Comments (5)
Yes, Today TCP apps will see the client ip as that of the last proxy rather than the actual downstream client ip. In HTTP apps, the proxy protocol is just that of injecting XFF headers which we do.
For TCP, the proxy protocol requires the server to handle a custom TCP header on the very beginning of the connection. This as @JennyLawrance mentioned requires opt-in from the application as it’s no longer just raw TCP connection.
However, since we have envoy both on edge and as a sidecar, the proxy protocol can happen between the edge proxy/loadbalancer and the sidecar helper, then the sidecar can set the correct client ip and strip that packet out keeping it transparent to the application. https://www.envoyproxy.io/docs/envoy/latest/configuration/listeners/listener_filters/original_src_filter
We don’t have this today though.
from azure-container-apps.
This is a very interesting ask. Implementing Proxy protocol as suggested also implies that the user will also code their app to handle the proxy header, right? I'm not clear on how many standard webservers support the proxy protocol on the server side.
An alternative idea to meet your requirements will be for ACA to provide first class Logging for TCP connections. ACA already supports IP restriction feature, so the deny-list is already covered.
Will this approach meet your requirements, or am I missing something?
from azure-container-apps.
@marshallr12 for non-HTTP TCP connections, how is the client IP normally presented to your app (assuming there's some kind of proxy/middleware in the flow)?
from azure-container-apps.
The app is an SMTP server written in .NET using a System.Net.Socket.TcpListener which accepts connections and returns a System.Net.Socket.TcpClient. The client is then interrogated for the client IP, which is then used to trigger application-level rules to accept or reject the connection. This all works fine when hosting in a VM with a public IP. There are potentially other related apps I'd like to containerize (POP, IMAP, Mail agent).
In containers, the client IP is always an internal VNET address rather than the original external client IP. So that IP will always be internal no matter the initiating external client IP address, and would not be useful to any TCP-based application. From what I read, the proxy in ACA is Envoy, which supports the proxy protocol when configured properly and preserves the original IP (or provides the means to access it).
If you have an SMTP application which exposes a port to the public, you have to dynamically identify bad actor IP addresses for clients / spammers. This is done with a combination of firewall-like behaviors (too many connections, too many failed login attempts, etc.), but also by querying services like SpamHaus and providing the client IP to those services.
You also have to be able to identify whether the connecting MX server is authoritative for the domain associated with the sender of an email. This is done by providing the client IP address (which would belong to the connecting MX server) to a Sender Protection Framework API (SPF). Essentially, SPF uses DNS to see if the domain of the email sender corresponds to a known MX server for that domain, based on the client IP Address (i.e., the connecting MX server). SPF allows you to prevent spoofing of email senders.
A deny-list in this scenario has to be built dynamically over time like an application-layer firewall. So it is not the sort of deny list where an admin would statically configure deny-lists and white-lists.
from azure-container-apps.
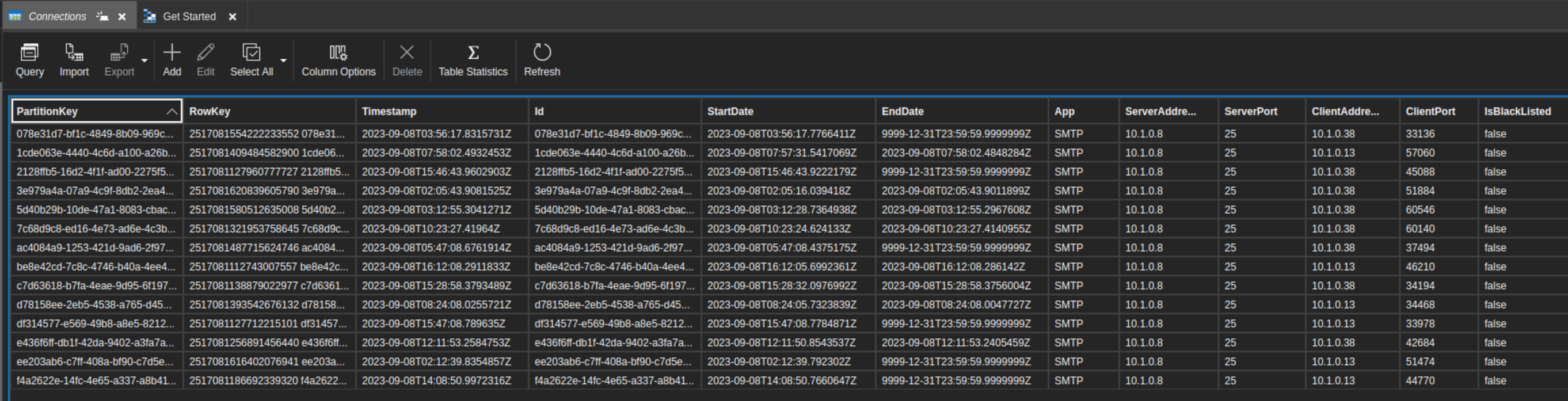
This image shows my connection log (which uses table storage) since I've containerized my mail server. All of these connections represent spam (or hacker) attempts. However, the client address reflects the proxy, and not the original connecting address. The "App" column would be any of SMTP, SMTPS, POP, POPS, IMAP, etc. as there are multiple email-related application servers involved.
from azure-container-apps.
Related Issues (20)
- Startup probe not working as expected HOT 5
- Consumption vs Consumption on Dedicated Plan structure memory HOT 7
- Feature Request: expose mc_ resource group from managed environment api HOT 2
- Multiple values in CRON expression for jobs no longer works HOT 4
- Feature Request: Link Azure Container Registry to Container App Environment HOT 4
- Roadmap: Import a certificate from Key Vault HOT 1
- Container jobs cannot connect to container apps in the same environment HOT 3
- Container app gets killed in the middle of the execution.
- Issue with Azure Container Apps (ACA) Limitation on Opening Multiple Ports HOT 2
- InvalidParameterValueInContainerTemplate - deploy quickstart image in portal with VNet HOT 1
- Container App Jobs with Azure Firewall - undocumented/broad rules HOT 1
- Internal Server Error when trying to deploy Container Apps Job using DevOps Pipelines with task AzureCLI@2 HOT 3
- GitHub Actions runners and Azure Pipelines agents with Azure Container Apps not working HOT 1
- Examine why ephemeral storage fills up HOT 2
- CosmosDB request timeouts in vNet deployed "Workload profiles" environment HOT 3
- Nginx container app + Azure File Share - can't read/write HOT 3
- Feature Request: Basic Load Balancer HOT 1
- Feature Request: Ability to enable/disable apps and jobs HOT 4
- Container apps jobs environment variables fail validation HOT 6
Recommend Projects
-
 React
React
A declarative, efficient, and flexible JavaScript library for building user interfaces.
-
Vue.js
🖖 Vue.js is a progressive, incrementally-adoptable JavaScript framework for building UI on the web.
-
 Typescript
Typescript
TypeScript is a superset of JavaScript that compiles to clean JavaScript output.
-
TensorFlow
An Open Source Machine Learning Framework for Everyone
-
Django
The Web framework for perfectionists with deadlines.
-
Laravel
A PHP framework for web artisans
-
D3
Bring data to life with SVG, Canvas and HTML. 📊📈🎉
-
Recommend Topics
-
javascript
JavaScript (JS) is a lightweight interpreted programming language with first-class functions.
-
web
Some thing interesting about web. New door for the world.
-
server
A server is a program made to process requests and deliver data to clients.
-
Machine learning
Machine learning is a way of modeling and interpreting data that allows a piece of software to respond intelligently.
-
Visualization
Some thing interesting about visualization, use data art
-
Game
Some thing interesting about game, make everyone happy.
Recommend Org
-
Facebook
We are working to build community through open source technology. NB: members must have two-factor auth.
-
Microsoft
Open source projects and samples from Microsoft.
-
Google
Google ❤️ Open Source for everyone.
-
Alibaba
Alibaba Open Source for everyone
-
D3
Data-Driven Documents codes.
-
Tencent
China tencent open source team.

from azure-container-apps.