySDExNS42ODRDMTE1LjY4IDI2LjE1MTEgMTE1LjY3MiAyNi4wNzkgMTE1LjY3MiAyNi4wMDY3QzExNS42NzEgMjUuNDc1NSAxMTUuNjcyIDI0Ljk0NDMgMTE1LjY3MiAyNC40MTMyQzExNS42NzIgMjEuODE5NiAxMTUuNjcgMTkuMjI1OSAxMTUuNjczIDE2LjYzMjNDMTE1LjY3NCAxNi4wMDA0IDExNS42MDkgMTUuMzc5NyAxMTUuNDEyIDE0Ljc3NjlDMTE1LjA1NCAxMy42NzY5IDExNC4yODUgMTMuMDc1OCAxMTMuMTQ4IDEyLjk0MjNDMTExLjkwMiAxMi43OTYgMTEwLjc4NiAxMy4xMTU1IDEwOS44MDcgMTMuOTA4NUMxMDkuMjQ2IDE0LjM2MzQgMTA4Ljc2IDE0Ljg4ODQgMTA4LjMzNiAxNS40NzA2QzEwOC4yOTEgMTUuNTMyMyAxMDguMjc1IDE1LjYxOTMgMTA4LjI2IDE1LjY5NzJDMTA4LjI0OCAxNS43NTY5IDEwOC4yNTcgMTUuODIwOSAxMDguMjU3IDE1Ljg4MzFDMTA4LjI1NyAxOS4yMjE3IDEwOC4yNTcgMjIuNTYwMyAxMDguMjU3IDI1Ljg5OVYyNi4xNzQ1SDEwNS44MTNDMTA1LjgxIDI2LjA5NjkgMTA1LjgwNCAyNi4wMTc4IDEwNS44MDQgMjUuOTM4NUMxMDUuODAzIDI0LjY0MTYgMTA1LjgwMyAyMy4zNDQ5IDEwNS44MDMgMjIuMDQ4QzEwNS44MDMgMjAuMjEzMSAxMDUuODA0IDE4LjM3ODMgMTA1LjgwMyAxNi41NDM0QzEwNS44MDIgMTUuOTE4OCAxMDUuNzIxIDE1LjMwNDkgMTA1LjUxNiAxNC43MTI3QzEwNS4xNSAxMy42NTI0IDEwNC4zODkgMTMuMDc2IDEwMy4yODkgMTIuOTQzOEMxMDEuOTk1IDEyLjc4ODQgMTAwLjg0NyAxMy4xMzU4IDk5Ljg0ODUgMTMuOTc3N0M5OS4zNTQ4IDE0LjM5NCA5OC45MjcxIDE0Ljg2OCA5OC41NTEzIDE1LjM5MTlDOTguNDY2NyAxNS41MDk3IDk4LjQzIDE1LjYyNzMgOTguNDMwMiAxNS43NzMzQzk4LjQzMzkgMTguMTg3NiA5OC40MzI5IDIwLjYwMTkgOTguNDMyOSAyMy4wMTYyQzk4LjQzMjkgMjQuMDAyNyA5OC40MzI4IDI0Ljk4OTEgOTguNDMyOCAyNS45NzU1Qzk4LjQzMjggMjYuMDUwNiA5OC40MzI5IDI2LjEyNTcgOTguNDMyOSAyNi4xOTY2Qzk4LjI2OCAyNi4yNDExIDk2LjQyMDkgMjYuMjU2OCA5Ni4wMDgzIDI2LjIyMTFDOTUuOTYzNSAyNi4wNzg1IDk1Ljk0NzUgMTEuNTE3OSA5NS45OTE5IDExLjIzMjhDOTYuMTM5MiAxMS4xODk4IDk3LjYyOTkgMTEuMTc5OSA5Ny44NzkxIDExLjIyNEM5OC4wMzE5IDExLjkwNDggOTguMTg2MyAxMi41OTM0IDk4LjM1MDYgMTMuMzI1NUM5OC40MzIxIDEzLjIzNzUgOTguNDgzIDEzLjE4NDggOTguNTMxNSAxMy4xMjk4Qzk4Ljg3MzMgMTIuNzQxOCA5OS4yMTEzIDEyLjM1MyA5OS42MjA3IDEyLjAyODZDMTAwLjI5NyAxMS40OTI1IDEwMS4wMzcgMTEuMTA1IDEwMS44OTIgMTAuOTQ2NUMxMDIuODkxIDEwLjc2MTQgMTAzLjg4MSAxMC43NjkzIDEwNC44NTggMTEuMDY3N0MxMDUuNzQyIDExLjMzNzQgMTA2LjQyOCAxMS44ODM4IDEwNi45ODkgMTIuNjAxNkMxMDcuMjM2IDEyLjkxNzkgMTA3LjQ0MSAxMy4yNjA3IDEwNy42MTggMTMuNjIwOUMxMDcuNjQ3IDEzLjY4MTEgMTA3LjY4IDEzLjc0IDEwNy43MjYgMTMuODI4M0MxMDcuNzg5IDEzLjc0NzEgMTA3LjgzNSAxMy42OTA0IDEwNy44NzggMTMuNjMxOEMxMDguMzYyIDEyLjk3ODggMTA4LjkyNCAxMi40MDQ3IDEwOS41NzggMTEuOTIwOUMxMTAuNjUzIDExLjEyNjkgMTExLjg2NSAxMC43OTIxIDExMy4xODkgMTAuODMwNUMxMTMuNzY1IDEwLjg0NzIgMTE0LjMzMiAxMC45NDA1IDExNC44NzggMTEuMTA5QzExNS45NCAxMS40MzYxIDExNi43ODEgMTIuMDQ4NyAxMTcuMzE5IDEzLjA1MTZDMTE3LjczMiAxMy44MTk4IDExNy45NjEgMTQuNjMyNyAxMTguMDEzIDE1LjQ5NzZDMTE4LjAzNSAxNS44NzU5IDExOC4wNDMgMTYuMjU1NiAxMTguMDQ0IDE2LjYzNDdDMTE4LjA0NiAxOS43Mzg5IDExOC4wNDUgMjIuODQzIDExOC4wNDUgMjUuOTQ3QzExOC4wNDUgMjYuMDM1IDExOC4wNDUgMjYuMTIyOSAxMTguMDQ1IDI2LjIyMTJaIiBmaWxsPSJibGFjayIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTg4Ljk5MSAxMS4yMDg5SDkxLjQyOThDOTEuNDM0NiAxMS4yNzM0IDkxLjQ0MjggMTEuMzMzIDkxLjQ0MjggMTEuMzkyN0M5MS40NDMyIDE0LjQ0ODYgOTEuNDQ2MiAxNy41MDQ2IDkxLjQ0IDIwLjU2MDRDOTEuNDM4NiAyMS4yNDM5IDkxLjM5NzMgMjEuOTMwNCA5MS4yMDUgMjIuNTg5MUM5MC42NzQgMjQuNDA3NyA4OS41MTAzIDI1LjYzMTMgODcuNzA0NSAyNi4yMzA4Qzg3LjE5MDQgMjYuNDAxNSA4Ni42NTYzIDI2LjQ2ODYgODYuMTIxIDI2LjUxODVDODUuMTgxMSAyNi42MDYyIDg0LjI0MjcgMjYuNTcyMSA4My4zMjM4IDI2LjM1MzlDODIuMzAwNiAyNi4xMTEgODEuMzY5MSAyNS42Njg1IDgwLjYzOTcgMjQuODg3MkM3OS45NzMxIDI0LjE3MzMgNzkuNTI5NyAyMy4zMzQ4IDc5LjMxMzEgMjIuMzc0OUM3OS4xNzcgMjEuNzcxOCA3OS4xMTgzIDIxLjE2MTcgNzkuMTE2NiAyMC41NDg2Qzc5LjEwODIgMTcuNDkyNyA3OS4xMTIyIDE0LjQzNjggNzkuMTEyMSAxMS4zODA5Qzc5LjExMjEgMTEuMzMzMyA3OS4xMTYyIDExLjI4NTkgNzkuMTE4MiAxMS4yNDE0Qzc5LjI2NjUgMTEuMTg5MSA4MS4zMDYgMTEuMTc1MiA4MS41NzY0IDExLjIyNzRWMTEuNDg0NkM4MS41NzY0IDE0LjQxNjMgODEuNTc2OSAxNy4zNDggODEuNTc1OSAyMC4yNzk4QzgxLjU3NTggMjAuNzk3OSA4MS41OTYzIDIxLjMxMzIgODEuNzA0MSAyMS44MjI4QzgyLjAxOTUgMjMuMzEzOCA4My4wNDcgMjQuMjY3OSA4NC41NTkzIDI0LjQ2NjRDODUuMTY1OSAyNC41NDU5IDg1Ljc3MjggMjQuNTQxNyA4Ni4zNjk1IDI0LjQwNDFDODcuNDU3MiAyNC4xNTMgODguMTk3OCAyMy40Nzk4IDg4LjYzNDMgMjIuNDY2MkM4OC45MjMyIDIxLjc5NSA4OC45ODc1IDIxLjA3OTggODguOTg5MiAyMC4zNTlDODguOTkzNyAxOC40NDEzIDg4Ljk5MDkgMTYuNTIzNiA4OC45OTEgMTQuNjA1OUM4OC45OTEgMTMuNTY0MyA4OC45OTEgMTIuNTIyNiA4OC45OTEgMTEuNDgxVjExLjIwODlaIiBmaWxsPSJibGFjayIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTUyLjg4NDggMTMuNjc4N0M1Mi4yOTk4IDEzLjUwNDMgNTEuNzU1MiAxMy4zMzA2IDUxLjIwNCAxMy4xODA5QzUwLjU2MzYgMTMuMDA2OSA0OS45MTA0IDEyLjkwMjkgNDkuMjQzOSAxMi45MDk0QzQ4LjYxMTkgMTIuOTE1NSA0Ny45OTMyIDEzLjAxNDMgNDcuMzk2NCAxMy4yMjA0QzQ2LjU4NTMgMTMuNTAwNCA0NS45MjE3IDEzLjk4OSA0NS40MTQxIDE0LjY4MjhDNDQuNzgwMSAxNS41NDkzIDQ0LjQyMzMgMTYuNTE5MiA0NC4zMjYxIDE3LjU4ODZDNDQuMjY5OCAxOC4yMDgxIDQ0LjI0NTUgMTguODI3MiA0NC4yOSAxOS40NDc4QzQ0LjM2NTEgMjAuNDk4MiA0NC42NTc3IDIxLjQ3NyA0NS4yNDc2IDIyLjM1OTZDNDUuOTM1OSAyMy4zODk0IDQ2LjkwNDQgMjMuOTk0NSA0OC4xMDE3IDI0LjI0OTZDNDguODk5MyAyNC40MTk2IDQ5LjcwNDMgMjQuNDA0OSA1MC41MTAyIDI0LjMxMjdDNTEuMzAyNyAyNC4yMjE5IDUyLjA2MDQgMjMuOTk1NCA1Mi44MDgxIDIzLjcyODhDNTIuODg0OCAyMy43MDE0IDUyLjk2MjkgMjMuNjc4IDUzLjA1NTcgMjMuNjQ3N1YyNS42ODgzQzUyLjg0NzYgMjUuNzg0MSA1Mi42MzYzIDI1LjkwMTYgNTIuNDExNSAyNS45ODE0QzUxLjI5NjIgMjYuMzc3MSA1MC4xMzk5IDI2LjU1NjEgNDguOTYxMSAyNi41NTMyQzQ3LjczMzQgMjYuNTUwMiA0Ni41NTY1IDI2LjI5ODQgNDUuNDQzMyAyNS43NTU5QzQzLjg3MzYgMjQuOTkxMSA0Mi44MjIgMjMuNzc0MyA0Mi4yMjU4IDIyLjE0NzhDNDEuODY5IDIxLjE3NDQgNDEuNzAyNiAyMC4xNjY2IDQxLjY3MiAxOS4xMzE1QzQxLjYzNjIgMTcuOTIxIDQxLjc3NzEgMTYuNzM1OSA0Mi4xNTUxIDE1LjU4NDRDNDIuODgwMSAxMy4zNzYzIDQ0LjM1NDkgMTEuOTA0OSA0Ni41NDI5IDExLjEzNDlDNDcuMDE1NiAxMC45Njg1IDQ3LjUwMTIgMTAuODkxIDQ3Ljk5NzEgMTAuODQ2M0M0OC41NzQ3IDEwLjc5NDMgNDkuMTUxNiAxMC43NTI4IDQ5LjczMTUgMTAuODAwOEM1MC43NjIzIDEwLjg4NjEgNTEuNzY0NSAxMS4wNzg1IDUyLjY5NjIgMTEuNTU2NkM1Mi44Mzg4IDExLjYyOTcgNTIuODkyNyAxMS43MTEyIDUyLjg4OTIgMTEuODczOEM1Mi44Nzc2IDEyLjQwNDYgNTIuODg0OCAxMi45MzU4IDUyLjg4NDggMTMuNDY2OVYxMy42Nzg3WiIgZmlsbD0iYmxhY2siLz4KPHBhdGggZmlsbC1ydWxlPSJldmVub2RkIiBjbGlwLXJ1bGU9ImV2ZW5vZGQiIGQ9Ik02NC40NTg5IDI2LjE3MjdINjYuODg1MlYzLjMzMzMxSDY0LjQ1ODlWMjYuMTcyN1oiIGZpbGw9ImJsYWNrIi8+CjxwYXRoIGZpbGwtcnVsZT0iZXZlbm9kZCIgY2xpcC1ydWxlPSJldmVub2RkIiBkPSJNNTkuMzg3MiAyNi4xNzU0SDU2Ljk5MDZDNTYuOTc5NiAyNi4xNjczIDU2Ljk3MzEgMjYuMTY0MSA1Ni45Njg4IDI2LjE1OUM1Ni45NjQ1IDI2LjE1NDEgNTYuOTYwNyAyNi4xNDc1IDU2Ljk1OTcgMjYuMTQxMkM1Ni45NTQ2IDI2LjEwNzMgNTYuOTQ2NSAyNi4wNzM0IDU2Ljk0NjUgMjYuMDM5NUM1Ni45NDY4IDIxLjEyMjQgNTYuOTQ3NyAxNi4yMDUyIDU2Ljk0OTEgMTEuMjg4MUM1Ni45NDkyIDExLjI2ODYgNTYuOTU4OSAxMS4yNDkzIDU2Ljk2MzYgMTEuMjMxNEM1Ny4xMTk3IDExLjE5MDEgNTkuMTQ0MSAxMS4xODA5IDU5LjM4NzIgMTEuMjIyMVYyNi4xNzU0WiIgZmlsbD0iYmxhY2siLz4KPHBhdGggZmlsbC1ydWxlPSJldmVub2RkIiBjbGlwLXJ1bGU9ImV2ZW5vZGQiIGQ9Ik03MS45NTU4IDExLjIwOTRINzQuMzU5N0M3NC40MDQ2IDExLjM1ODMgNzQuNDE5MSAyNS44OTY2IDc0LjM3MzggMjYuMTcyOEg3MS45NTU4VjExLjIwOTRaIiBmaWxsPSJibGFjayIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTU5LjMzMzYgNy42ODU5N0g1Ni45Mjg5QzU2Ljg4NjQgNy41MzEyNiA1Ni44NzcxIDUuMjE1NjcgNTYuOTE4OCA0Ljk3MTM3SDU5LjMyNEM1OS4zNjM3IDUuMTIwMDYgNTkuMzczOSA3LjQxMDg3IDU5LjMzMzYgNy42ODU5N1oiIGZpbGw9ImJsYWNrIi8+CjxwYXRoIGZpbGwtcnVsZT0iZXZlbm9kZCIgY2xpcC1ydWxlPSJldmVub2RkIiBkPSJNNzEuOTEyOCA0Ljk2Mjc3SDc0LjMxMDRDNzQuMzU4OSA1LjEwODY1IDc0LjM3NzggNy4yNjk5MyA3NC4zMzM5IDcuNjc3NDZINzEuOTEyOFY0Ljk2Mjc3WiIgZmlsbD0iYmxhY2siLz4KPC9zdmc+\n mediatype: image/svg+xml\n install:\n spec:\n clusterPermissions:\n - rules:\n - apiGroups:\n - security.openshift.io\n resourceNames:\n - hostnetwork\n resources:\n - securitycontextconstraints\n verbs:\n - use\n - apiGroups:\n - rbac.authorization.k8s.io\n resources:\n - clusterroles\n - clusterrolebindings\n verbs:\n - create\n - get\n - patch\n - update\n - delete\n - list\n - watch\n - apiGroups:\n - cilium.io\n resources:\n - '*'\n verbs:\n - '*'\n - apiGroups:\n - apiextensions.k8s.io\n resources:\n - customresourcedefinitions\n verbs:\n - '*'\n - apiGroups:\n - coordination.k8s.io\n resources:\n - leases\n verbs:\n - create\n - get\n - update\n - apiGroups:\n - \"\"\n resources:\n - services/status\n verbs:\n - update\n - apiGroups:\n - \"\"\n resources:\n - pods\n - pods/status\n - pods/finalizers\n verbs:\n - get\n - list\n - watch\n - update\n - delete\n - apiGroups:\n - \"\"\n resources:\n - nodes\n - nodes/status\n verbs:\n - get\n - list\n - watch\n - update\n - patch\n - apiGroups:\n - \"\"\n resources:\n - namespaces\n - services\n - endpoints\n - componentstatuses\n verbs:\n - get\n - list\n - watch\n - apiGroups:\n - discovery.k8s.io\n resources:\n - endpointslices\n verbs:\n - get\n - list\n - watch\n - apiGroups:\n - networking.k8s.io\n resources:\n - networkpolicies\n verbs:\n - get\n - list\n - watch\n serviceAccountName: cilium-olm\n deployments:\n - name: cilium-olm\n spec:\n replicas: 1\n selector:\n matchLabels:\n name: cilium-olm\n template:\n metadata:\n labels:\n name: cilium-olm\n spec:\n containers:\n - command:\n - /usr/local/bin/helm-operator\n - run\n - --watches-file=watches.yaml\n - --enable-leader-election\n - --leader-election-id=cilium-olm\n - --zap-devel\n env:\n - name: WATCH_NAMESPACE\n valueFrom:\n fieldRef:\n fieldPath: metadata.namespace\n image: registry.connect.redhat.com/isovalent/cilium-olm@sha256:26f1ed31c8f0600fcea498116e7dbea157a8704989f762e22e8038b8ea364dce\n name: operator\n ports:\n - containerPort: 9443\n name: https\n protocol: TCP\n resources:\n limits:\n cpu: 100m\n memory: 150Mi\n requests:\n cpu: 100m\n memory: 150Mi\n volumeMounts:\n - mountPath: /tmp\n name: tmp\n hostNetwork: true\n serviceAccount: cilium-olm\n terminationGracePeriodSeconds: 10\n tolerations:\n - operator: Exists\n volumes:\n - emptyDir: {}\n name: tmp\n permissions:\n - rules:\n - apiGroups:\n - \"\"\n resources:\n - configmaps\n verbs:\n - get\n - list\n - watch\n - create\n - update\n - patch\n - delete\n - apiGroups:\n - \"\"\n resources:\n - events\n verbs:\n - create\n - apiGroups:\n - \"\"\n resources:\n - namespaces\n verbs:\n - get\n - apiGroups:\n - cilium.io\n resources:\n - ciliumconfigs\n - ciliumconfigs/status\n verbs:\n - list\n - apiGroups:\n - cilium.io\n resources:\n - ciliumconfigs\n - ciliumconfigs/status\n - ciliumconfigs/finalizers\n verbs:\n - get\n - patch\n - update\n - watch\n - list\n - delete\n - apiGroups:\n - \"\"\n resources:\n - events\n verbs:\n - create\n - apiGroups:\n - \"\"\n resources:\n - secrets\n verbs:\n - '*'\n - apiGroups:\n - \"\"\n resources:\n - serviceaccounts\n - configmaps\n - secrets\n - services\n verbs:\n - '*'\n - apiGroups:\n - apps\n resources:\n - deployments\n - daemonsets\n verbs:\n - '*'\n serviceAccountName: cilium-olm\n strategy: deployment\n installModes:\n - supported: true\n type: OwnNamespace\n - supported: true\n type: SingleNamespace\n - supported: false\n type: MultiNamespace\n - supported: false\n type: AllNamespaces\n keywords:\n - networking\n - security\n - observability\n - eBPF\n links:\n - name: Cilium Homepage\n url: https://cilium.io/\n maintainers:\n - email: [email protected]\n name: Cilium\n maturity: stable\n provider:\n name: Isovalent\n version: 1.10.1+xdcd9835\n relatedImages:\n - name: operator\n image: registry.connect.redhat.com/isovalent/cilium-olm@sha256:26f1ed31c8f0600fcea498116e7dbea157a8704989f762e22e8038b8ea364dce", "stdout_lines": ["apiVersion: operators.coreos.com/v1alpha1", "kind: ClusterServiceVersion", "metadata:", " annotations:", " alm-examples: '[{\"apiVersion\":\"cilium.io/v1alpha1\",\"kind\":\"CiliumConfig\",\"metadata\":{\"name\":\"cilium-openshift-default\",\"namespace\":\"placeholder\"},\"spec\":{\"nativeRoutingCIDR\":\"10.128.0.0/14\",\"endpointRoutes\":{\"enabled\":true},\"kubeProxyReplacement\":\"probe\",\"cni\":{\"binPath\":\"/var/lib/cni/bin\",\"confPath\":\"/var/run/multus/cni/net.d\"},\"ipam\":{\"operator\":{\"clusterPoolIPv4PodCIDR\":\"10.128.0.0/14\",\"clusterPoolIPv4MaskSize\":\"23\"},\"mode\":\"cluster-pool\"},\"prometheus\":{\"serviceMonitor\":{\"enabled\":false}},\"hubble\":{\"tls\":{\"enabled\":false}}}}]'", " alm-examples-metadata: '{\"cilium-openshift-default\":{\"description\":\"Default CiliumConfig CR for OpenShift\"}}'", " capabilities: Basic Install", " categories: Networking,Security", " repository: http://github.com/cilium/cilium", " support: [email protected]", " name: cilium.v1.10.1-xdcd9835", " namespace: placeholder", "spec:", " apiservicedefinitions: {}", " customresourcedefinitions:", " owned:", " - kind: CiliumConfig", " name: ciliumconfigs.cilium.io", " resources:", " - kind: DaemonSet", " name: cilium", " version: v1", " - kind: Deployment", " name: cilium-operator", " version: v1", " - kind: ConfigMap", " name: cilium-config", " version: v1", " statusDescriptors:", " - description: Helm release conditions", " displayName: Conditions", " path: conditions", " - description: Name of deployed Helm release", " displayName: Deployed release", " path: deployedRelease", " version: v1alpha1", " description: Cilium - eBPF-based Networking, Security, and Observability", " displayName: Cilium", " icon:", " - base64data: PHN2ZyB3aWR0aD0iMTE5IiBoZWlnaHQ9IjM1IiB2aWV3Qm94PSIwIDAgMTE5IDM1IiBmaWxsPSJub25lIiB4bWxucz0iaHR0cDovL3d3dy53My5vcmcvMjAwMC9zdmciPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTI5LjMzNjEgMTguODA3NUgyNC4yMzY4TDIxLjY1NzEgMjMuMzI2MkwyNC4yMzY4IDI3Ljc4MzhIMjkuMzM2MUwzMS45MTU3IDIzLjMyNjJMMjkuMzM2MSAxOC44MDc1WiIgZmlsbD0iIzgwNjFBOSIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTI5LjMzNjEgNi44MzkwNUgyNC4yMzY4TDIxLjY1NzEgMTEuMzU3N0wyNC4yMzY4IDE1LjgxNTNIMjkuMzM2MUwzMS45MTU3IDExLjM1NzdMMjkuMzM2MSA2LjgzOTA1WiIgZmlsbD0iI0YxNzMyMyIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTE5LjA3NzQgMS4xMzk4M0gxMy45NzgxTDExLjM5ODQgNS42NTg1MkwxMy45NzgxIDEwLjExNjFIMTkuMDc3NEwyMS42NTcxIDUuNjU4NTJMMTkuMDc3NCAxLjEzOTgzWiIgZmlsbD0iI0Y4QzUxNyIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTguODE4ODkgNi44MzkwNUgzLjcxOTU5TDEuMTM5ODkgMTEuMzU3N0wzLjcxOTU5IDE1LjgxNTNIOC44MTg4OUwxMS4zOTg1IDExLjM1NzdMOC44MTg4OSA2LjgzOTA1WiIgZmlsbD0iI0NBREQ3MiIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTE5LjA3NzQgMTIuNTM4M0gxMy45NzgxTDExLjM5ODQgMTcuMDU3TDEzLjk3ODEgMjEuNTE0NkgxOS4wNzc0TDIxLjY1NzEgMTcuMDU3TDE5LjA3NzQgMTIuNTM4M1oiIGZpbGw9IiNFODI2MjkiLz4KPHBhdGggZmlsbC1ydWxlPSJldmVub2RkIiBjbGlwLXJ1bGU9ImV2ZW5vZGQiIGQ9Ik04LjgxODg5IDE4LjgwNzVIMy43MTk1OUwxLjEzOTg5IDIzLjMyNjJMMy43MTk1OSAyNy43ODM4SDguODE4ODlMMTEuMzk4NSAyMy4zMjYyTDguODE4ODkgMTguODA3NVoiIGZpbGw9IiM5OEM5M0UiLz4KPHBhdGggZmlsbC1ydWxlPSJldmVub2RkIiBjbGlwLXJ1bGU9ImV2ZW5vZGQiIGQ9Ik0xOS4wNzc0IDI0LjUwNjdIMTMuOTc4MUwxMS4zOTg0IDI5LjAyNTRMMTMuOTc4MSAzMy40ODNIMTkuMDc3NEwyMS42NTcxIDI5LjAyNTRMMTkuMDc3NCAyNC41MDY3WiIgZmlsbD0iIzYyOEFDNiIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTE4LjgxODEgMjAuNzc4M0gxNC4yMzc3TDExLjkyMDUgMTYuODM5N0wxNC4yMzc3IDEyLjg0NzFIMTguODE4MUwyMS4xMzUyIDE2LjgzOTdMMTguODE4MSAyMC43NzgzWk0xOS42NDQxIDExLjM5ODRIMTMuMzkzM0wxMC4yNTg3IDE2LjgzMUwxMy4zOTMzIDIyLjIyN0gxOS42NDQxTDIyLjc5NyAxNi44MzFMMTkuNjQ0MSAxMS4zOTg0WiIgZmlsbD0iIzM2MzczNiIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTEzLjM5MzIgMjMuMzY2OUwxMC4yNTg3IDI4Ljc5OTVMMTMuMzkzMiAzNC4xOTU0SDE5LjY0NDFMMjIuNzk3IDI4Ljc5OTVMMTkuNjQ0MSAyMy4zNjY5SDEzLjM5MzJaTTExLjkyMDQgMjguODA4MkwxNC4yMzc2IDI0LjgxNTZIMTguODE4TDIxLjEzNTIgMjguODA4MkwxOC44MTggMzIuNzQ2OEgxNC4yMzc2TDExLjkyMDQgMjguODA4MloiIGZpbGw9IiMzNjM3MzYiLz4KPHBhdGggZmlsbC1ydWxlPSJldmVub2RkIiBjbGlwLXJ1bGU9ImV2ZW5vZGQiIGQ9Ik0xMy4zOTMyIDBMMTAuMjU4NyA1LjQzMjYzTDEzLjM5MzIgMTAuODI4NUgxOS42NDQxTDIyLjc5NyA1LjQzMjYzTDE5LjY0NDEgMEgxMy4zOTMyWk0xMS45MjA0IDUuNDQxMkwxNC4yMzc2IDEuNDQ4N0gxOC44MThMMjEuMTM1MiA1LjQ0MTJMMTguODE4IDkuMzc5ODVIMTQuMjM3NkwxMS45MjA0IDUuNDQxMloiIGZpbGw9IiMzNjM3MzYiLz4KPHBhdGggZmlsbC1ydWxlPSJldmVub2RkIiBjbGlwLXJ1bGU9ImV2ZW5vZGQiIGQ9Ik0yMy42NTE4IDE3LjY2NzZMMjAuNTE3MiAyMy4xMDAyTDIzLjY1MTggMjguNDk2MUgyOS45MDI2TDMzLjA1NTUgMjMuMTAwMkwyOS45MDI2IDE3LjY2NzZIMjMuNjUxOFpNMjIuMTc5MSAyMy4xMDg4TDI0LjQ5NjIgMTkuMTE2MkgyOS4wNzY2TDMxLjM5MzcgMjMuMTA4OEwyOS4wNzY2IDI3LjA0NzVIMjQuNDk2MkwyMi4xNzkxIDIzLjEwODhaIiBmaWxsPSIjMzYzNzM2Ii8+CjxwYXRoIGZpbGwtcnVsZT0iZXZlbm9kZCIgY2xpcC1ydWxlPSJldmVub2RkIiBkPSJNMjMuNjUxOCA1LjY5OTIyTDIwLjUxNzIgMTEuMTMxOUwyMy42NTE4IDE2LjUyNzhIMjkuOTAyNkwzMy4wNTU1IDExLjEzMTlMMjkuOTAyNiA1LjY5OTIySDIzLjY1MThaTTIyLjE3OTEgMTEuMTQwNUwyNC40OTYyIDcuMTQ3OTFIMjkuMDc2NkwzMS4zOTM3IDExLjE0MDVMMjkuMDc2NiAxNS4wNzkxSDI0LjQ5NjJMMjIuMTc5MSAxMS4xNDA1WiIgZmlsbD0iIzM2MzczNiIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTMuMTM0NTMgMTcuNjY3NkwwIDIzLjEwMDJMMy4xMzQ1MyAyOC40OTYxSDkuMzg1NDJMMTIuNTM4MyAyMy4xMDAyTDkuMzg1NDIgMTcuNjY3NkgzLjEzNDUzWk0xLjY2MTc5IDIzLjEwODhMMy45Nzg5MiAxOS4xMTYySDguNTU5MzNMMTAuODc2NSAyMy4xMDg4TDguNTU5MzMgMjcuMDQ3NUgzLjk3ODkyTDEuNjYxNzkgMjMuMTA4OFoiIGZpbGw9IiMzNjM3MzYiLz4KPHBhdGggZmlsbC1ydWxlPSJldmVub2RkIiBjbGlwLXJ1bGU9ImV2ZW5vZGQiIGQ9Ik0zLjEzNDUzIDUuNjk5MjJMMCAxMS4xMzE5TDMuMTM0NTMgMTYuNTI3OEg5LjM4NTQyTDEyLjUzODMgMTEuMTMxOUw5LjM4NTQyIDUuNjk5MjJIMy4xMzQ1M1pNMS42NjE3OSAxMS4xNDA1TDMuOTc4OTIgNy4xNDc5MUg4LjU1OTMzTDEwLjg3NjUgMTEuMTQwNUw4LjU1OTMzIDE1LjA3OTFIMy45Nzg5MkwxLjY2MTc5IDExLjE0MDVaIiBmaWxsPSIjMzYzNzM2Ii8+CjxwYXRoIGZpbGwtcnVsZT0iZXZlbm9kZCIgY2xpcC1ydWxlPSJldmVub2RkIiBkPSJNMTE4LjA0NSAyNi4yMjEySDExNS42ODRDMTE1LjY4IDI2LjE1MTEgMTE1LjY3MiAyNi4wNzkgMTE1LjY3MiAyNi4wMDY3QzExNS42NzEgMjUuNDc1NSAxMTUuNjcyIDI0Ljk0NDMgMTE1LjY3MiAyNC40MTMyQzExNS42NzIgMjEuODE5NiAxMTUuNjcgMTkuMjI1OSAxMTUuNjczIDE2LjYzMjNDMTE1LjY3NCAxNi4wMDA0IDExNS42MDkgMTUuMzc5NyAxMTUuNDEyIDE0Ljc3NjlDMTE1LjA1NCAxMy42NzY5IDExNC4yODUgMTMuMDc1OCAxMTMuMTQ4IDEyLjk0MjNDMTExLjkwMiAxMi43OTYgMTEwLjc4NiAxMy4xMTU1IDEwOS44MDcgMTMuOTA4NUMxMDkuMjQ2IDE0LjM2MzQgMTA4Ljc2IDE0Ljg4ODQgMTA4LjMzNiAxNS40NzA2QzEwOC4yOTEgMTUuNTMyMyAxMDguMjc1IDE1LjYxOTMgMTA4LjI2IDE1LjY5NzJDMTA4LjI0OCAxNS43NTY5IDEwOC4yNTcgMTUuODIwOSAxMDguMjU3IDE1Ljg4MzFDMTA4LjI1NyAxOS4yMjE3IDEwOC4yNTcgMjIuNTYwMyAxMDguMjU3IDI1Ljg5OVYyNi4xNzQ1SDEwNS44MTNDMTA1LjgxIDI2LjA5NjkgMTA1LjgwNCAyNi4wMTc4IDEwNS44MDQgMjUuOTM4NUMxMDUuODAzIDI0LjY0MTYgMTA1LjgwMyAyMy4zNDQ5IDEwNS44MDMgMjIuMDQ4QzEwNS44MDMgMjAuMjEzMSAxMDUuODA0IDE4LjM3ODMgMTA1LjgwMyAxNi41NDM0QzEwNS44MDIgMTUuOTE4OCAxMDUuNzIxIDE1LjMwNDkgMTA1LjUxNiAxNC43MTI3QzEwNS4xNSAxMy42NTI0IDEwNC4zODkgMTMuMDc2IDEwMy4yODkgMTIuOTQzOEMxMDEuOTk1IDEyLjc4ODQgMTAwLjg0NyAxMy4xMzU4IDk5Ljg0ODUgMTMuOTc3N0M5OS4zNTQ4IDE0LjM5NCA5OC45MjcxIDE0Ljg2OCA5OC41NTEzIDE1LjM5MTlDOTguNDY2NyAxNS41MDk3IDk4LjQzIDE1LjYyNzMgOTguNDMwMiAxNS43NzMzQzk4LjQzMzkgMTguMTg3NiA5OC40MzI5IDIwLjYwMTkgOTguNDMyOSAyMy4wMTYyQzk4LjQzMjkgMjQuMDAyNyA5OC40MzI4IDI0Ljk4OTEgOTguNDMyOCAyNS45NzU1Qzk4LjQzMjggMjYuMDUwNiA5OC40MzI5IDI2LjEyNTcgOTguNDMyOSAyNi4xOTY2Qzk4LjI2OCAyNi4yNDExIDk2LjQyMDkgMjYuMjU2OCA5Ni4wMDgzIDI2LjIyMTFDOTUuOTYzNSAyNi4wNzg1IDk1Ljk0NzUgMTEuNTE3OSA5NS45OTE5IDExLjIzMjhDOTYuMTM5MiAxMS4xODk4IDk3LjYyOTkgMTEuMTc5OSA5Ny44NzkxIDExLjIyNEM5OC4wMzE5IDExLjkwNDggOTguMTg2MyAxMi41OTM0IDk4LjM1MDYgMTMuMzI1NUM5OC40MzIxIDEzLjIzNzUgOTguNDgzIDEzLjE4NDggOTguNTMxNSAxMy4xMjk4Qzk4Ljg3MzMgMTIuNzQxOCA5OS4yMTEzIDEyLjM1MyA5OS42MjA3IDEyLjAyODZDMTAwLjI5NyAxMS40OTI1IDEwMS4wMzcgMTEuMTA1IDEwMS44OTIgMTAuOTQ2NUMxMDIuODkxIDEwLjc2MTQgMTAzLjg4MSAxMC43NjkzIDEwNC44NTggMTEuMDY3N0MxMDUuNzQyIDExLjMzNzQgMTA2LjQyOCAxMS44ODM4IDEwNi45ODkgMTIuNjAxNkMxMDcuMjM2IDEyLjkxNzkgMTA3LjQ0MSAxMy4yNjA3IDEwNy42MTggMTMuNjIwOUMxMDcuNjQ3IDEzLjY4MTEgMTA3LjY4IDEzLjc0IDEwNy43MjYgMTMuODI4M0MxMDcuNzg5IDEzLjc0NzEgMTA3LjgzNSAxMy42OTA0IDEwNy44NzggMTMuNjMxOEMxMDguMzYyIDEyLjk3ODggMTA4LjkyNCAxMi40MDQ3IDEwOS41NzggMTEuOTIwOUMxMTAuNjUzIDExLjEyNjkgMTExLjg2NSAxMC43OTIxIDExMy4xODkgMTAuODMwNUMxMTMuNzY1IDEwLjg0NzIgMTE0LjMzMiAxMC45NDA1IDExNC44NzggMTEuMTA5QzExNS45NCAxMS40MzYxIDExNi43ODEgMTIuMDQ4NyAxMTcuMzE5IDEzLjA1MTZDMTE3LjczMiAxMy44MTk4IDExNy45NjEgMTQuNjMyNyAxMTguMDEzIDE1LjQ5NzZDMTE4LjAzNSAxNS44NzU5IDExOC4wNDMgMTYuMjU1NiAxMTguMDQ0IDE2LjYzNDdDMTE4LjA0NiAxOS43Mzg5IDExOC4wNDUgMjIuODQzIDExOC4wNDUgMjUuOTQ3QzExOC4wNDUgMjYuMDM1IDExOC4wNDUgMjYuMTIyOSAxMTguMDQ1IDI2LjIyMTJaIiBmaWxsPSJibGFjayIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTg4Ljk5MSAxMS4yMDg5SDkxLjQyOThDOTEuNDM0NiAxMS4yNzM0IDkxLjQ0MjggMTEuMzMzIDkxLjQ0MjggMTEuMzkyN0M5MS40NDMyIDE0LjQ0ODYgOTEuNDQ2MiAxNy41MDQ2IDkxLjQ0IDIwLjU2MDRDOTEuNDM4NiAyMS4yNDM5IDkxLjM5NzMgMjEuOTMwNCA5MS4yMDUgMjIuNTg5MUM5MC42NzQgMjQuNDA3NyA4OS41MTAzIDI1LjYzMTMgODcuNzA0NSAyNi4yMzA4Qzg3LjE5MDQgMjYuNDAxNSA4Ni42NTYzIDI2LjQ2ODYgODYuMTIxIDI2LjUxODVDODUuMTgxMSAyNi42MDYyIDg0LjI0MjcgMjYuNTcyMSA4My4zMjM4IDI2LjM1MzlDODIuMzAwNiAyNi4xMTEgODEuMzY5MSAyNS42Njg1IDgwLjYzOTcgMjQuODg3MkM3OS45NzMxIDI0LjE3MzMgNzkuNTI5NyAyMy4zMzQ4IDc5LjMxMzEgMjIuMzc0OUM3OS4xNzcgMjEuNzcxOCA3OS4xMTgzIDIxLjE2MTcgNzkuMTE2NiAyMC41NDg2Qzc5LjEwODIgMTcuNDkyNyA3OS4xMTIyIDE0LjQzNjggNzkuMTEyMSAxMS4zODA5Qzc5LjExMjEgMTEuMzMzMyA3OS4xMTYyIDExLjI4NTkgNzkuMTE4MiAxMS4yNDE0Qzc5LjI2NjUgMTEuMTg5MSA4MS4zMDYgMTEuMTc1MiA4MS41NzY0IDExLjIyNzRWMTEuNDg0NkM4MS41NzY0IDE0LjQxNjMgODEuNTc2OSAxNy4zNDggODEuNTc1OSAyMC4yNzk4QzgxLjU3NTggMjAuNzk3OSA4MS41OTYzIDIxLjMxMzIgODEuNzA0MSAyMS44MjI4QzgyLjAxOTUgMjMuMzEzOCA4My4wNDcgMjQuMjY3OSA4NC41NTkzIDI0LjQ2NjRDODUuMTY1OSAyNC41NDU5IDg1Ljc3MjggMjQuNTQxNyA4Ni4zNjk1IDI0LjQwNDFDODcuNDU3MiAyNC4xNTMgODguMTk3OCAyMy40Nzk4IDg4LjYzNDMgMjIuNDY2MkM4OC45MjMyIDIxLjc5NSA4OC45ODc1IDIxLjA3OTggODguOTg5MiAyMC4zNTlDODguOTkzNyAxOC40NDEzIDg4Ljk5MDkgMTYuNTIzNiA4OC45OTEgMTQuNjA1OUM4OC45OTEgMTMuNTY0MyA4OC45OTEgMTIuNTIyNiA4OC45OTEgMTEuNDgxVjExLjIwODlaIiBmaWxsPSJibGFjayIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTUyLjg4NDggMTMuNjc4N0M1Mi4yOTk4IDEzLjUwNDMgNTEuNzU1MiAxMy4zMzA2IDUxLjIwNCAxMy4xODA5QzUwLjU2MzYgMTMuMDA2OSA0OS45MTA0IDEyLjkwMjkgNDkuMjQzOSAxMi45MDk0QzQ4LjYxMTkgMTIuOTE1NSA0Ny45OTMyIDEzLjAxNDMgNDcuMzk2NCAxMy4yMjA0QzQ2LjU4NTMgMTMuNTAwNCA0NS45MjE3IDEzLjk4OSA0NS40MTQxIDE0LjY4MjhDNDQuNzgwMSAxNS41NDkzIDQ0LjQyMzMgMTYuNTE5MiA0NC4zMjYxIDE3LjU4ODZDNDQuMjY5OCAxOC4yMDgxIDQ0LjI0NTUgMTguODI3MiA0NC4yOSAxOS40NDc4QzQ0LjM2NTEgMjAuNDk4MiA0NC42NTc3IDIxLjQ3NyA0NS4yNDc2IDIyLjM1OTZDNDUuOTM1OSAyMy4zODk0IDQ2LjkwNDQgMjMuOTk0NSA0OC4xMDE3IDI0LjI0OTZDNDguODk5MyAyNC40MTk2IDQ5LjcwNDMgMjQuNDA0OSA1MC41MTAyIDI0LjMxMjdDNTEuMzAyNyAyNC4yMjE5IDUyLjA2MDQgMjMuOTk1NCA1Mi44MDgxIDIzLjcyODhDNTIuODg0OCAyMy43MDE0IDUyLjk2MjkgMjMuNjc4IDUzLjA1NTcgMjMuNjQ3N1YyNS42ODgzQzUyLjg0NzYgMjUuNzg0MSA1Mi42MzYzIDI1LjkwMTYgNTIuNDExNSAyNS45ODE0QzUxLjI5NjIgMjYuMzc3MSA1MC4xMzk5IDI2LjU1NjEgNDguOTYxMSAyNi41NTMyQzQ3LjczMzQgMjYuNTUwMiA0Ni41NTY1IDI2LjI5ODQgNDUuNDQzMyAyNS43NTU5QzQzLjg3MzYgMjQuOTkxMSA0Mi44MjIgMjMuNzc0MyA0Mi4yMjU4IDIyLjE0NzhDNDEuODY5IDIxLjE3NDQgNDEuNzAyNiAyMC4xNjY2IDQxLjY3MiAxOS4xMzE1QzQxLjYzNjIgMTcuOTIxIDQxLjc3NzEgMTYuNzM1OSA0Mi4xNTUxIDE1LjU4NDRDNDIuODgwMSAxMy4zNzYzIDQ0LjM1NDkgMTEuOTA0OSA0Ni41NDI5IDExLjEzNDlDNDcuMDE1NiAxMC45Njg1IDQ3LjUwMTIgMTAuODkxIDQ3Ljk5NzEgMTAuODQ2M0M0OC41NzQ3IDEwLjc5NDMgNDkuMTUxNiAxMC43NTI4IDQ5LjczMTUgMTAuODAwOEM1MC43NjIzIDEwLjg4NjEgNTEuNzY0NSAxMS4wNzg1IDUyLjY5NjIgMTEuNTU2NkM1Mi44Mzg4IDExLjYyOTcgNTIuODkyNyAxMS43MTEyIDUyLjg4OTIgMTEuODczOEM1Mi44Nzc2IDEyLjQwNDYgNTIuODg0OCAxMi45MzU4IDUyLjg4NDggMTMuNDY2OVYxMy42Nzg3WiIgZmlsbD0iYmxhY2siLz4KPHBhdGggZmlsbC1ydWxlPSJldmVub2RkIiBjbGlwLXJ1bGU9ImV2ZW5vZGQiIGQ9Ik02NC40NTg5IDI2LjE3MjdINjYuODg1MlYzLjMzMzMxSDY0LjQ1ODlWMjYuMTcyN1oiIGZpbGw9ImJsYWNrIi8+CjxwYXRoIGZpbGwtcnVsZT0iZXZlbm9kZCIgY2xpcC1ydWxlPSJldmVub2RkIiBkPSJNNTkuMzg3MiAyNi4xNzU0SDU2Ljk5MDZDNTYuOTc5NiAyNi4xNjczIDU2Ljk3MzEgMjYuMTY0MSA1Ni45Njg4IDI2LjE1OUM1Ni45NjQ1IDI2LjE1NDEgNTYuOTYwNyAyNi4xNDc1IDU2Ljk1OTcgMjYuMTQxMkM1Ni45NTQ2IDI2LjEwNzMgNTYuOTQ2NSAyNi4wNzM0IDU2Ljk0NjUgMjYuMDM5NUM1Ni45NDY4IDIxLjEyMjQgNTYuOTQ3NyAxNi4yMDUyIDU2Ljk0OTEgMTEuMjg4MUM1Ni45NDkyIDExLjI2ODYgNTYuOTU4OSAxMS4yNDkzIDU2Ljk2MzYgMTEuMjMxNEM1Ny4xMTk3IDExLjE5MDEgNTkuMTQ0MSAxMS4xODA5IDU5LjM4NzIgMTEuMjIyMVYyNi4xNzU0WiIgZmlsbD0iYmxhY2siLz4KPHBhdGggZmlsbC1ydWxlPSJldmVub2RkIiBjbGlwLXJ1bGU9ImV2ZW5vZGQiIGQ9Ik03MS45NTU4IDExLjIwOTRINzQuMzU5N0M3NC40MDQ2IDExLjM1ODMgNzQuNDE5MSAyNS44OTY2IDc0LjM3MzggMjYuMTcyOEg3MS45NTU4VjExLjIwOTRaIiBmaWxsPSJibGFjayIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTU5LjMzMzYgNy42ODU5N0g1Ni45Mjg5QzU2Ljg4NjQgNy41MzEyNiA1Ni44NzcxIDUuMjE1NjcgNTYuOTE4OCA0Ljk3MTM3SDU5LjMyNEM1OS4zNjM3IDUuMTIwMDYgNTkuMzczOSA3LjQxMDg3IDU5LjMzMzYgNy42ODU5N1oiIGZpbGw9ImJsYWNrIi8+CjxwYXRoIGZpbGwtcnVsZT0iZXZlbm9kZCIgY2xpcC1ydWxlPSJldmVub2RkIiBkPSJNNzEuOTEyOCA0Ljk2Mjc3SDc0LjMxMDRDNzQuMzU4OSA1LjEwODY1IDc0LjM3NzggNy4yNjk5MyA3NC4zMzM5IDcuNjc3NDZINzEuOTEyOFY0Ljk2Mjc3WiIgZmlsbD0iYmxhY2siLz4KPC9zdmc+", " mediatype: image/svg+xml", " install:", " spec:", " clusterPermissions:", " - rules:", " - apiGroups:", " - security.openshift.io", " resourceNames:", " - hostnetwork", " resources:", " - securitycontextconstraints", " verbs:", " - use", " - apiGroups:", " - rbac.authorization.k8s.io", " resources:", " - clusterroles", " - clusterrolebindings", " verbs:", " - create", " - get", " - patch", " - update", " - delete", " - list", " - watch", " - apiGroups:", " - cilium.io", " resources:", " - '*'", " verbs:", " - '*'", " - apiGroups:", " - apiextensions.k8s.io", " resources:", " - customresourcedefinitions", " verbs:", " - '*'", " - apiGroups:", " - coordination.k8s.io", " resources:", " - leases", " verbs:", " - create", " - get", " - update", " - apiGroups:", " - \"\"", " resources:", " - services/status", " verbs:", " - update", " - apiGroups:", " - \"\"", " resources:", " - pods", " - pods/status", " - pods/finalizers", " verbs:", " - get", " - list", " - watch", " - update", " - delete", " - apiGroups:", " - \"\"", " resources:", " - nodes", " - nodes/status", " verbs:", " - get", " - list", " - watch", " - update", " - patch", " - apiGroups:", " - \"\"", " resources:", " - namespaces", " - services", " - endpoints", " - componentstatuses", " verbs:", " - get", " - list", " - watch", " - apiGroups:", " - discovery.k8s.io", " resources:", " - endpointslices", " verbs:", " - get", " - list", " - watch", " - apiGroups:", " - networking.k8s.io", " resources:", " - networkpolicies", " verbs:", " - get", " - list", " - watch", " serviceAccountName: cilium-olm", " deployments:", " - name: cilium-olm", " spec:", " replicas: 1", " selector:", " matchLabels:", " name: cilium-olm", " template:", " metadata:", " labels:", " name: cilium-olm", " spec:", " containers:", " - command:", " - /usr/local/bin/helm-operator", " - run", " - --watches-file=watches.yaml", " - --enable-leader-election", " - --leader-election-id=cilium-olm", " - --zap-devel", " env:", " - name: WATCH_NAMESPACE", " valueFrom:", " fieldRef:", " fieldPath: metadata.namespace", " image: registry.connect.redhat.com/isovalent/cilium-olm@sha256:26f1ed31c8f0600fcea498116e7dbea157a8704989f762e22e8038b8ea364dce", " name: operator", " ports:", " - containerPort: 9443", " name: https", " protocol: TCP", " resources:", " limits:", " cpu: 100m", " memory: 150Mi", " requests:", " cpu: 100m", " memory: 150Mi", " volumeMounts:", " - mountPath: /tmp", " name: tmp", " hostNetwork: true", " serviceAccount: cilium-olm", " terminationGracePeriodSeconds: 10", " tolerations:", " - operator: Exists", " volumes:", " - emptyDir: {}", " name: tmp", " permissions:", " - rules:", " - apiGroups:", " - \"\"", " resources:", " - configmaps", " verbs:", " - get", " - list", " - watch", " - create", " - update", " - patch", " - delete", " - apiGroups:", " - \"\"", " resources:", " - events", " verbs:", " - create", " - apiGroups:", " - \"\"", " resources:", " - namespaces", " verbs:", " - get", " - apiGroups:", " - cilium.io", " resources:", " - ciliumconfigs", " - ciliumconfigs/status", " verbs:", " - list", " - apiGroups:", " - cilium.io", " resources:", " - ciliumconfigs", " - ciliumconfigs/status", " - ciliumconfigs/finalizers", " verbs:", " - get", " - patch", " - update", " - watch", " - list", " - delete", " - apiGroups:", " - \"\"", " resources:", " - events", " verbs:", " - create", " - apiGroups:", " - \"\"", " resources:", " - secrets", " verbs:", " - '*'", " - apiGroups:", " - \"\"", " resources:", " - serviceaccounts", " - configmaps", " - secrets", " - services", " verbs:", " - '*'", " - apiGroups:", " - apps", " resources:", " - deployments", " - daemonsets", " verbs:", " - '*'", " serviceAccountName: cilium-olm", " strategy: deployment", " installModes:", " - supported: true", " type: OwnNamespace", " - supported: true", " type: SingleNamespace", " - supported: false", " type: MultiNamespace", " - supported: false", " type: AllNamespaces", " keywords:", " - networking", " - security", " - observability", " - eBPF", " links:", " - name: Cilium Homepage", " url: https://cilium.io/", " maintainers:", " - email: [email protected]", " name: Cilium", " maturity: stable", " provider:", " name: Isovalent", " version: 1.10.1+xdcd9835", " relatedImages:", " - name: operator", " image: registry.connect.redhat.com/isovalent/cilium-olm@sha256:26f1ed31c8f0600fcea498116e7dbea157a8704989f762e22e8038b8ea364dce"]}
2021-06-25 12:57:41,939 p=23 u=default n=ansible | TASK [parse_operator_bundle : Set facts for csv_data] **************************
2021-06-25 12:57:42,073 p=23 u=default n=ansible | ok: [localhost] => {"ansible_facts": {"csv_vars": "apiVersion: operators.coreos.com/v1alpha1\nkind: ClusterServiceVersion\nmetadata:\n annotations:\n alm-examples: '[{\"apiVersion\":\"cilium.io/v1alpha1\",\"kind\":\"CiliumConfig\",\"metadata\":{\"name\":\"cilium-openshift-default\",\"namespace\":\"placeholder\"},\"spec\":{\"nativeRoutingCIDR\":\"10.128.0.0/14\",\"endpointRoutes\":{\"enabled\":true},\"kubeProxyReplacement\":\"probe\",\"cni\":{\"binPath\":\"/var/lib/cni/bin\",\"confPath\":\"/var/run/multus/cni/net.d\"},\"ipam\":{\"operator\":{\"clusterPoolIPv4PodCIDR\":\"10.128.0.0/14\",\"clusterPoolIPv4MaskSize\":\"23\"},\"mode\":\"cluster-pool\"},\"prometheus\":{\"serviceMonitor\":{\"enabled\":false}},\"hubble\":{\"tls\":{\"enabled\":false}}}}]'\n alm-examples-metadata: '{\"cilium-openshift-default\":{\"description\":\"Default CiliumConfig CR for OpenShift\"}}'\n capabilities: Basic Install\n categories: Networking,Security\n repository: http://github.com/cilium/cilium\n support: [email protected]\n name: cilium.v1.10.1-xdcd9835\n namespace: placeholder\nspec:\n apiservicedefinitions: {}\n customresourcedefinitions:\n owned:\n - kind: CiliumConfig\n name: ciliumconfigs.cilium.io\n resources:\n - kind: DaemonSet\n name: cilium\n version: v1\n - kind: Deployment\n name: cilium-operator\n version: v1\n - kind: ConfigMap\n name: cilium-config\n version: v1\n statusDescriptors:\n - description: Helm release conditions\n displayName: Conditions\n path: conditions\n - description: Name of deployed Helm release\n displayName: Deployed release\n path: deployedRelease\n version: v1alpha1\n description: Cilium - eBPF-based Networking, Security, and Observability\n displayName: Cilium\n icon:\n - base64data: PHN2ZyB3aWR0aD0iMTE5IiBoZWlnaHQ9IjM1IiB2aWV3Qm94PSIwIDAgMTE5IDM1IiBmaWxsPSJub25lIiB4bWxucz0iaHR0cDovL3d3dy53My5vcmcvMjAwMC9zdmciPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTI5LjMzNjEgMTguODA3NUgyNC4yMzY4TDIxLjY1NzEgMjMuMzI2MkwyNC4yMzY4IDI3Ljc4MzhIMjkuMzM2MUwzMS45MTU3IDIzLjMyNjJMMjkuMzM2MSAxOC44MDc1WiIgZmlsbD0iIzgwNjFBOSIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTI5LjMzNjEgNi44MzkwNUgyNC4yMzY4TDIxLjY1NzEgMTEuMzU3N0wyNC4yMzY4IDE1LjgxNTNIMjkuMzM2MUwzMS45MTU3IDExLjM1NzdMMjkuMzM2MSA2LjgzOTA1WiIgZmlsbD0iI0YxNzMyMyIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTE5LjA3NzQgMS4xMzk4M0gxMy45NzgxTDExLjM5ODQgNS42NTg1MkwxMy45NzgxIDEwLjExNjFIMTkuMDc3NEwyMS42NTcxIDUuNjU4NTJMMTkuMDc3NCAxLjEzOTgzWiIgZmlsbD0iI0Y4QzUxNyIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTguODE4ODkgNi44MzkwNUgzLjcxOTU5TDEuMTM5ODkgMTEuMzU3N0wzLjcxOTU5IDE1LjgxNTNIOC44MTg4OUwxMS4zOTg1IDExLjM1NzdMOC44MTg4OSA2LjgzOTA1WiIgZmlsbD0iI0NBREQ3MiIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTE5LjA3NzQgMTIuNTM4M0gxMy45NzgxTDExLjM5ODQgMTcuMDU3TDEzLjk3ODEgMjEuNTE0NkgxOS4wNzc0TDIxLjY1NzEgMTcuMDU3TDE5LjA3NzQgMTIuNTM4M1oiIGZpbGw9IiNFODI2MjkiLz4KPHBhdGggZmlsbC1ydWxlPSJldmVub2RkIiBjbGlwLXJ1bGU9ImV2ZW5vZGQiIGQ9Ik04LjgxODg5IDE4LjgwNzVIMy43MTk1OUwxLjEzOTg5IDIzLjMyNjJMMy43MTk1OSAyNy43ODM4SDguODE4ODlMMTEuMzk4NSAyMy4zMjYyTDguODE4ODkgMTguODA3NVoiIGZpbGw9IiM5OEM5M0UiLz4KPHBhdGggZmlsbC1ydWxlPSJldmVub2RkIiBjbGlwLXJ1bGU9ImV2ZW5vZGQiIGQ9Ik0xOS4wNzc0IDI0LjUwNjdIMTMuOTc4MUwxMS4zOTg0IDI5LjAyNTRMMTMuOTc4MSAzMy40ODNIMTkuMDc3NEwyMS42NTcxIDI5LjAyNTRMMTkuMDc3NCAyNC41MDY3WiIgZmlsbD0iIzYyOEFDNiIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTE4LjgxODEgMjAuNzc4M0gxNC4yMzc3TDExLjkyMDUgMTYuODM5N0wxNC4yMzc3IDEyLjg0NzFIMTguODE4MUwyMS4xMzUyIDE2LjgzOTdMMTguODE4MSAyMC43NzgzWk0xOS42NDQxIDExLjM5ODRIMTMuMzkzM0wxMC4yNTg3IDE2LjgzMUwxMy4zOTMzIDIyLjIyN0gxOS42NDQxTDIyLjc5NyAxNi44MzFMMTkuNjQ0MSAxMS4zOTg0WiIgZmlsbD0iIzM2MzczNiIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTEzLjM5MzIgMjMuMzY2OUwxMC4yNTg3IDI4Ljc5OTVMMTMuMzkzMiAzNC4xOTU0SDE5LjY0NDFMMjIuNzk3IDI4Ljc5OTVMMTkuNjQ0MSAyMy4zNjY5SDEzLjM5MzJaTTExLjkyMDQgMjguODA4MkwxNC4yMzc2IDI0LjgxNTZIMTguODE4TDIxLjEzNTIgMjguODA4MkwxOC44MTggMzIuNzQ2OEgxNC4yMzc2TDExLjkyMDQgMjguODA4MloiIGZpbGw9IiMzNjM3MzYiLz4KPHBhdGggZmlsbC1ydWxlPSJldmVub2RkIiBjbGlwLXJ1bGU9ImV2ZW5vZGQiIGQ9Ik0xMy4zOTMyIDBMMTAuMjU4NyA1LjQzMjYzTDEzLjM5MzIgMTAuODI4NUgxOS42NDQxTDIyLjc5NyA1LjQzMjYzTDE5LjY0NDEgMEgxMy4zOTMyWk0xMS45MjA0IDUuNDQxMkwxNC4yMzc2IDEuNDQ4N0gxOC44MThMMjEuMTM1MiA1LjQ0MTJMMTguODE4IDkuMzc5ODVIMTQuMjM3NkwxMS45MjA0IDUuNDQxMloiIGZpbGw9IiMzNjM3MzYiLz4KPHBhdGggZmlsbC1ydWxlPSJldmVub2RkIiBjbGlwLXJ1bGU9ImV2ZW5vZGQiIGQ9Ik0yMy42NTE4IDE3LjY2NzZMMjAuNTE3MiAyMy4xMDAyTDIzLjY1MTggMjguNDk2MUgyOS45MDI2TDMzLjA1NTUgMjMuMTAwMkwyOS45MDI2IDE3LjY2NzZIMjMuNjUxOFpNMjIuMTc5MSAyMy4xMDg4TDI0LjQ5NjIgMTkuMTE2MkgyOS4wNzY2TDMxLjM5MzcgMjMuMTA4OEwyOS4wNzY2IDI3LjA0NzVIMjQuNDk2MkwyMi4xNzkxIDIzLjEwODhaIiBmaWxsPSIjMzYzNzM2Ii8+CjxwYXRoIGZpbGwtcnVsZT0iZXZlbm9kZCIgY2xpcC1ydWxlPSJldmVub2RkIiBkPSJNMjMuNjUxOCA1LjY5OTIyTDIwLjUxNzIgMTEuMTMxOUwyMy42NTE4IDE2LjUyNzhIMjkuOTAyNkwzMy4wNTU1IDExLjEzMTlMMjkuOTAyNiA1LjY5OTIySDIzLjY1MThaTTIyLjE3OTEgMTEuMTQwNUwyNC40OTYyIDcuMTQ3OTFIMjkuMDc2NkwzMS4zOTM3IDExLjE0MDVMMjkuMDc2NiAxNS4wNzkxSDI0LjQ5NjJMMjIuMTc5MSAxMS4xNDA1WiIgZmlsbD0iIzM2MzczNiIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTMuMTM0NTMgMTcuNjY3NkwwIDIzLjEwMDJMMy4xMzQ1MyAyOC40OTYxSDkuMzg1NDJMMTIuNTM4MyAyMy4xMDAyTDkuMzg1NDIgMTcuNjY3NkgzLjEzNDUzWk0xLjY2MTc5IDIzLjEwODhMMy45Nzg5MiAxOS4xMTYySDguNTU5MzNMMTAuODc2NSAyMy4xMDg4TDguNTU5MzMgMjcuMDQ3NUgzLjk3ODkyTDEuNjYxNzkgMjMuMTA4OFoiIGZpbGw9IiMzNjM3MzYiLz4KPHBhdGggZmlsbC1ydWxlPSJldmVub2RkIiBjbGlwLXJ1bGU9ImV2ZW5vZGQiIGQ9Ik0zLjEzNDUzIDUuNjk5MjJMMCAxMS4xMzE5TDMuMTM0NTMgMTYuNTI3OEg5LjM4NTQyTDEyLjUzODMgMTEuMTMxOUw5LjM4NTQyIDUuNjk5MjJIMy4xMzQ1M1pNMS42NjE3OSAxMS4xNDA1TDMuOTc4OTIgNy4xNDc5MUg4LjU1OTMzTDEwLjg3NjUgMTEuMTQwNUw4LjU1OTMzIDE1LjA3OTFIMy45Nzg5MkwxLjY2MTc5IDExLjE0MDVaIiBmaWxsPSIjMzYzNzM2Ii8+CjxwYXRoIGZpbGwtcnVsZT0iZXZlbm9kZCIgY2xpcC1ydWxlPSJldmVub2RkIiBkPSJNMTE4LjA0NSAyNi4yMjEySDExNS42ODRDMTE1LjY4IDI2LjE1MTEgMTE1LjY3MiAyNi4wNzkgMTE1LjY3MiAyNi4wMDY3QzExNS42NzEgMjUuNDc1NSAxMTUuNjcyIDI0Ljk0NDMgMTE1LjY3MiAyNC40MTMyQzExNS42NzIgMjEuODE5NiAxMTUuNjcgMTkuMjI1OSAxMTUuNjczIDE2LjYzMjNDMTE1LjY3NCAxNi4wMDA0IDExNS42MDkgMTUuMzc5NyAxMTUuNDEyIDE0Ljc3NjlDMTE1LjA1NCAxMy42NzY5IDExNC4yODUgMTMuMDc1OCAxMTMuMTQ4IDEyLjk0MjNDMTExLjkwMiAxMi43OTYgMTEwLjc4NiAxMy4xMTU1IDEwOS44MDcgMTMuOTA4NUMxMDkuMjQ2IDE0LjM2MzQgMTA4Ljc2IDE0Ljg4ODQgMTA4LjMzNiAxNS40NzA2QzEwOC4yOTEgMTUuNTMyMyAxMDguMjc1IDE1LjYxOTMgMTA4LjI2IDE1LjY5NzJDMTA4LjI0OCAxNS43NTY5IDEwOC4yNTcgMTUuODIwOSAxMDguMjU3IDE1Ljg4MzFDMTA4LjI1NyAxOS4yMjE3IDEwOC4yNTcgMjIuNTYwMyAxMDguMjU3IDI1Ljg5OVYyNi4xNzQ1SDEwNS44MTNDMTA1LjgxIDI2LjA5NjkgMTA1LjgwNCAyNi4wMTc4IDEwNS44MDQgMjUuOTM4NUMxMDUuODAzIDI0LjY0MTYgMTA1LjgwMyAyMy4zNDQ5IDEwNS44MDMgMjIuMDQ4QzEwNS44MDMgMjAuMjEzMSAxMDUuODA0IDE4LjM3ODMgMTA1LjgwMyAxNi41NDM0QzEwNS44MDIgMTUuOTE4OCAxMDUuNzIxIDE1LjMwNDkgMTA1LjUxNiAxNC43MTI3QzEwNS4xNSAxMy42NTI0IDEwNC4zODkgMTMuMDc2IDEwMy4yODkgMTIuOTQzOEMxMDEuOTk1IDEyLjc4ODQgMTAwLjg0NyAxMy4xMzU4IDk5Ljg0ODUgMTMuOTc3N0M5OS4zNTQ4IDE0LjM5NCA5OC45MjcxIDE0Ljg2OCA5OC41NTEzIDE1LjM5MTlDOTguNDY2NyAxNS41MDk3IDk4LjQzIDE1LjYyNzMgOTguNDMwMiAxNS43NzMzQzk4LjQzMzkgMTguMTg3NiA5OC40MzI5IDIwLjYwMTkgOTguNDMyOSAyMy4wMTYyQzk4LjQzMjkgMjQuMDAyNyA5OC40MzI4IDI0Ljk4OTEgOTguNDMyOCAyNS45NzU1Qzk4LjQzMjggMjYuMDUwNiA5OC40MzI5IDI2LjEyNTcgOTguNDMyOSAyNi4xOTY2Qzk4LjI2OCAyNi4yNDExIDk2LjQyMDkgMjYuMjU2OCA5Ni4wMDgzIDI2LjIyMTFDOTUuOTYzNSAyNi4wNzg1IDk1Ljk0NzUgMTEuNTE3OSA5NS45OTE5IDExLjIzMjhDOTYuMTM5MiAxMS4xODk4IDk3LjYyOTkgMTEuMTc5OSA5Ny44NzkxIDExLjIyNEM5OC4wMzE5IDExLjkwNDggOTguMTg2MyAxMi41OTM0IDk4LjM1MDYgMTMuMzI1NUM5OC40MzIxIDEzLjIzNzUgOTguNDgzIDEzLjE4NDggOTguNTMxNSAxMy4xMjk4Qzk4Ljg3MzMgMTIuNzQxOCA5OS4yMTEzIDEyLjM1MyA5OS42MjA3IDEyLjAyODZDMTAwLjI5NyAxMS40OTI1IDEwMS4wMzcgMTEuMTA1IDEwMS44OTIgMTAuOTQ2NUMxMDIuODkxIDEwLjc2MTQgMTAzLjg4MSAxMC43NjkzIDEwNC44NTggMTEuMDY3N0MxMDUuNzQyIDExLjMzNzQgMTA2LjQyOCAxMS44ODM4IDEwNi45ODkgMTIuNjAxNkMxMDcuMjM2IDEyLjkxNzkgMTA3LjQ0MSAxMy4yNjA3IDEwNy42MTggMTMuNjIwOUMxMDcuNjQ3IDEzLjY4MTEgMTA3LjY4IDEzLjc0IDEwNy43MjYgMTMuODI4M0MxMDcuNzg5IDEzLjc0NzEgMTA3LjgzNSAxMy42OTA0IDEwNy44NzggMTMuNjMxOEMxMDguMzYyIDEyLjk3ODggMTA4LjkyNCAxMi40MDQ3IDEwOS41NzggMTEuOTIwOUMxMTAuNjUzIDExLjEyNjkgMTExLjg2NSAxMC43OTIxIDExMy4xODkgMTAuODMwNUMxMTMuNzY1IDEwLjg0NzIgMTE0LjMzMiAxMC45NDA1IDExNC44NzggMTEuMTA5QzExNS45NCAxMS40MzYxIDExNi43ODEgMTIuMDQ4NyAxMTcuMzE5IDEzLjA1MTZDMTE3LjczMiAxMy44MTk4IDExNy45NjEgMTQuNjMyNyAxMTguMDEzIDE1LjQ5NzZDMTE4LjAzNSAxNS44NzU5IDExOC4wNDMgMTYuMjU1NiAxMTguMDQ0IDE2LjYzNDdDMTE4LjA0NiAxOS43Mzg5IDExOC4wNDUgMjIuODQzIDExOC4wNDUgMjUuOTQ3QzExOC4wNDUgMjYuMDM1IDExOC4wNDUgMjYuMTIyOSAxMTguMDQ1IDI2LjIyMTJaIiBmaWxsPSJibGFjayIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTg4Ljk5MSAxMS4yMDg5SDkxLjQyOThDOTEuNDM0NiAxMS4yNzM0IDkxLjQ0MjggMTEuMzMzIDkxLjQ0MjggMTEuMzkyN0M5MS40NDMyIDE0LjQ0ODYgOTEuNDQ2MiAxNy41MDQ2IDkxLjQ0IDIwLjU2MDRDOTEuNDM4NiAyMS4yNDM5IDkxLjM5NzMgMjEuOTMwNCA5MS4yMDUgMjIuNTg5MUM5MC42NzQgMjQuNDA3NyA4OS41MTAzIDI1LjYzMTMgODcuNzA0NSAyNi4yMzA4Qzg3LjE5MDQgMjYuNDAxNSA4Ni42NTYzIDI2LjQ2ODYgODYuMTIxIDI2LjUxODVDODUuMTgxMSAyNi42MDYyIDg0LjI0MjcgMjYuNTcyMSA4My4zMjM4IDI2LjM1MzlDODIuMzAwNiAyNi4xMTEgODEuMzY5MSAyNS42Njg1IDgwLjYzOTcgMjQuODg3MkM3OS45NzMxIDI0LjE3MzMgNzkuNTI5NyAyMy4zMzQ4IDc5LjMxMzEgMjIuMzc0OUM3OS4xNzcgMjEuNzcxOCA3OS4xMTgzIDIxLjE2MTcgNzkuMTE2NiAyMC41NDg2Qzc5LjEwODIgMTcuNDkyNyA3OS4xMTIyIDE0LjQzNjggNzkuMTEyMSAxMS4zODA5Qzc5LjExMjEgMTEuMzMzMyA3OS4xMTYyIDExLjI4NTkgNzkuMTE4MiAxMS4yNDE0Qzc5LjI2NjUgMTEuMTg5MSA4MS4zMDYgMTEuMTc1MiA4MS41NzY0IDExLjIyNzRWMTEuNDg0NkM4MS41NzY0IDE0LjQxNjMgODEuNTc2OSAxNy4zNDggODEuNTc1OSAyMC4yNzk4QzgxLjU3NTggMjAuNzk3OSA4MS41OTYzIDIxLjMxMzIgODEuNzA0MSAyMS44MjI4QzgyLjAxOTUgMjMuMzEzOCA4My4wNDcgMjQuMjY3OSA4NC41NTkzIDI0LjQ2NjRDODUuMTY1OSAyNC41NDU5IDg1Ljc3MjggMjQuNTQxNyA4Ni4zNjk1IDI0LjQwNDFDODcuNDU3MiAyNC4xNTMgODguMTk3OCAyMy40Nzk4IDg4LjYzNDMgMjIuNDY2MkM4OC45MjMyIDIxLjc5NSA4OC45ODc1IDIxLjA3OTggODguOTg5MiAyMC4zNTlDODguOTkzNyAxOC40NDEzIDg4Ljk5MDkgMTYuNTIzNiA4OC45OTEgMTQuNjA1OUM4OC45OTEgMTMuNTY0MyA4OC45OTEgMTIuNTIyNiA4OC45OTEgMTEuNDgxVjExLjIwODlaIiBmaWxsPSJibGFjayIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTUyLjg4NDggMTMuNjc4N0M1Mi4yOTk4IDEzLjUwNDMgNTEuNzU1MiAxMy4zMzA2IDUxLjIwNCAxMy4xODA5QzUwLjU2MzYgMTMuMDA2OSA0OS45MTA0IDEyLjkwMjkgNDkuMjQzOSAxMi45MDk0QzQ4LjYxMTkgMTIuOTE1NSA0Ny45OTMyIDEzLjAxNDMgNDcuMzk2NCAxMy4yMjA0QzQ2LjU4NTMgMTMuNTAwNCA0NS45MjE3IDEzLjk4OSA0NS40MTQxIDE0LjY4MjhDNDQuNzgwMSAxNS41NDkzIDQ0LjQyMzMgMTYuNTE5MiA0NC4zMjYxIDE3LjU4ODZDNDQuMjY5OCAxOC4yMDgxIDQ0LjI0NTUgMTguODI3MiA0NC4yOSAxOS40NDc4QzQ0LjM2NTEgMjAuNDk4MiA0NC42NTc3IDIxLjQ3NyA0NS4yNDc2IDIyLjM1OTZDNDUuOTM1OSAyMy4zODk0IDQ2LjkwNDQgMjMuOTk0NSA0OC4xMDE3IDI0LjI0OTZDNDguODk5MyAyNC40MTk2IDQ5LjcwNDMgMjQuNDA0OSA1MC41MTAyIDI0LjMxMjdDNTEuMzAyNyAyNC4yMjE5IDUyLjA2MDQgMjMuOTk1NCA1Mi44MDgxIDIzLjcyODhDNTIuODg0OCAyMy43MDE0IDUyLjk2MjkgMjMuNjc4IDUzLjA1NTcgMjMuNjQ3N1YyNS42ODgzQzUyLjg0NzYgMjUuNzg0MSA1Mi42MzYzIDI1LjkwMTYgNTIuNDExNSAyNS45ODE0QzUxLjI5NjIgMjYuMzc3MSA1MC4xMzk5IDI2LjU1NjEgNDguOTYxMSAyNi41NTMyQzQ3LjczMzQgMjYuNTUwMiA0Ni41NTY1IDI2LjI5ODQgNDUuNDQzMyAyNS43NTU5QzQzLjg3MzYgMjQuOTkxMSA0Mi44MjIgMjMuNzc0MyA0Mi4yMjU4IDIyLjE0NzhDNDEuODY5IDIxLjE3NDQgNDEuNzAyNiAyMC4xNjY2IDQxLjY3MiAxOS4xMzE1QzQxLjYzNjIgMTcuOTIxIDQxLjc3NzEgMTYuNzM1OSA0Mi4xNTUxIDE1LjU4NDRDNDIuODgwMSAxMy4zNzYzIDQ0LjM1NDkgMTEuOTA0OSA0Ni41NDI5IDExLjEzNDlDNDcuMDE1NiAxMC45Njg1IDQ3LjUwMTIgMTAuODkxIDQ3Ljk5NzEgMTAuODQ2M0M0OC41NzQ3IDEwLjc5NDMgNDkuMTUxNiAxMC43NTI4IDQ5LjczMTUgMTAuODAwOEM1MC43NjIzIDEwLjg4NjEgNTEuNzY0NSAxMS4wNzg1IDUyLjY5NjIgMTEuNTU2NkM1Mi44Mzg4IDExLjYyOTcgNTIuODkyNyAxMS43MTEyIDUyLjg4OTIgMTEuODczOEM1Mi44Nzc2IDEyLjQwNDYgNTIuODg0OCAxMi45MzU4IDUyLjg4NDggMTMuNDY2OVYxMy42Nzg3WiIgZmlsbD0iYmxhY2siLz4KPHBhdGggZmlsbC1ydWxlPSJldmVub2RkIiBjbGlwLXJ1bGU9ImV2ZW5vZGQiIGQ9Ik02NC40NTg5IDI2LjE3MjdINjYuODg1MlYzLjMzMzMxSDY0LjQ1ODlWMjYuMTcyN1oiIGZpbGw9ImJsYWNrIi8+CjxwYXRoIGZpbGwtcnVsZT0iZXZlbm9kZCIgY2xpcC1ydWxlPSJldmVub2RkIiBkPSJNNTkuMzg3MiAyNi4xNzU0SDU2Ljk5MDZDNTYuOTc5NiAyNi4xNjczIDU2Ljk3MzEgMjYuMTY0MSA1Ni45Njg4IDI2LjE1OUM1Ni45NjQ1IDI2LjE1NDEgNTYuOTYwNyAyNi4xNDc1IDU2Ljk1OTcgMjYuMTQxMkM1Ni45NTQ2IDI2LjEwNzMgNTYuOTQ2NSAyNi4wNzM0IDU2Ljk0NjUgMjYuMDM5NUM1Ni45NDY4IDIxLjEyMjQgNTYuOTQ3NyAxNi4yMDUyIDU2Ljk0OTEgMTEuMjg4MUM1Ni45NDkyIDExLjI2ODYgNTYuOTU4OSAxMS4yNDkzIDU2Ljk2MzYgMTEuMjMxNEM1Ny4xMTk3IDExLjE5MDEgNTkuMTQ0MSAxMS4xODA5IDU5LjM4NzIgMTEuMjIyMVYyNi4xNzU0WiIgZmlsbD0iYmxhY2siLz4KPHBhdGggZmlsbC1ydWxlPSJldmVub2RkIiBjbGlwLXJ1bGU9ImV2ZW5vZGQiIGQ9Ik03MS45NTU4IDExLjIwOTRINzQuMzU5N0M3NC40MDQ2IDExLjM1ODMgNzQuNDE5MSAyNS44OTY2IDc0LjM3MzggMjYuMTcyOEg3MS45NTU4VjExLjIwOTRaIiBmaWxsPSJibGFjayIvPgo8cGF0aCBmaWxsLXJ1bGU9ImV2ZW5vZGQiIGNsaXAtcnVsZT0iZXZlbm9kZCIgZD0iTTU5LjMzMzYgNy42ODU5N0g1Ni45Mjg5QzU2Ljg4NjQgNy41MzEyNiA1Ni44NzcxIDUuMjE1NjcgNTYuOTE4OCA0Ljk3MTM3SDU5LjMyNEM1OS4zNjM3IDUuMTIwMDYgNTkuMzczOSA3LjQxMDg3IDU5LjMzMzYgNy42ODU5N1oiIGZpbGw9ImJsYWNrIi8+CjxwYXRoIGZpbGwtcnVsZT0iZXZlbm9kZCIgY2xpcC1ydWxlPSJldmVub2RkIiBkPSJNNzEuOTEyOCA0Ljk2Mjc3SDc0LjMxMDRDNzQuMzU4OSA1LjEwODY1IDc0LjM3NzggNy4yNjk5MyA3NC4zMzM5IDcuNjc3NDZINzEuOTEyOFY0Ljk2Mjc3WiIgZmlsbD0iYmxhY2siLz4KPC9zdmc+\n mediatype: image/svg+xml\n install:\n spec:\n clusterPermissions:\n - rules:\n - apiGroups:\n - security.openshift.io\n resourceNames:\n - hostnetwork\n resources:\n - securitycontextconstraints\n verbs:\n - use\n - apiGroups:\n - rbac.authorization.k8s.io\n resources:\n - clusterroles\n - clusterrolebindings\n verbs:\n - create\n - get\n - patch\n - update\n - delete\n - list\n - watch\n - apiGroups:\n - cilium.io\n resources:\n - '*'\n verbs:\n - '*'\n - apiGroups:\n - apiextensions.k8s.io\n resources:\n - customresourcedefinitions\n verbs:\n - '*'\n - apiGroups:\n - coordination.k8s.io\n resources:\n - leases\n verbs:\n - create\n - get\n - update\n - apiGroups:\n - \"\"\n resources:\n - services/status\n verbs:\n - update\n - apiGroups:\n - \"\"\n resources:\n - pods\n - pods/status\n - pods/finalizers\n verbs:\n - get\n - list\n - watch\n - update\n - delete\n - apiGroups:\n - \"\"\n resources:\n - nodes\n - nodes/status\n verbs:\n - get\n - list\n - watch\n - update\n - patch\n - apiGroups:\n - \"\"\n resources:\n - namespaces\n - services\n - endpoints\n - componentstatuses\n verbs:\n - get\n - list\n - watch\n - apiGroups:\n - discovery.k8s.io\n resources:\n - endpointslices\n verbs:\n - get\n - list\n - watch\n - apiGroups:\n - networking.k8s.io\n resources:\n - networkpolicies\n verbs:\n - get\n - list\n - watch\n serviceAccountName: cilium-olm\n deployments:\n - name: cilium-olm\n spec:\n replicas: 1\n selector:\n matchLabels:\n name: cilium-olm\n template:\n metadata:\n labels:\n name: cilium-olm\n spec:\n containers:\n - command:\n - /usr/local/bin/helm-operator\n - run\n - --watches-file=watches.yaml\n - --enable-leader-election\n - --leader-election-id=cilium-olm\n - --zap-devel\n env:\n - name: WATCH_NAMESPACE\n valueFrom:\n fieldRef:\n fieldPath: metadata.namespace\n image: registry.connect.redhat.com/isovalent/cilium-olm@sha256:26f1ed31c8f0600fcea498116e7dbea157a8704989f762e22e8038b8ea364dce\n name: operator\n ports:\n - containerPort: 9443\n name: https\n protocol: TCP\n resources:\n limits:\n cpu: 100m\n memory: 150Mi\n requests:\n cpu: 100m\n memory: 150Mi\n volumeMounts:\n - mountPath: /tmp\n name: tmp\n hostNetwork: true\n serviceAccount: cilium-olm\n terminationGracePeriodSeconds: 10\n tolerations:\n - operator: Exists\n volumes:\n - emptyDir: {}\n name: tmp\n permissions:\n - rules:\n - apiGroups:\n - \"\"\n resources:\n - configmaps\n verbs:\n - get\n - list\n - watch\n - create\n - update\n - patch\n - delete\n - apiGroups:\n - \"\"\n resources:\n - events\n verbs:\n - create\n - apiGroups:\n - \"\"\n resources:\n - namespaces\n verbs:\n - get\n - apiGroups:\n - cilium.io\n resources:\n - ciliumconfigs\n - ciliumconfigs/status\n verbs:\n - list\n - apiGroups:\n - cilium.io\n resources:\n - ciliumconfigs\n - ciliumconfigs/status\n - ciliumconfigs/finalizers\n verbs:\n - get\n - patch\n - update\n - watch\n - list\n - delete\n - apiGroups:\n - \"\"\n resources:\n - events\n verbs:\n - create\n - apiGroups:\n - \"\"\n resources:\n - secrets\n verbs:\n - '*'\n - apiGroups:\n - \"\"\n resources:\n - serviceaccounts\n - configmaps\n - secrets\n - services\n verbs:\n - '*'\n - apiGroups:\n - apps\n resources:\n - deployments\n - daemonsets\n verbs:\n - '*'\n serviceAccountName: cilium-olm\n strategy: deployment\n installModes:\n - supported: true\n type: OwnNamespace\n - supported: true\n type: SingleNamespace\n - supported: false\n type: MultiNamespace\n - supported: false\n type: AllNamespaces\n keywords:\n - networking\n - security\n - observability\n - eBPF\n links:\n - name: Cilium Homepage\n url: https://cilium.io/\n maintainers:\n - email: [email protected]\n name: Cilium\n maturity: stable\n provider:\n name: Isovalent\n version: 1.10.1+xdcd9835\n relatedImages:\n - name: operator\n image: registry.connect.redhat.com/isovalent/cilium-olm@sha256:26f1ed31c8f0600fcea498116e7dbea157a8704989f762e22e8038b8ea364dce"}, "changed": false}
2021-06-25 12:57:42,076 p=23 u=default n=ansible | TASK [parse_operator_bundle : Determine and set fact for operator specific information - name, pod name, container name and capabilities] ***
2021-06-25 12:57:42,372 p=23 u=default n=ansible | ok: [localhost] => {"ansible_facts": {"current_csv": "cilium.v1.10.1-xdcd9835", "operator_capabilities": "Basic Install", "operator_container_name": "operator", "operator_pod_name": "cilium-olm"}, "changed": false}
2021-06-25 12:57:42,374 p=23 u=default n=ansible | TASK [parse_operator_bundle : Determine operator_allnamespaces_support] ********
2021-06-25 12:57:42,543 p=23 u=default n=ansible | ok: [localhost] => {"ansible_facts": {"operator_allnamespaces_support": [false]}, "changed": false}
2021-06-25 12:57:42,546 p=23 u=default n=ansible | TASK [parse_operator_bundle : Determine operator_ownnamespace_support] *********
2021-06-25 12:57:42,714 p=23 u=default n=ansible | ok: [localhost] => {"ansible_facts": {"operator_ownnamespace_support": [true]}, "changed": false}
2021-06-25 12:57:42,717 p=23 u=default n=ansible | TASK [parse_operator_bundle : Determine operator_singlenamespace_support] ******
2021-06-25 12:57:42,888 p=23 u=default n=ansible | ok: [localhost] => {"ansible_facts": {"operator_singlenamespace_support": [true]}, "changed": false}
2021-06-25 12:57:42,890 p=23 u=default n=ansible | TASK [parse_operator_bundle : Determine operator_multinamespace_support] *******
2021-06-25 12:57:43,060 p=23 u=default n=ansible | ok: [localhost] => {"ansible_facts": {"operator_multinamespace_support": [false]}, "changed": false}
2021-06-25 12:57:43,062 p=23 u=default n=ansible | TASK [parse_operator_bundle : Set boolean value for different types of namespaces] ***
2021-06-25 12:57:43,194 p=23 u=default n=ansible | ok: [localhost] => {"ansible_facts": {"operator_allnamespaces_support": false, "operator_multinamespace_support": false, "operator_ownnamespace_support": true, "operator_singlenamespace_support": true}, "changed": false}
2021-06-25 12:57:43,200 p=23 u=default n=ansible | TASK [parse_operator_bundle : Output all collected data to a yaml file in work dir] ***
2021-06-25 12:57:43,685 p=23 u=default n=ansible | changed: [localhost] => {"changed": true, "checksum": "751c10af7d5b70aaa942659244282bfbeefac115", "dest": "/home/jenkins/agent/workspace/cvp-isv-operator-bundle-image-validation-test/parsed_operator_data.yml", "gid": 0, "group": "root", "md5sum": "5bbf286eedeb70fdd5e35af94b0c55d6", "mode": "0644", "owner": "default", "size": 644, "src": "/home/jenkins/agent/.ansible/tmp/ansible-tmp-1624625863.3402283-347-253092958666172/source", "state": "file", "uid": 1001680000}
2021-06-25 12:57:43,687 p=23 u=default n=ansible | TASK [parse_operator_bundle : Sanity check the operator bundle's information] ***
2021-06-25 12:57:43,822 p=23 u=default n=ansible | included: /home/jenkins/agent/workspace/cvp-isv-operator-bundle-image-validation-test/operators/config/ansible/roles/parse_operator_bundle/tasks/bundle_sanity_checks.yml for localhost
2021-06-25 12:57:43,834 p=23 u=default n=ansible | TASK [parse_operator_bundle : Read the variables from annotations.yaml] ********
2021-06-25 12:57:43,991 p=23 u=default n=ansible | ok: [localhost] => {"ansible_facts": {"annotations_vars": {"annotations": {"operators.operatorframework.io.bundle.channel.default.v1": "stable", "operators.operatorframework.io.bundle.channels.v1": "stable", "operators.operatorframework.io.bundle.manifests.v1": "manifests/", "operators.operatorframework.io.bundle.mediatype.v1": "registry+v1", "operators.operatorframework.io.bundle.metadata.v1": "metadata/", "operators.operatorframework.io.bundle.package.v1": "cilium", "operators.operatorframework.io.metrics.builder": "operator-sdk-v1.0.1", "operators.operatorframework.io.metrics.mediatype.v1": "metrics+v1", "operators.operatorframework.io.metrics.project_layout": "helm.sdk.operatorframework.io/v1", "operators.operatorframework.io.test.config.v1": "tests/scorecard/", "operators.operatorframework.io.test.mediatype.v1": "scorecard+v1"}}}, "ansible_included_var_files": ["/home/jenkins/agent/test-operator/metadata/annotations.yaml"], "changed": false}
2021-06-25 12:57:43,994 p=23 u=default n=ansible | TASK [parse_operator_bundle : shell] *******************************************
2021-06-25 12:57:44,145 p=23 u=default n=ansible | skipping: [localhost] => {"changed": false, "skip_reason": "Conditional result was False"}
2021-06-25 12:57:44,147 p=23 u=default n=ansible | TASK [parse_operator_bundle : Debug] *******************************************
2021-06-25 12:57:44,301 p=23 u=default n=ansible | skipping: [localhost] => {}
2021-06-25 12:57:44,303 p=23 u=default n=ansible | TASK [parse_operator_bundle : Set facts] ***************************************
2021-06-25 12:57:44,455 p=23 u=default n=ansible | skipping: [localhost] => {"changed": false, "skip_reason": "Conditional result was False"}
2021-06-25 12:57:44,458 p=23 u=default n=ansible | TASK [parse_operator_bundle : debug] *******************************************
2021-06-25 12:57:44,609 p=23 u=default n=ansible | ok: [localhost] => {
"skopeo_inspect_json.Labels": {
"com.redhat.delivery.backport": "true",
"com.redhat.delivery.operator.bundle": "true",
"com.redhat.iib.pinned": "true",
"com.redhat.openshift.versions": "v4.5,v4.6,v4.7",
"io.buildah.version": "1.16.7",
"operators.operatorframework.io.bundle.channel.default.v1": "stable",
"operators.operatorframework.io.bundle.channels.v1": "stable",
"operators.operatorframework.io.bundle.manifests.v1": "manifests/",
"operators.operatorframework.io.bundle.mediatype.v1": "registry+v1",
"operators.operatorframework.io.bundle.metadata.v1": "metadata/",
"operators.operatorframework.io.bundle.package.v1": "cilium",
"operators.operatorframework.io.metrics.builder": "operator-sdk-v1.0.1",
"operators.operatorframework.io.metrics.mediatype.v1": "metrics+v1",
"operators.operatorframework.io.metrics.project_layout": "helm.sdk.operatorframework.io/v1"
}
}
2021-06-25 12:57:44,611 p=23 u=default n=ansible | TASK [parse_operator_bundle : debug] *******************************************
2021-06-25 12:57:44,762 p=23 u=default n=ansible | ok: [localhost] => {
"annotations_vars.annotations": {
"operators.operatorframework.io.bundle.channel.default.v1": "stable",
"operators.operatorframework.io.bundle.channels.v1": "stable",
"operators.operatorframework.io.bundle.manifests.v1": "manifests/",
"operators.operatorframework.io.bundle.mediatype.v1": "registry+v1",
"operators.operatorframework.io.bundle.metadata.v1": "metadata/",
"operators.operatorframework.io.bundle.package.v1": "cilium",
"operators.operatorframework.io.metrics.builder": "operator-sdk-v1.0.1",
"operators.operatorframework.io.metrics.mediatype.v1": "metrics+v1",
"operators.operatorframework.io.metrics.project_layout": "helm.sdk.operatorframework.io/v1",
"operators.operatorframework.io.test.config.v1": "tests/scorecard/",
"operators.operatorframework.io.test.mediatype.v1": "scorecard+v1"
}
}
2021-06-25 12:57:44,765 p=23 u=default n=ansible | TASK [parse_operator_bundle : Check if the operators.operatorframework.io.bundle.channels.v1 from annotation.yaml matches the bundle image label] ***
2021-06-25 12:57:44,917 p=23 u=default n=ansible | skipping: [localhost] => {"changed": false, "skip_reason": "Conditional result was False"}
2021-06-25 12:57:44,919 p=23 u=default n=ansible | TASK [parse_operator_bundle : Check if the operators.operatorframework.io.bundle.manifests.v1 from annotation.yaml matches the bundle image label] ***
2021-06-25 12:57:45,072 p=23 u=default n=ansible | skipping: [localhost] => {"changed": false, "skip_reason": "Conditional result was False"}
2021-06-25 12:57:45,074 p=23 u=default n=ansible | TASK [parse_operator_bundle : Check if the operators.operatorframework.io.bundle.mediatype.v1 from annotation.yaml matches the bundle image label] ***
2021-06-25 12:57:45,225 p=23 u=default n=ansible | skipping: [localhost] => {"changed": false, "skip_reason": "Conditional result was False"}
2021-06-25 12:57:45,227 p=23 u=default n=ansible | TASK [parse_operator_bundle : Check if the operators.operatorframework.io.bundle.mediatype.v1 is set to the expected value] ***
2021-06-25 12:57:45,376 p=23 u=default n=ansible | skipping: [localhost] => {"changed": false, "skip_reason": "Conditional result was False"}
2021-06-25 12:57:45,379 p=23 u=default n=ansible | TASK [parse_operator_bundle : Check if the operators.operatorframework.io.bundle.metadata.v1 from annotation.yaml matches the bundle image label] ***
2021-06-25 12:57:45,528 p=23 u=default n=ansible | skipping: [localhost] => {"changed": false, "skip_reason": "Conditional result was False"}
2021-06-25 12:57:45,530 p=23 u=default n=ansible | TASK [parse_operator_bundle : Check if the operators.operatorframework.io.bundle.package.v1 from annotation.yaml matches the bundle image label] ***
2021-06-25 12:57:45,676 p=23 u=default n=ansible | skipping: [localhost] => {"changed": false, "skip_reason": "Conditional result was False"}
2021-06-25 12:57:45,677 p=23 u=default n=ansible | PLAY RECAP *********************************************************************
2021-06-25 12:57:45,677 p=23 u=default n=ansible | localhost : ok=36 changed=9 unreachable=0 failed=0 skipped=11 rescued=0 ignored=0
-------------------
Execution Reference:
-> /cvp/cvp-isv-operator-bundle-image-validation-test/certified-ospid-e31ac831-7e72-42bb-baf9-f392ef7ea622-603a0723-d1ac-4af3-8216-20b46833dd67/603a0723-d1ac-4af3-8216-20b46833dd67/